Robust Container Security
with our CNAPP solution
Our advanced container security solution protects cloud-native applications from development to production.
It tracks and secures containers throughout the lifecycle while providing advanced inventory capabilities to ensure the security of all container assets.
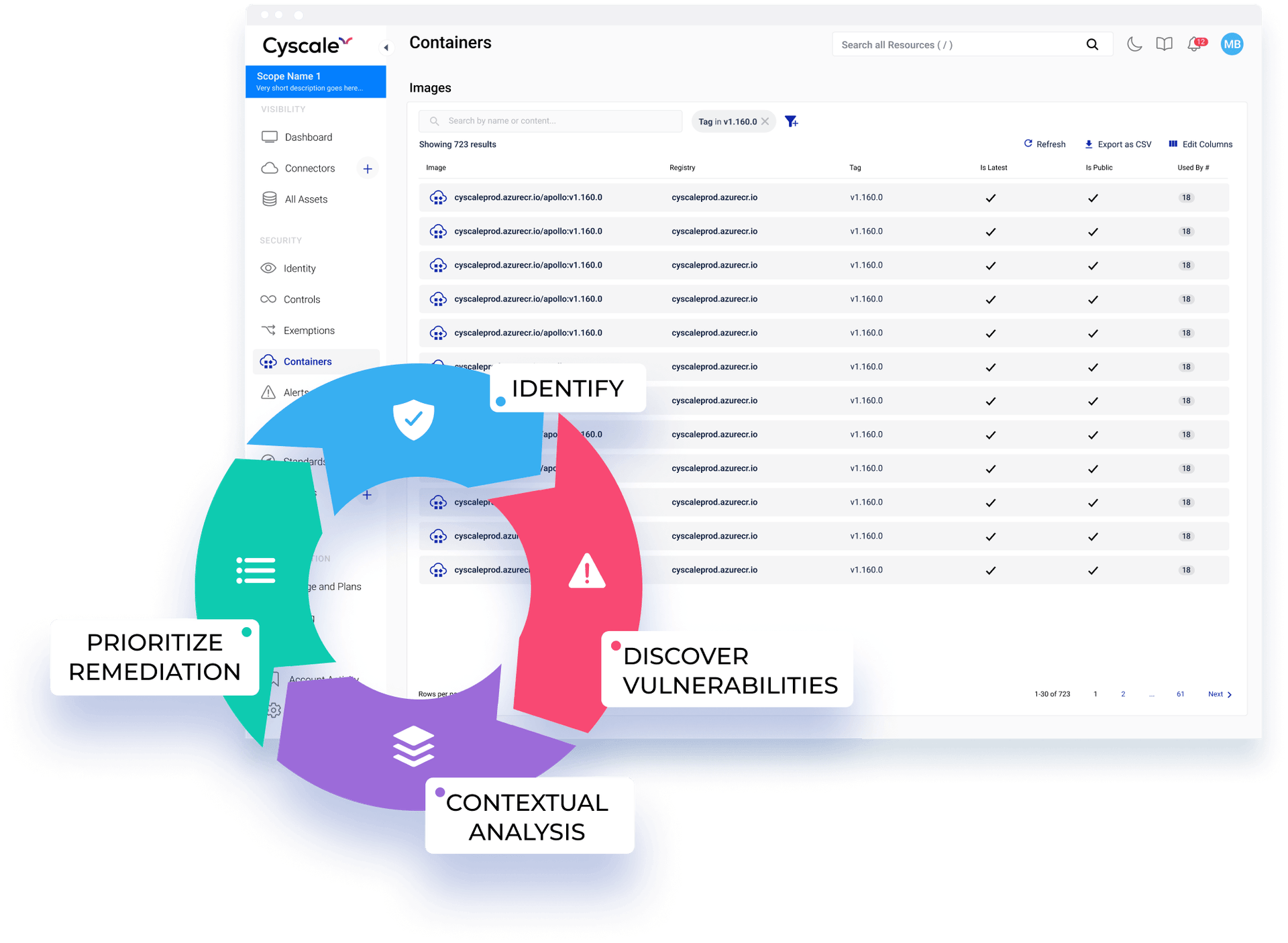
Empower your DevOps
Team with comprehensive container security
Vulnerability Scanning
Scan container images and registries for known vulnerabilities and misconfigurations, including those related to Linux dependencies and CVEs, to prevent security threats.
Access Control
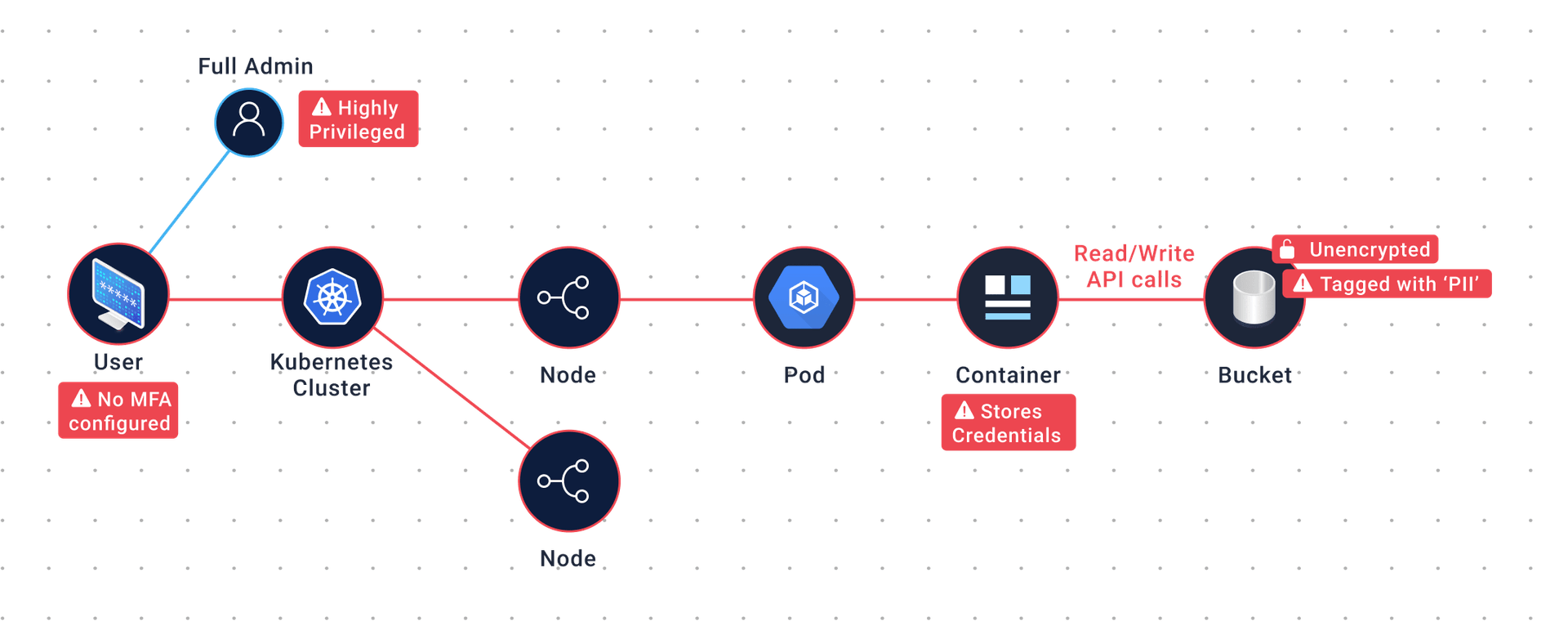
Provides granular visibility over user and application access to containerized environments, helping you check for excessive permissions and ensure that only authorized users can access the environment.
Contextual Analysis
Get contextual insights for the vulnerabilities in running container images, as well as for misconfigurations of cloud resources running containers, so that you can prevent threats to your container environments.
Agentless
Get the visibility you need for the container environments in your cloud-native applications without installing any agents.
Container Images
Know where each image is running in the cloud and ensure that you don’t use any open source libraries that don’t meet your organization's standards for security and compliance.
Orchestration
Supports Kubernetes, the most popular container orchestration platform, ensuring consistent security across different environments.
Compliance
Get guidance for adhering to well-known frameworks and best practices such as the CIS Benchmarks for Docker, Kubernetes and more.
DevSecOps-Friendly
Our solution is designed with DevSecOps principles in mind, allowing you to integrate application security principles into your software development pipeline. Scan Docker files and identify images with vulnerabilities that should never get to runtime.
Automate your Container
Security
across the entire
application lifecycle
Protect your containerized applications from cyber threats and maintain compliance effortlessly with our Container Security solution. Our powerful automation tools streamline the process from build to deploy, ensuring consistent and efficient security measures throughout the entire application lifecycle. This means you can spend less time on manual security checks and more time on developing innovative features for your customers.
Some of the benefits of our Container Security solution include:
- Continuous security measures that are always working in the background, keeping your containerized applications secure
- Automation of critical security checks, such as vulnerability scanning and misconfiguration detection, to find and remediate issues before they become a problem.
- Faster time to market and reduced risk of security vulnerabilities, thanks to improved efficiency and reduced manual errors.
Align teams & tasksGovern all cloud entities
from a single dashboard
Consolidate all the key elements of cloud compliance in an easy-to-use dashboard. Replace cloud portals with our Cloud Platform - the hub for a sweeping overview of your
cloud security posture.
Implement, manage, and monitor security policies and controls for single cloud and multi-cloud environments through reliable automation.
Demonstrate compliance for multiple projects with read-only dashboard access or reports (CSV, PDF) you can share with internal stakeholders, prospects, or customers.

100% Confidence with
your Cloud Compliance
Meet industry regulations
Protect sensitive data and comply with strict industry regulations in your organisation. Cyscale automatically runs all critical compliance checks and finds data at-risk across multiple cloud service providers.
PCI-DSS, SOC 2, GDPR, and more
Cyscale offers a wide range of benchmarks and frameworks, including: CIS, ISO27001, PCI-DSS, NIST,
SOC 2, GDPR.
Built-in compliance templates
You can either use policy templates as a basis for your custom policies, or create them from scratch.
500+ out-of-the-box security controls
Onboard teams in 30 minutes and coordinate efforts to apply 500+ out-of-the-box security controls.
Take control of your container security and protect against
vulnerabilities, exposures, and threats
Start seeing value & saving money in minutes