Multi-cloud Data Security for resilient cloud environments
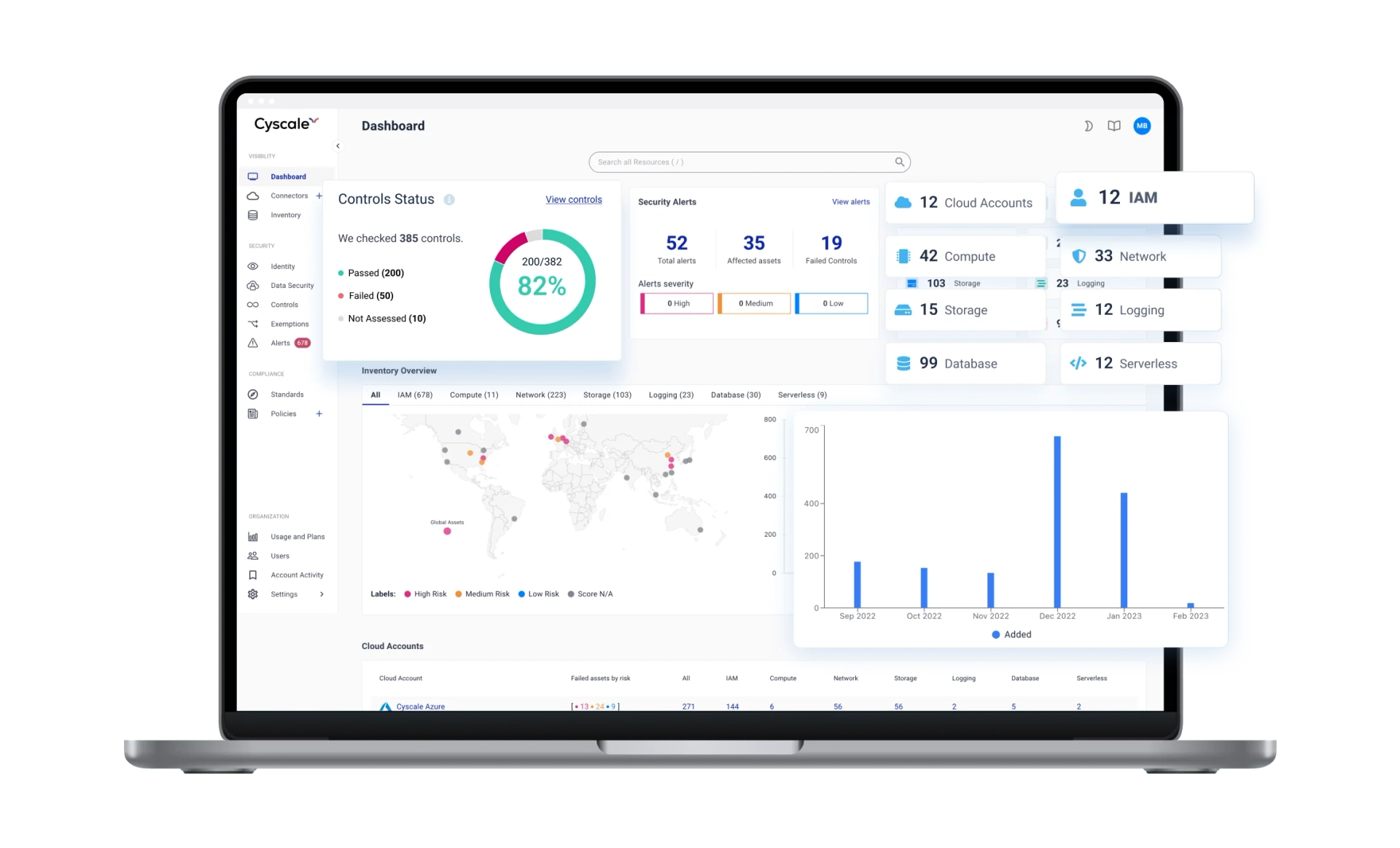
Stuck playing catch-up with data security, with no breathing space for projects that move the needle? It's time for a change of pace. Give your engineers clarity and accuracy - use the Cyscale Cloud Platform to turn cloud data security into a manageable routine. Keep tabs on your fast-growing cloud inventory with real-time automated data discovery and classification, compliance scans on autopilot and a fully auditable evidence trail. And that's just a taste!
Agentlessno installation, just instant value
Serverlesscloud-native with zero performance penalty
Context-awaregoes beyond list-based inventories
Comprehensiveextensive multi-cloud range & flexibility
Discover & map data repositories across multi-cloud environments
When you're growing fast, it's easy to lose track of your cloud assets. But that comes at a cost, both in terms of $$$ and compliance issues. Liquidate your data security debt with the Cyscale Cloud Platform. Bring all your entities under one roof with comprehensive asset inventory and management - as soon as you log in. Expand visibility to cover your entire cloud infrastructure, across cloud service providers. It's much easier to meet data security requirements when you know exactly where all your cloud assets are.
We support
DATABASES
- AWS RDS
- AWS DynamoDB
- AWS Aurora
- GCP Cloud SQL
- GCP Spanner
- Azure SQL Database
- Azure CosmosDB
- Cloud-native MySQL
- Cloud-native PostgreSQL
CLOUD / NETWORK STORAGE
- AWS S3 Bucket
- AWS EBS
- AWS EFS
- GCP Disk
- GCP Cloud Storage
- GCP Cloud Filestore
- Azure Disk
- Azure Blob Storage
- Azure Files
BIG DATA/DATA LAKES
- AWS Lake Formation
- AWS Redshift
- GCP BigQuery
- Azure Synapse
- Azure Data Lake Storage
- Snowflake (soon)
- Databricks (soon)
- -
- -
CODE / IP REPOSITORIES
- GitHub
- Gitlab
- BitBucket (soon)
- Atlassian Jira & Confluence
- Amazon AWS Code Repository
- Google Cloud Source
- Microsoft Azure Repos
- -
- -
Don't see your Data Repo?
Prioritize security-critical data repos to avoid exposure & breaches
With all cloud assets mapped out, IT and security teams can build a clear roadmap to ensure data protection against external threats (unauthorized access, cyber threats, etc.) and internal security risks (insider threats, vulnerabilities and human error). We make it even easier to triage security tasks by automatically identifying which cloud assets hold critical data, who uses it and how. The Cyscale Cloud Platform also automates the detection of security policy violations and risky behavior that open up your cloud computing environment to the risk of data loss. Avoid losing trade secrets and intellectual property that future innovation and profitability depend on with robust data privacy security solutions.
Visualize access, permissions & relationships between your data and other digital assets
Make your cloud assets secure and compliant based on the full context they operate in.
Our proprietary Security Knowledge Graph™ makes it easy to see who has access to individual assets and how they interact with one another. A structure of micrographs represents these complex relationships in a visual, intuitive format anyone can navigate with zero training.
No more shadow access, excessive permissions and other cybersecurity issues cross-cloud interactions create. Know who's accessing your sensitive data and what they're doing with it.
With Cyscale, you understand how to implement strong IAM (Identity and Access Management) policies to keep security threats away using access control and authentication rules.
Data Security Top 10
Cyscale is built by the authors of the OWASP Data Security Top 10 standard that helps security, IT, and compliance specialists ensure critical data is safe against unauthorized exposure, data breaches, malware, and accidental or malicious misuse.
Comprehensive, blazing-fast classification that closes security gaps
Our Cloud Platform gives you the visibility that goes deep into every layer of your cloud infrastructures.
Financial customer data
- Credit card numbers
- IBANs
- Balance sheets
- Cash flow statements
Medical information
- Electronic health records
- Medical insurance data
- Clinical trials data
- Disease registries
Intelectual property
- Patents
- Trademarks
- Copyright-protected data access
- Trade secrets
Personally Identifiable Information
- Social Security Numbers
- National IDs
- Driver's license details
- Home addresses
Manage your compliance obligations with the 500+ ready-to-use security controls and policies you can apply and monitor through automatic, ongoing checks for misconfigurations. Get alerts whenever your most valuable cloud assets drift from your initial configuration. We help you meet compliance requirements for GDPR, HIPAA, NIST, PCI-DSS, and many others.
From data encryption and key management to firewalls, whether it’s in the public cloud, multi-cloud, or hybrid cloud, we help you take the right decisions and take appropriate security measures to keep your data safe.
RECOMMENDED ARTICLES
Cloud Data Security
The Complete Guide
to Cloud Storage Misconfigurations
This guide helps CIOs, CISOs and security staff to understand the risk & dangers of data security breaches and the importance of a secure cloud storage infrastructure.