The SaaS CTO Cloud Security Handbook: A Comprehensive Checklist
Cloud Security Analyst at Cyscale
Thursday, October 12, 2023

The cloud is a powerful enabler for innovation, responsible for creating in the region of 72,000 Software-as-a-Service (SaaS) companies globally by 2024, with an additional 175,000 arriving through the current boom in AI-focused startups.
The vast majority of SaaS-building businesses and tech startups are based in the US, followed by the UK and Canada, with other parts of Europe starting to grow their reputation. Romania, for example, has earned its title as the ‘Silicon Valley of Eastern Europe’ thanks to the strength of the tech community in Cluj-Napoca, the second largest city in the country.
Public cloud as an enabler and a challenge
The public cloud is the key enabler for all these businesses. But while cloud services from AWS, Azure, Google, Alibaba and others are more widely adopted and more secure than ever before, the cloud is an increasingly complex technology to manage, with a multitude of proprietary settings and controls, growing ever more granular. As a result, the greatest challenge to cloud as an enabler exists not in the security of the cloud itself, but in the policies, controls, and workflows for security of the technology.
Cloud security breaches are caused by mistakes and misconfigurations
In nearly all cases of cloud data breach, it is the user, not the cloud provider, who fails to effectively manage the controls used to protect an organization’s data. In fact, Gartner estimates 99% of cloud security failures are the customer’s fault and there is a wealth of additional research to back this up.
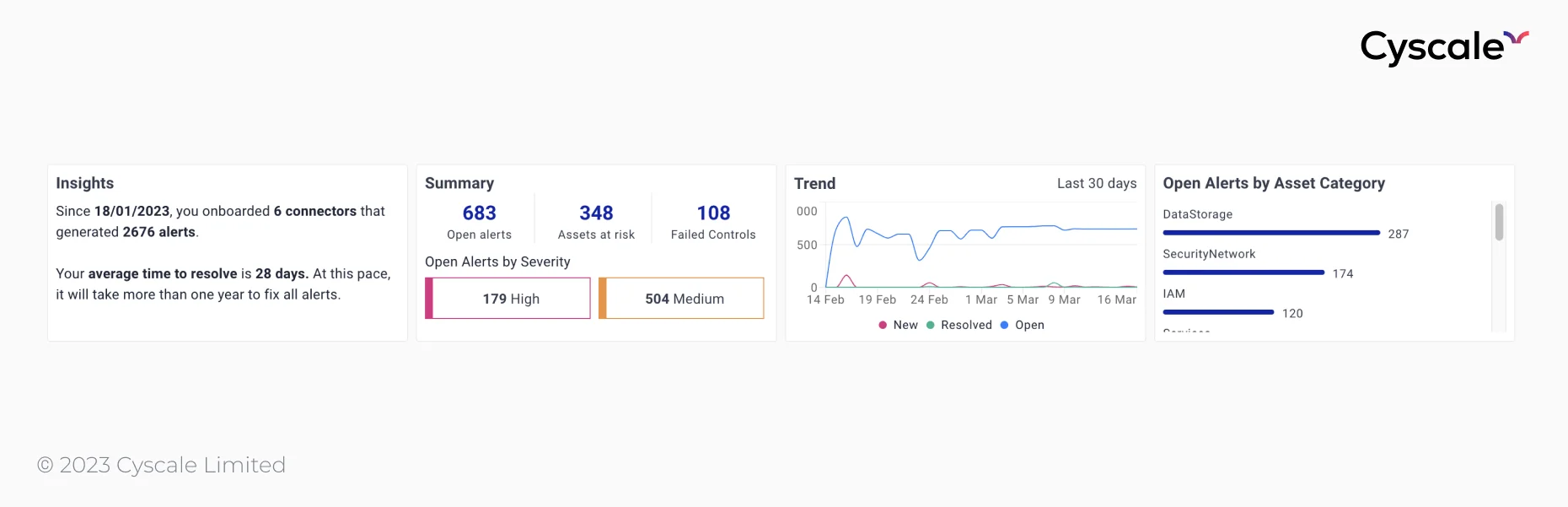
The simple fact is that humans can no longer correlate security vulnerabilities and misconfigurations manually because of the sheer volume of alerts and complexity of configurations. The problem of SaaS security is especially pervasive in companies with small security teams, where it’s also especially hard for a CTO, CISO, or head of cloud infrastructure to prioritize remediation.
Not even large, well-resourced companies are exempt, with Microsoft, Twitter, and T-Mobile among the headlines in 2023 for security incidents leading to significant breaches of cloud data.
What makes an effective cloud security strategy?
If you’re a SaaS CTO, CISO, or head of cloud infrastructure responsible for apps and data at a cloud-native or cloud-first business you need to deploy an effective cloud security strategy from the get-go. We’ve put together this SaaS CTO security checklist to help you understand what you need to do to get cloud security measures right from the start.
The SaaS CTO security checklist
In this article we look at the five key pillars that make up a strong cloud security strategy, including how to understand your unique cloud environment based on your specific usage of AWS, Google Cloud, Azure or whichever provider you choose.
You also need to consider that your cloud environment may not be static, with developers adding and removing assets, and sensitive data being created on a frequent basis. So, this means your cloud security approach can’t be static either, and you will need some kind of continuous monitoring and assessment program to check for misconfigurations and vulnerabilities along with a regular review of security policies.
In this guide to cloud security best practices we go into actionable detail that will help you create a roadmap for deployment of your cloud security strategy, covering data security when data is in motion, in use, and at rest, the types of attacks that threaten your data and what you can do to defend against them.
Understanding your cloud-native infrastructure
A foundational building block for any cloud-native cybersecurity strategy is a thorough understanding of your infrastructure and unique characteristics of your web applications including microservices architectures, virtual machines, containers, and serverless computing, among others.
This guide looks at how you can properly assess your cloud-native infrastructure, draw conclusions and create an efficient plan for remediation.
If you need a deeper dive into the cloud-native technology stack, our explainer looks at the differences between cloud-native, cloud-based, and cloud-enabled approaches.
Understanding CSPM (Cloud Security Posture Management)
As adoption of the cloud has grown, so too has the need for specialized tools to secure it. At some point you will have come across the term Cloud Security Posture Management (CSPM) as an essential part of a cloud security program designed to identify and expose the unintentional risks that can expose your data, or make your code or your infrastructure vulnerable to hackers.
What is CSPM?
CSPM solutions use the Application Programming Interfaces (APIs) offered by public cloud providers such as AWS, Azure, and Google, to gather rich data on your specific cloud configuration and workloads. These cloud security platforms use their own sophisticated technologies to process and analyze this data to identify misconfigurations, vulnerabilities, and risks, with some adding additional context and identifying potential threats, as well as suggesting remedial measures before any actual breach occurs.
Unintentional cloud configuration mistakes typically occur because of the complexity of the environment or because of poor visibility into the organization’s cloud security posture due to too many dashboards, management panels, or controls. This becomes your problem.
Regardless of the reason, it is important to understand that even one misconfiguration can lead to a disastrous data breach or leakage.
We have an essential guide to understanding Cloud Security Posture Management for those that need familiarize themselves.
Best practices for CSPM
In our CSPM best practices document, we look at how CSPM solutions can be used to ensure visibility of assets; use context to identify and prioritize assets with the greatest risk; ensure compliance with relevant frameworks (ISO 27001, SOC 2, GDPR, HIPAA, PCI-DSS, NIST and more); maintain ongoing monitoring of your environment to identify new threats; and finally, direct you to efficient remediation.
What to look for in a CSPM solution
Our separate guide on what to look for in a CSPM solution equips you with key questions to ask and considerations to help you make the right choice for your business at your current state of cloud maturity.
While our buyer’s guide to cloud security solutions goes into even further detail regarding the difference between enterprise-grade solutions, security offerings from your cloud service provider, and the free tools on offer.
Understanding CNAPP
Another acronym you may encounter - CNAPP (Cloud-Native Application Protection Platform) - refers to a security solution designed to protect cloud-native apps and combines multiple functionalities from separate toolsets, including CSPM, CWPP (Cloud Workload Protection Platform), and CIEM (Cloud Infrastructure Entitlements Management), essentially covering all the bases of identity and access, code, and infrastructure.
We have a primer on cloud-native applications security that looks at why and when you may need a CNAPP solution.
Book a free assessment with Cyscale to use CNAPP capabilities to secure your cloud security posture.
Common cloud misconfigurations and how to avoid them
In terms of actionable insights, our extensive handbook on common cloud misconfigurations looks at five of the most common cloud misconfigurations SaaS companies encounter, including: storage access configuration, access control, unrestricted network ports for inbound and outbound traffic, encryption oversights, or disabled or misconfigured logging and monitoring.
Working through this checklist can help you establish best practices for securing your apps and data in the cloud, including the use of tags to help establish security policies across all your relevant assets.
The dangers of alert fatigue
By the time you have designed a cloud security strategy and possibly deployed a few tools to help you enforce it, you will begin generating security alerts.
False positive alerts are the bane of any CTO or CISO and with cloud environments becoming so complex, alert fatigue is a very real and growing problem. A constant flood of alerts, false positives, and non-contextual information can be overwhelming, because when everything is important, nothing is important.
Alert fatigue is one of the biggest complaints cybersecurity professionals have about the tools they use. As a Cloud Security Manager we spoke to says: "When you see so many alerts, you freak out for a second."
So when it comes to beating alert fatigue, the onus is on the tools you use, and we believe three innovations are essential:
Custom risk rules – Define your own threshold for security posture. What works for one company won’t work for another.
Automation – With so many assets across so many cloud providers to track, humans cannot keep up. Continuous and automated detection of misconfigurations is critical.
Context - Not all alerts are created equal, and different teams have different responsibilities. Context allows you to immediately prioritize tasks.
Which brings us to...
Incident response planning
This is a critical part of any effective cloud security plan, because while an effective security strategy focuses on preventative maintenance, an incident response plan sets out the steps you take when a security breach happens.
Designing an effective incident response plan
We have a step-by-step checklist in our essential cloud security tips you can use to establish your incident response plan, looking at:
- Determining what caused the incident
- Containing the incident
- Notifying affected parties such as customers if customer data is affected
- Conducting a root cause analysis
- Implementing remediation measures
- Learnings and evaluation
As the threat landscape constantly evolves, so must your cloud security awareness and strategy. Business leaders must remain vigilant to new threats and vulnerabilities as well as any changes in their existing environment.
Even with a good cloud security strategy in place, an effective plan is an adaptive plan, and one that ensures ongoing defense against new threats.
Book a demo now to find out actionable insights and prepare for cloud security challenges.
Cloud Security Analyst at Cyscale
Sabrina Lupsan merges her academic knowledge in Information Security with practical research to analyze and strengthen cloud security. At Cyscale, she leverages her Azure Security Engineer certification and her Master's in Information Security to keep the company's services at the leading edge of cybersecurity developments.
Further reading
Cloud Storage
Misconfigurations

Build and maintain a strong
Security Program from the start.
Cloud Compliance in
2025: An In-Depth Guide
The whitepaper talks about ISO 27001, SOC 2, PCI-DSS, GDPR, HIPAA.
Download WhitepaperShare this article
Stay Connected
Receive our latest blog posts and product updates.
TOP ARTICLES
Cloud Security
Our Compliance toolbox
Check out our compliance platform for cloud-native and cloud-first organizations:

LATEST ARTICLES
What we’re up to

Why the world needs Cyscale in a post-Wiz era