Identity and Access Management Security
for Cloud
Scan, monitor and prioritize cloud IAM risk.
Continuous multi-cloud monitoring for identity and access management (IAM) misconfigurations across all your cloud resources to meet strict IAM compliance directives and improve your cloud security posture.
Onboard your Okta account into Cyscale and get full visibility over identities and permissions.
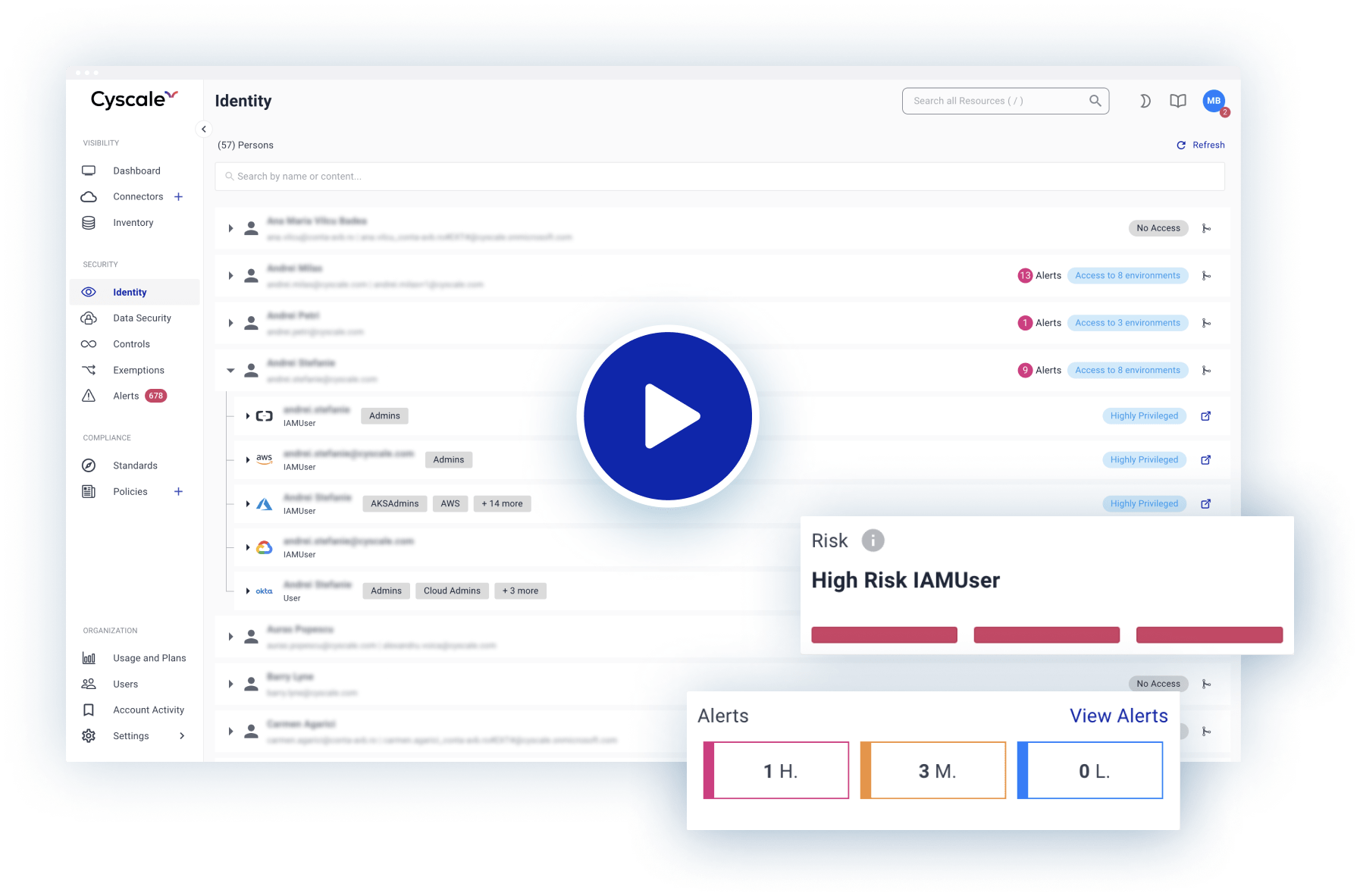
Effectively manage user permissions and enforce privilege access for a robust cloud security posture.
- A powerful Identity Dashboard helping you understand how access is provisioned in your organization on a per-person basis
- Identity provider integration: Onboard your Okta account into Cyscale and get full visibility on cloud SSO (Single Sign-On) users and provisioning
- User access misconfigurations are highlighted so that you can detect and mitigate cloud computing risk
- Easy, granular filtering for: inactive users, highly privileged or high-risk users, and others
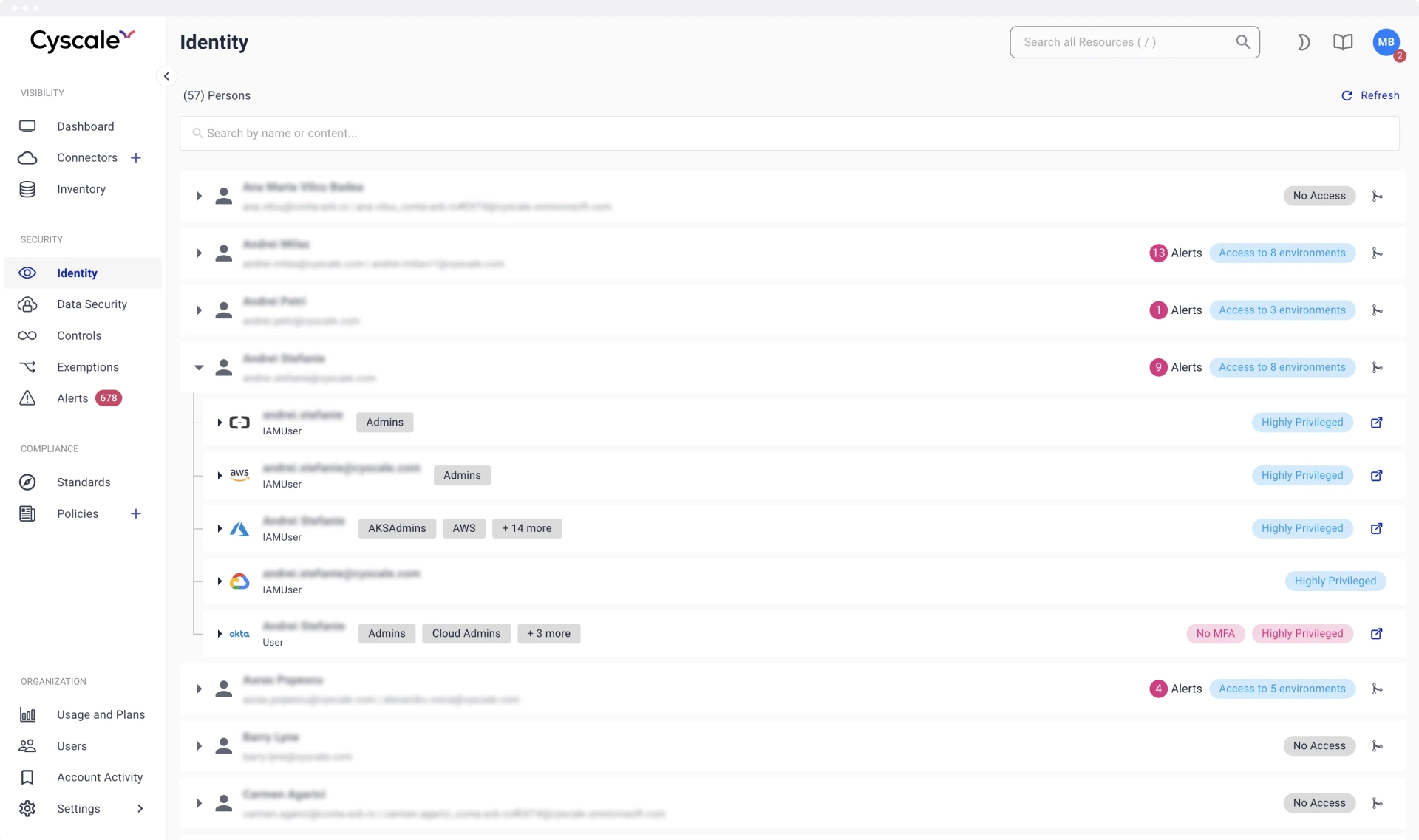
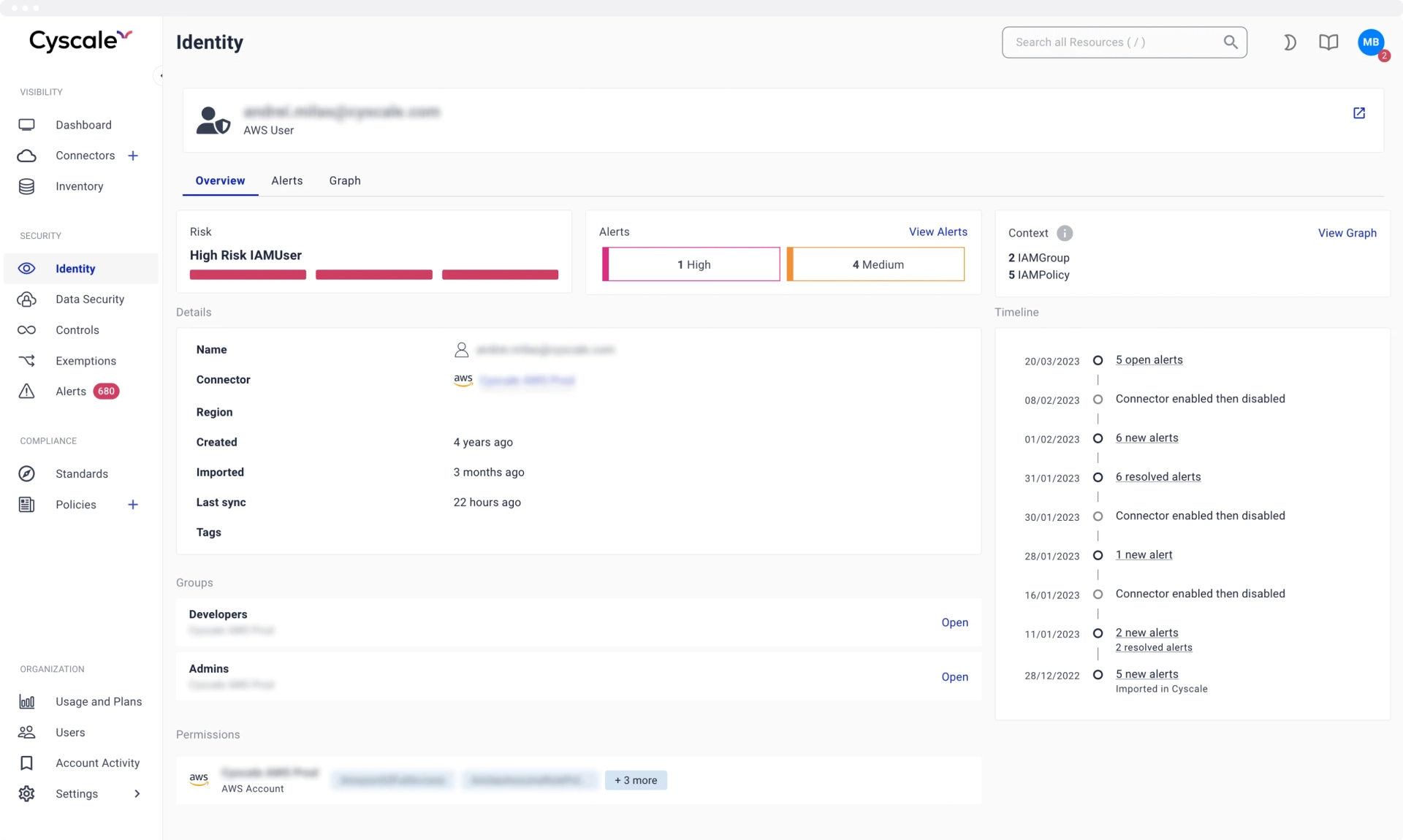
Deep dive into
User assets
An optimized page for cloud-based user assets helps you visualize and understand:
- Access (groups and permissions)
- Risk
- Policy violations
- User-related alerts
100% Confidence in your Cloud Compliance
Meet industry regulations
Protect sensitive data and comply with strict industry regulations in your organization. Cyscale automatically runs all critical compliance checks across multiple public cloud providers such as AWS (Amazon Web Services), Azure and Google Cloud, and finds data at-risk.
Built-in compliance templates
You can either use policy templates as a basis for your custom policies, or create them from scratch using a smart text editor. Your security team can control access through IAM policies, IAM roles and other IAM solutions to ensure a sound identity management program and reduce the attack surface.
PCI-DSS, SOC 2, GDPR, and more.
Cyscale offers a wide range of benchmarks and frameworks, including: CIS, ISO27001, PCI-DSS, NIST, SOC2, GDPR, and helps you prepare for auditing.
500+ out-of-the-box security controls
Onboard teams in 30 minutes and coordinate efforts to apply 500+ out-of-the-box cybersecurity controls and a large set of policies and standards to prevent data breaches. From access control, to MFA (multi-factor authentication), and the principle of least privilege, we help you with regular access reviews for your cloud infrastructure.
RECOMMENDED ARTICLES
IAM
The Complete Guide
to Cloud Storage Misconfigurations
This guide helps CIOs, CISOs and security staff to understand the risk & dangers of data security breaches and the importance of a secure cloud storage infrastructure.
