Use the Cyscale Cloud Platform to

Solve pressing WFH security issues
Limited cloud usage visibility
Misconfigured cloud controls
Overly permissive rights
Additional risks employee workarounds introduce
+ plenty others
Safely support remote work
Built-in Remote Work policy
Multi-cloud security controls
Real-time access evidence collection
In-depth scans of sensitive data across cloud storage, tools & repos
+ loads more!
Protect remote teams & their workEnsure secure remote access from day one
Onboard remote team members fast and provide the secure setup they need to be productive with substantially less effort. Use our Cloud Platform to correctly configure permissions and avoid errors that expose your environment to additional vulnerabilities. We provide a ready-to-use Remote Work policy that includes safety provisions for equipment (including mobile and BYOD), communications, and security layers. Keep the risks employee workarounds introduce to a minimum and make sure workflows stay compliant during digital transformation projects.
See every employee's access footprint in full
Use Cyscale to automatically document access for all employees to every cloud entity in your organization. Cloud storage, collaboration tools, data repos - you name it, we scan it and give you the full picture in real time. Our Cloud Platform runs ongoing Identity and Access Management checks, building an auditable trail of compliance data in the process. You can also use it to manage permissions and revoke them as you need. From logical security to account management and beyond, we constantly audit your cloud environments and notify you when assets drift from compliance.
Keep intellectual property safe across clouds
Avoid inadvertent data leaks that expose business-critical trade secrets, patents, and other copyright-protected data. Our in-depth sensitive data scanning engine identifies intellectual property spread across cloud storage, collaboration tools, and cloud source repositories. Automating this essential task for your multi-cloud environment gives you more time to solve security issues that put confidential data at risk.
Supercharge cloud security for WFHStay compliant with automated checks
Always know who has access to which cloud resources, how they are using them, and why. Keep track of cloud users' activity across your entire range of cloud accounts, SaaS platforms, and cloud assets with Cyscale. Our self-generated Security Knowledge Graph™ provides a map of cross-cloud interactions anyone can navigate to get insights and context. That's why IT, HR, and other teams tasked with remote work security and productivity rely on us to achieve, prove, and maintain compliance with ISO 27001, SOC 2, and other standards.
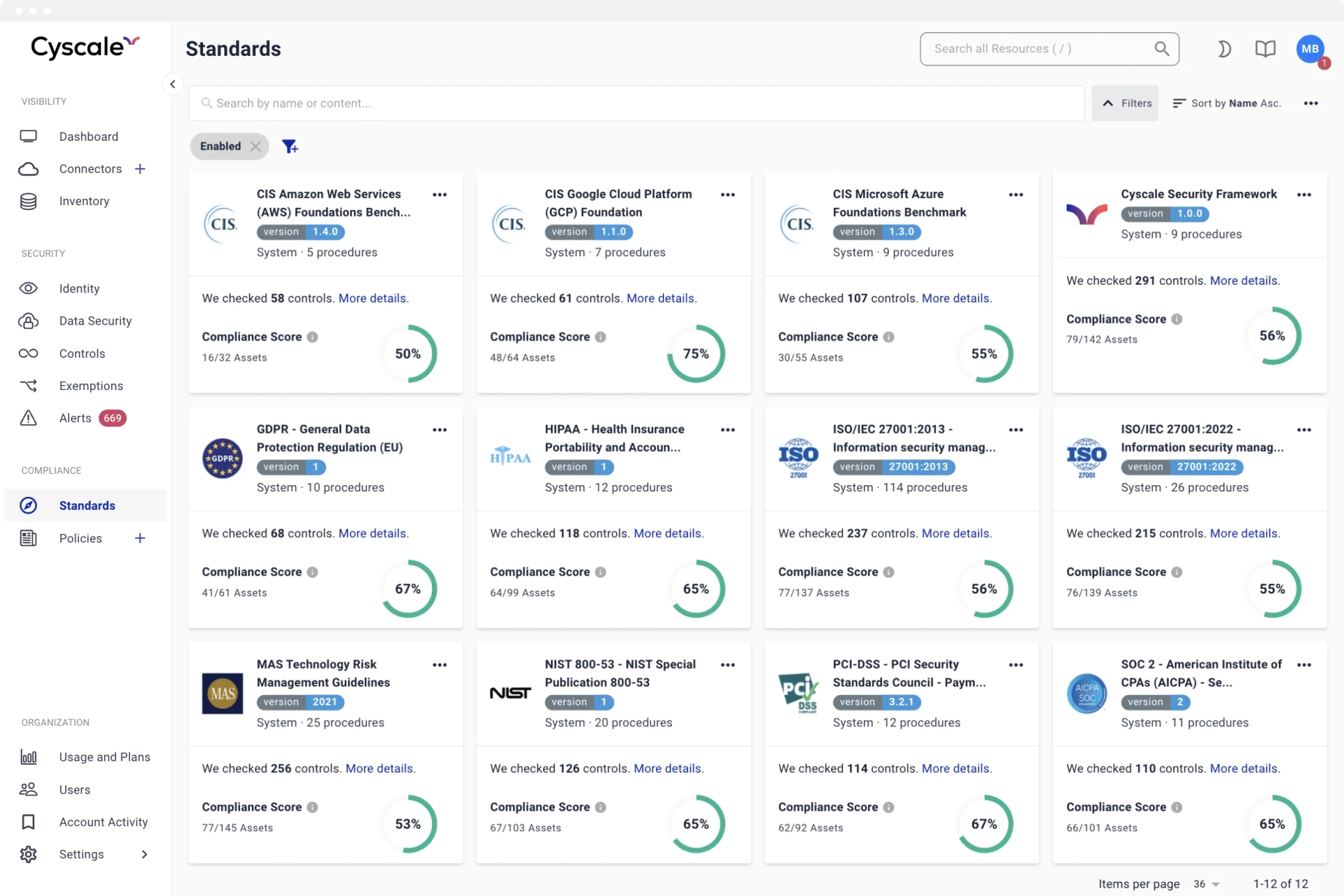
Simplify cloud security configurations
Full integration, clarity, and accuracy overlap to create the holy grail of cloud security. And our Cloud Platform sits right in the middle, delivering on all fronts. Replace separate logins, complex configurations, and disparate security settings with a dashboard so simple anyone in your team can use it. Zoom out to see the security posture of your remote teams and solve issues with a deep understanding of their impact and context.
Reduce your attack surface
Cybercriminals love insecure cloud services, especially when packed with confidential data. So when you curb overly permissive access rights and keep publicly available data in check from a single dashboard - or through our API - you make their life hard and yours much easier. Avoid privilege misuse, malware outbreaks, and other threats to cloud data security by fixing misconfigurations as soon as they appear. We help you promote a security-first culture by offering learning paths IT and security staff can use in the form of remediation guidance.
RECOMMENDED ARTICLES
CNAPP
The Complete Guide
to Cloud Storage Misconfigurations
This guide helps CIOs, CISOs and security staff to understand the risk & dangers of data security breaches and the importance of a secure cloud storage infrastructure.
