What is the difference between CNAPP and CSPM?
CSPM focuses on cloud misconfiguration detection and compliance posture. CNAPP is broader and combines CSPM with runtime, vulnerability, identity, and data security controls in one platform.
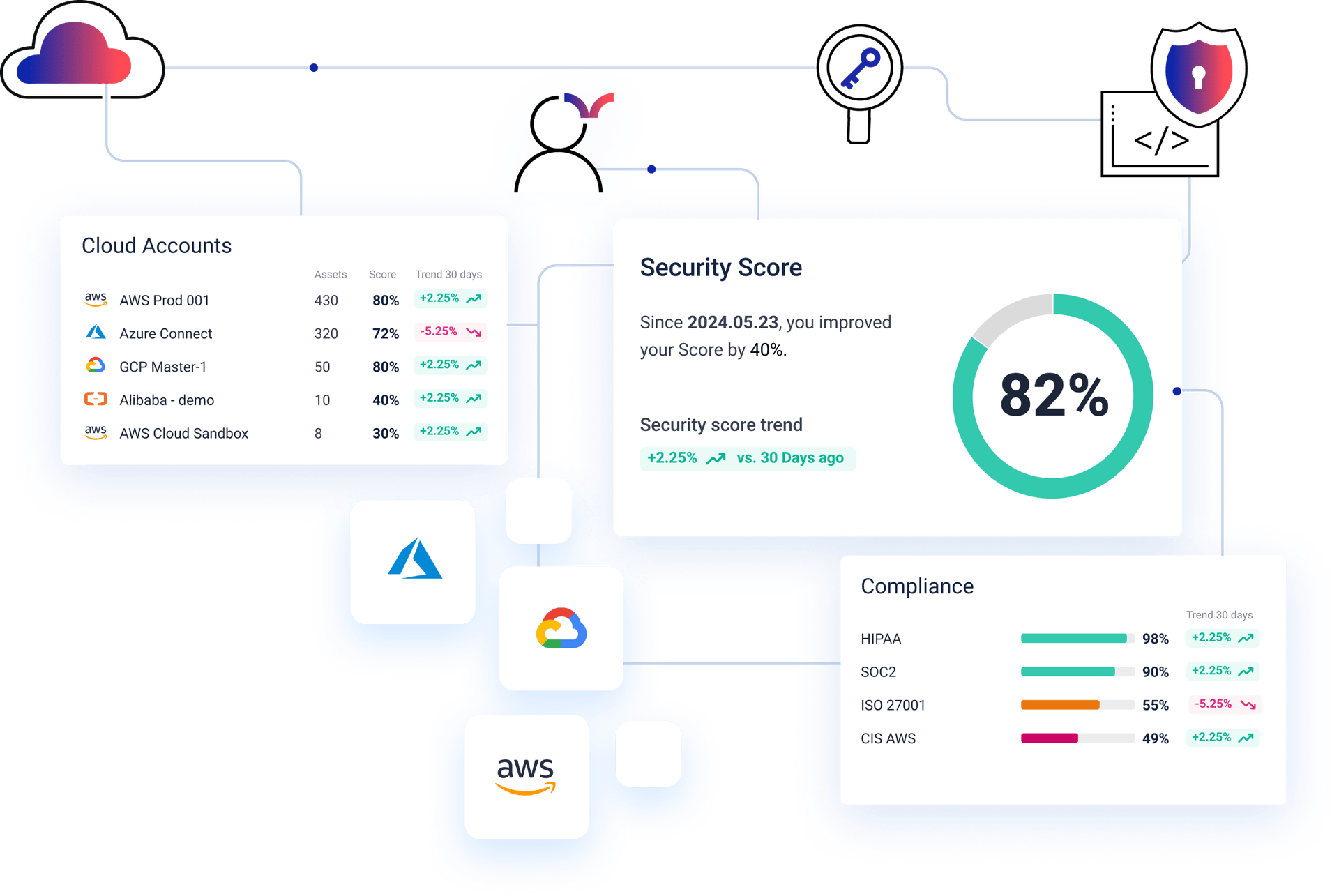
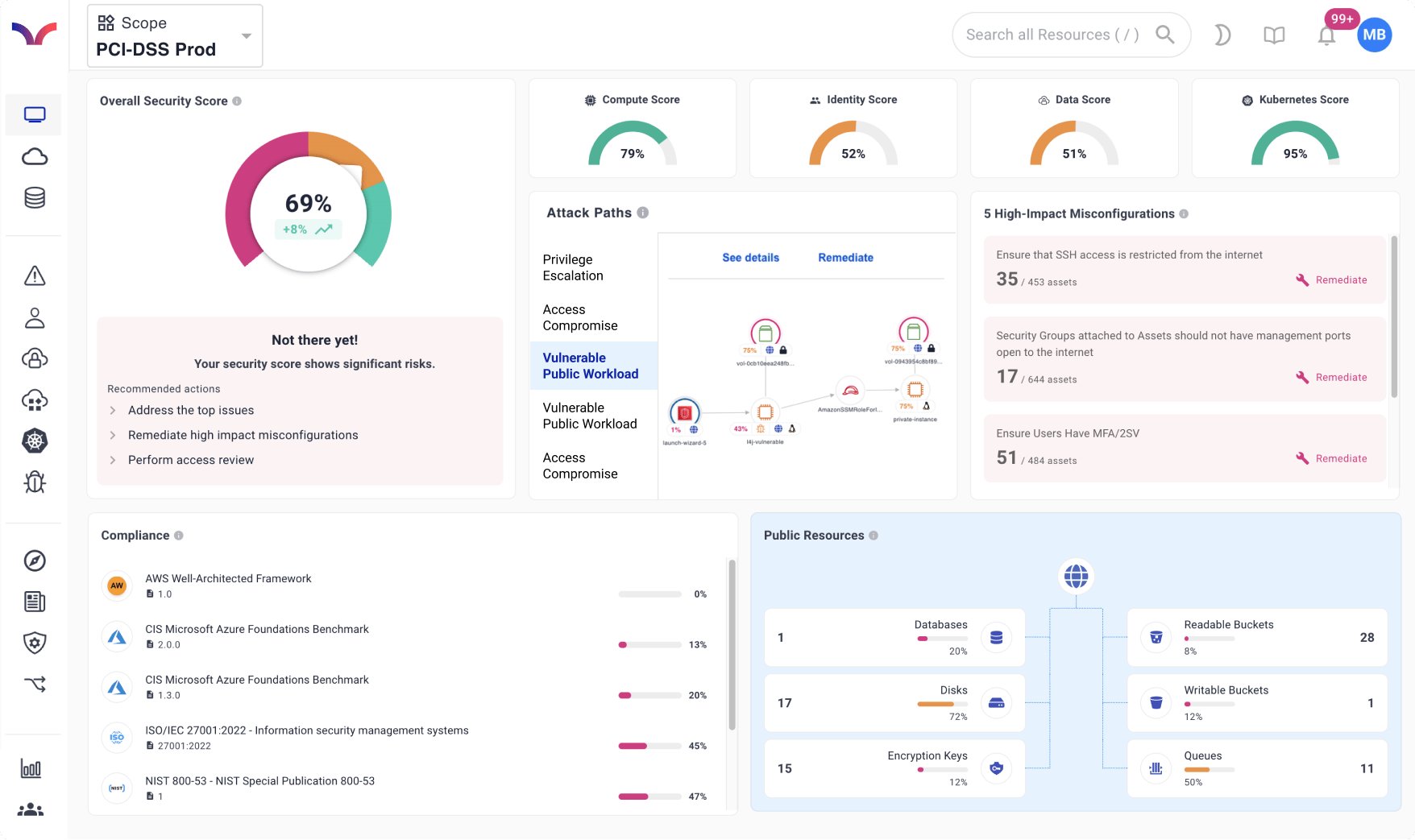
Detect the cloud risks that matter most and guide teams to faster remediation from a single unified platform.
4.9
Cyscale Solutions
Detect, contextualize & remediate misconfigurations in your unique cloud environment
S2E Italy, the largest Italian digital transformation and cybersecurity consulting company, has build an entire misconfigurations and vulnerabilities detection system on top of Cyscale.
Stop switching between disconnected tools. Cyscale helps security, platform, and compliance teams identify what matters most and remediate cloud risk faster.
A DEEPER UNDERSTANDING
OF YOUR UNIQUE CLOUD RISK
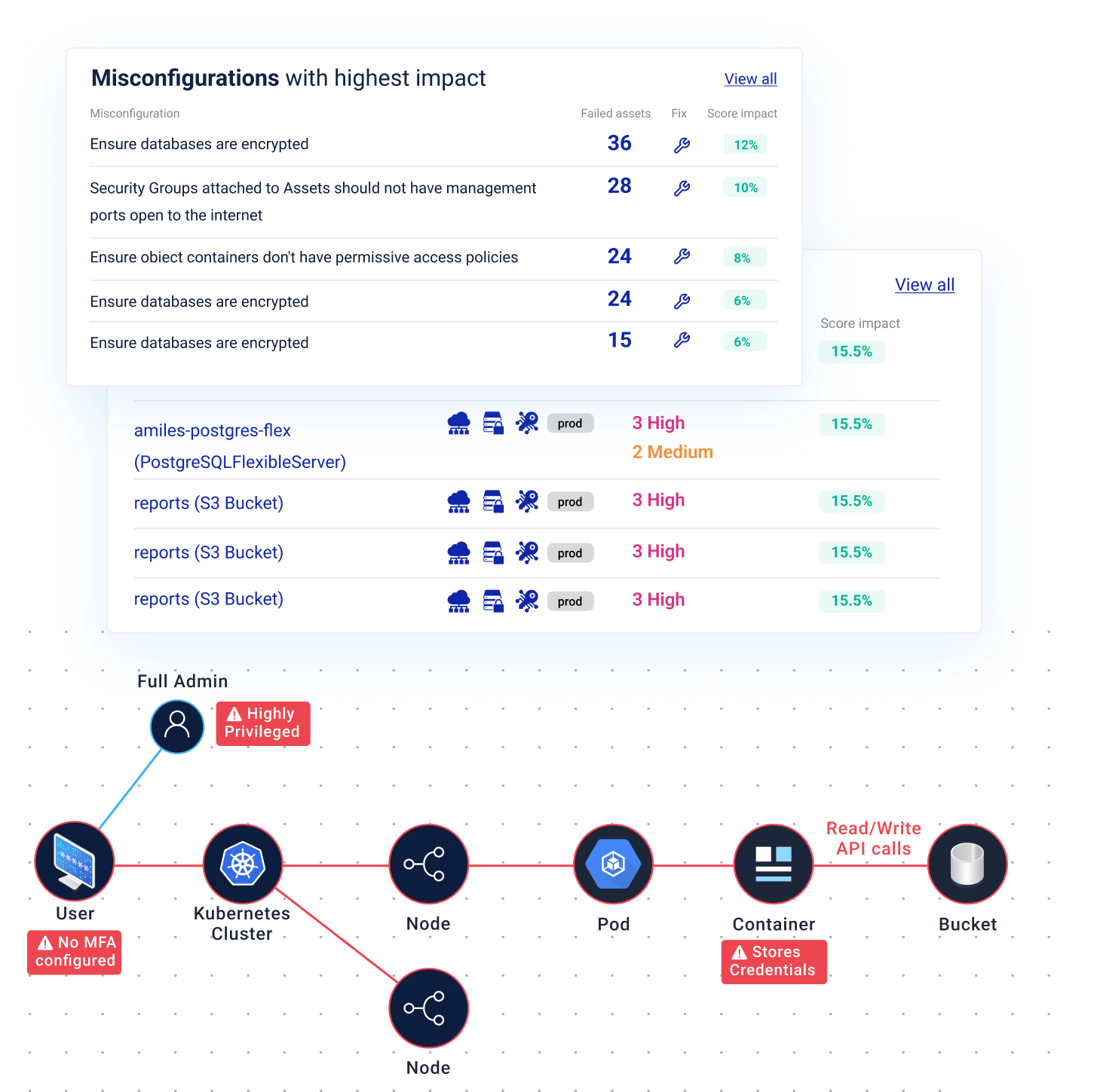
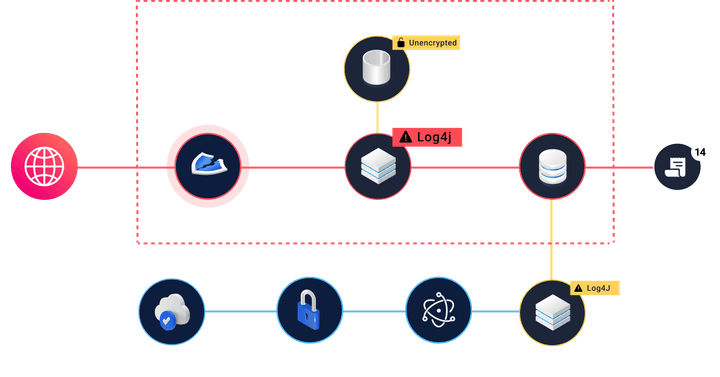
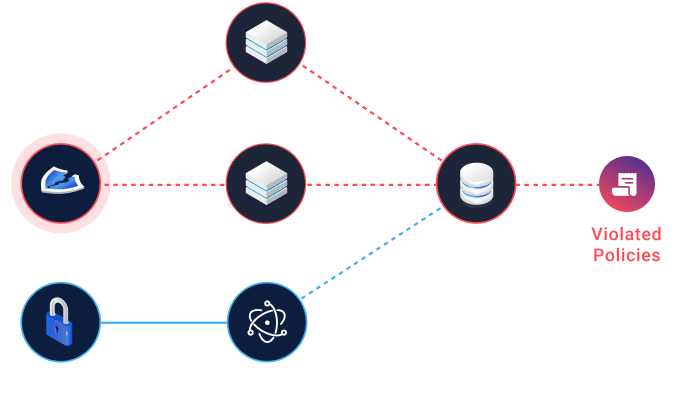
An unpatched virtual machine running an app with the devastating Log4j vulnerability is close to harmless in a private network. However, a server running the same vulnerable cloud app while being exposed to the internet, and having read or write access to a production datastore presents an urgent risk.
Don't waste time chasing false positives. Context enables you to immediately see what you need to prioritize on your cloud security roadmap.
CLOUD SECURITY IS CRITICAL
BUT IT SHOULDN'T BE COMPLEX
Cyscale is an agentless cloud-native application protection platform (CNAPP) that helps protect your organization against data breaches and other types of modern threats in the public cloud.
AUTOMATED CLOUD SECURITY
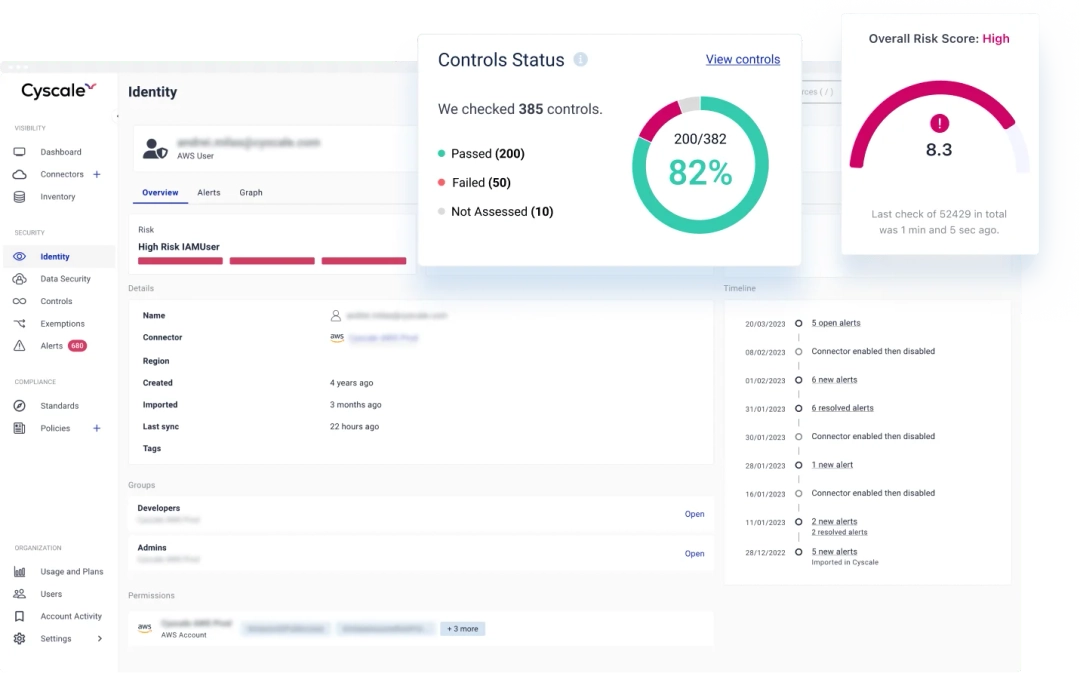
Cloud security posture management with identity and data centric views.
Unlimited protected assets.
Amazon Web Services, Google Cloud, Microsoft Azure, Alibaba Cloud, Okta, Github and more...
to detect cloud security drifts
Modern cloud teams need more than isolated scanners. Cyscale combines cloud posture management, vulnerability management, compliance, and identity risk context so teams can remediate what matters first.
Explore the dedicated pages for CSPM, CNAPP, and cloud vulnerability management.
Get fast onboarding, clear remediation guidance, and unified visibility across multi-cloud environments without juggling multiple cloud security tools.
CSPM focuses on cloud misconfiguration detection and compliance posture. CNAPP is broader and combines CSPM with runtime, vulnerability, identity, and data security controls in one platform.
Cyscale correlates vulnerabilities with identity permissions, internet exposure, data sensitivity, and attack paths so teams can fix the highest-impact cloud risks first.
Yes. Cyscale is built for agentless onboarding so teams can connect cloud accounts quickly and start seeing posture, vulnerability, and compliance insights in minutes.
Cyscale supports AWS, Microsoft Azure, Google Cloud, and Alibaba Cloud so security teams can manage multi-cloud posture from a single CNAPP experience.
Cloud Security Wiki
Security buyers and practitioners should evaluate cloud security platforms based on operational execution, not just detection depth. The right platform reduces triage load, aligns engineering and security teams, and improves executive confidence in risk reduction.
CNAPP Guide
Framework to evaluate unified code-to-cloud security operations.
CSPM Guide
How to prioritize and remediate posture drift in multi-cloud environments.
Cloud Vulnerability Management Guide
Operational model for SBOM-based scanning and risk-based remediation.
Cyscale vs Wiz
Comparison focused on operational clarity, speed, and pricing fit.
Cyscale vs Orca Security
Comparison focused on actionability from findings to fixed risk.
OUR BLOG
Cyscale Security Wiki
Explore connected guidance, implementation notes, and decision frameworks that link directly to this topic and related Cyscale workflows.
CNAPP combines cloud posture, vulnerability management, identity context, and compliance workflows into one operating model so teams can fix risk faster.
CSPM continuously identifies cloud misconfigurations and policy violations across AWS, Azure, and Google Cloud to reduce breach exposure and audit risk.
Cloud vulnerability management must connect software findings with runtime context so teams can prioritize exploitable and exposed issues first.
Cloud compliance programs are strongest when control status is monitored continuously and linked to concrete remediation workflows.
Stay connected
Receive new blog posts and product updates from Cyscale
By clicking Subscribe, I agree to Cyscale’s Privacy Policy
© 2026 Cyscale Limited