Why is ISO 27001 important?
ISO/IEC 27001:2013 is the golden international standard when it comes to information security. Part of the ISO/IEC 27000 family, it helps organizations protect their assets such as employee information, user data, and intellectual property. Being ISO 27001 compliant gives you and your customers the confidence to run and expand your business.
Becoming ISO 27001 Compliant
Either you decide to start/improve your cloud security program or a client requires compliant vendors
Assemble a team of 2 to 20 people, depending on the size of your organization, responsible for the entire process. This might include your CSO, CISO, compliance officers, security engineers and researchers, and software architects.
Optionally, contact a third-party company specialized in ISO 27001 compliance.
Understand the standard
- Clauses 4 to 10 - they describe the requirements of the standard. The result will be a set of policies that will form the information security management system (ISMS).
- Annex A - a comprehensive list of control objectives and information security controls intended to help you reduce the risk as much as possible.
Identify the scope of the ISMS taking into consideration
- the organization's objectives regarding risk management
- the requirements of the involved parties
- the asset inventory - might include legal documents, user data, cloud resources, and physical equipment.
Define and apply the information security risk mitigation treatment
- Annex A controls provide a holistic but general approach. You are still responsible for researching and implementing actual procedures to secure your assets
- This is a critical point for organizations running in the cloud
- You document the controls (both inclusions and exclusions) in the Statement of Applicability (SoA). This is an essential document for the ISMS and it is one of the first points of interest for the auditor.
Establish and implement the policies forming the ISMS
- You can start with a set of pre-defined policies
Inform and train every employee
Perform an internal audit
- Can be conducted by members of the organization or by consulting firms
Perform the actual audit
- The auditor will review your documents starting with the scope document, statement of applicability, and various policies such as the human resource security and data protection policies
- Once the auditor determines that your ISMS meets the ISO 27001 requirements, you proceed to stage 2. At this point, the auditor will check your controls to determine their effectiveness within your organization
Continuous compliance - the point of the security standard is not to pass the audit but to improve the cybersecurity of your information assets
- Periodically review your policies (designated owners and management)
- Keep your asset inventory up to date and ensure business continuity
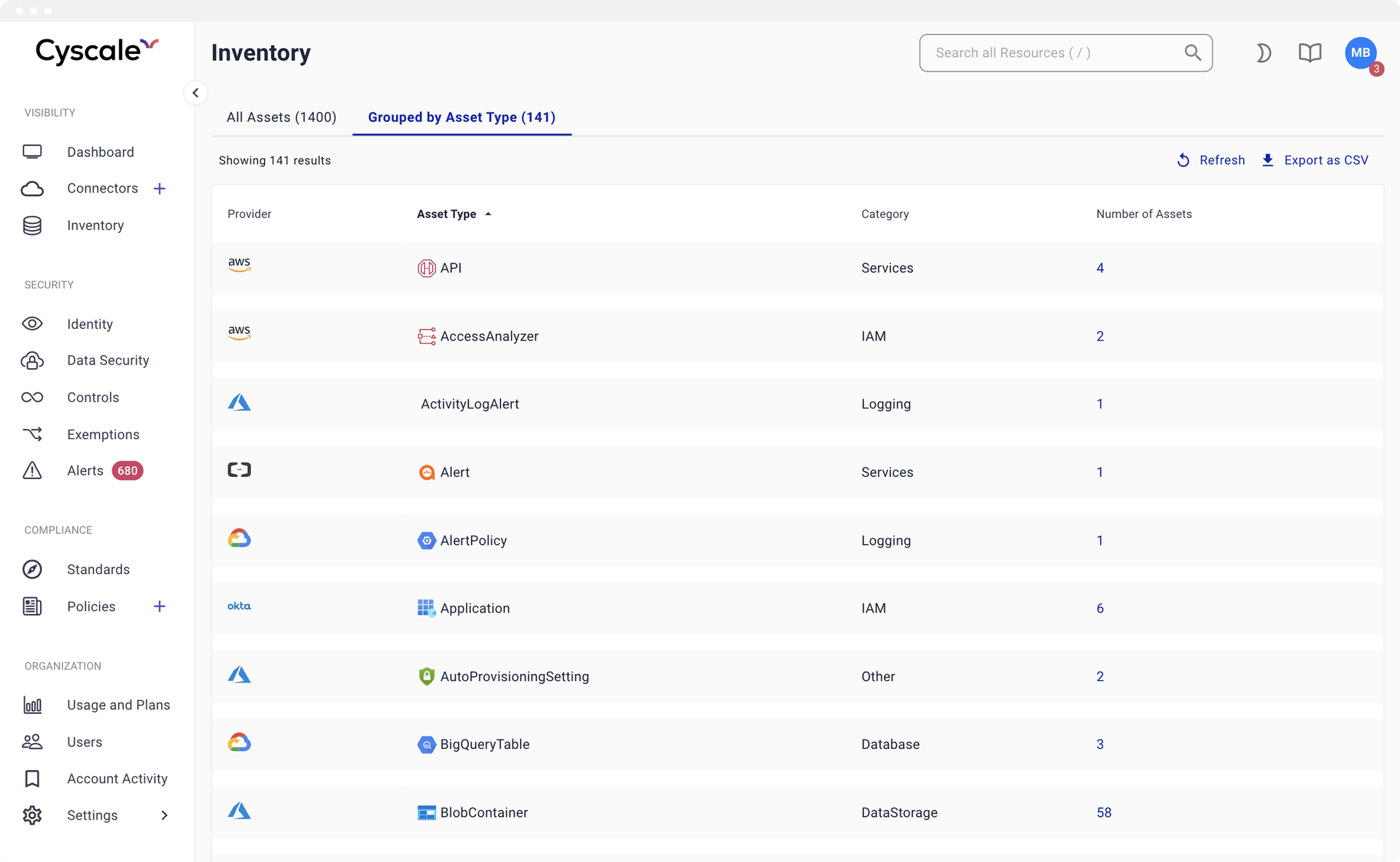
Asset Inventory
Keep track of all your cloud computing assets such as virtual machines, cloud storage buckets, and IAM users. Cyscale allows you to connect all your cloud accounts from cloud service providers (AWS, Google Cloud, Azure, and Alibaba), in a read-only mode.
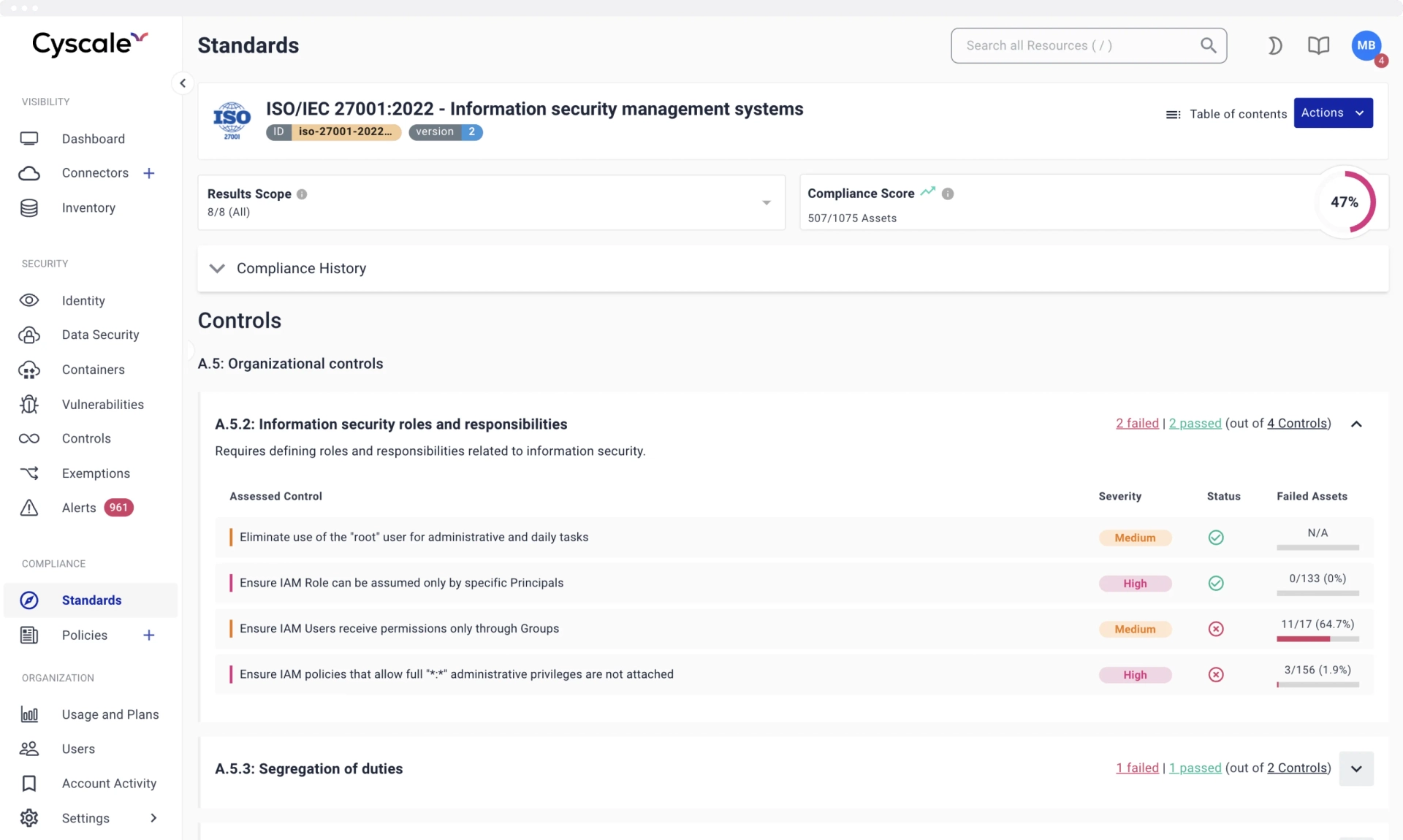
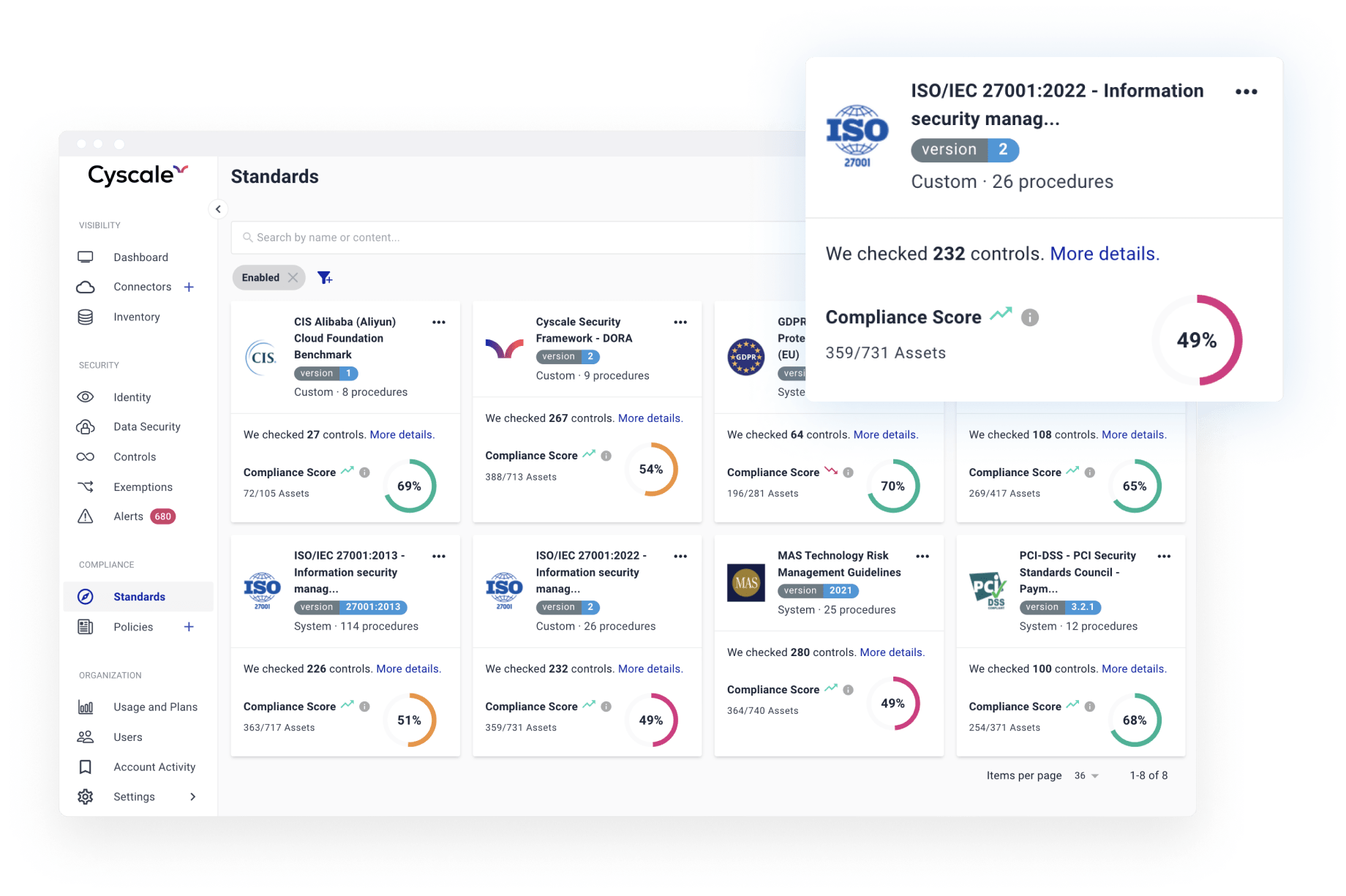
Annex A Controls and beyond
Continuously keep your cloud infrastructure and your sensitive data secure by following industry best practices to prevent vulnerabilities, such as CIS benchmarks and well-architected frameworks, all neatly mapped to ISO 27001. You can establish the statement of applicability for your cloud assets in minutes instead of weeks.
Out of the box Policies
Cyscale provides you with a set of battle-tested security policies to jumpstart your ISMS. They are applicable to all your assets such as employee information, intelectual property, and physical equipment, besides cloud assets. They help you improve your security posture and prevent security incidents.
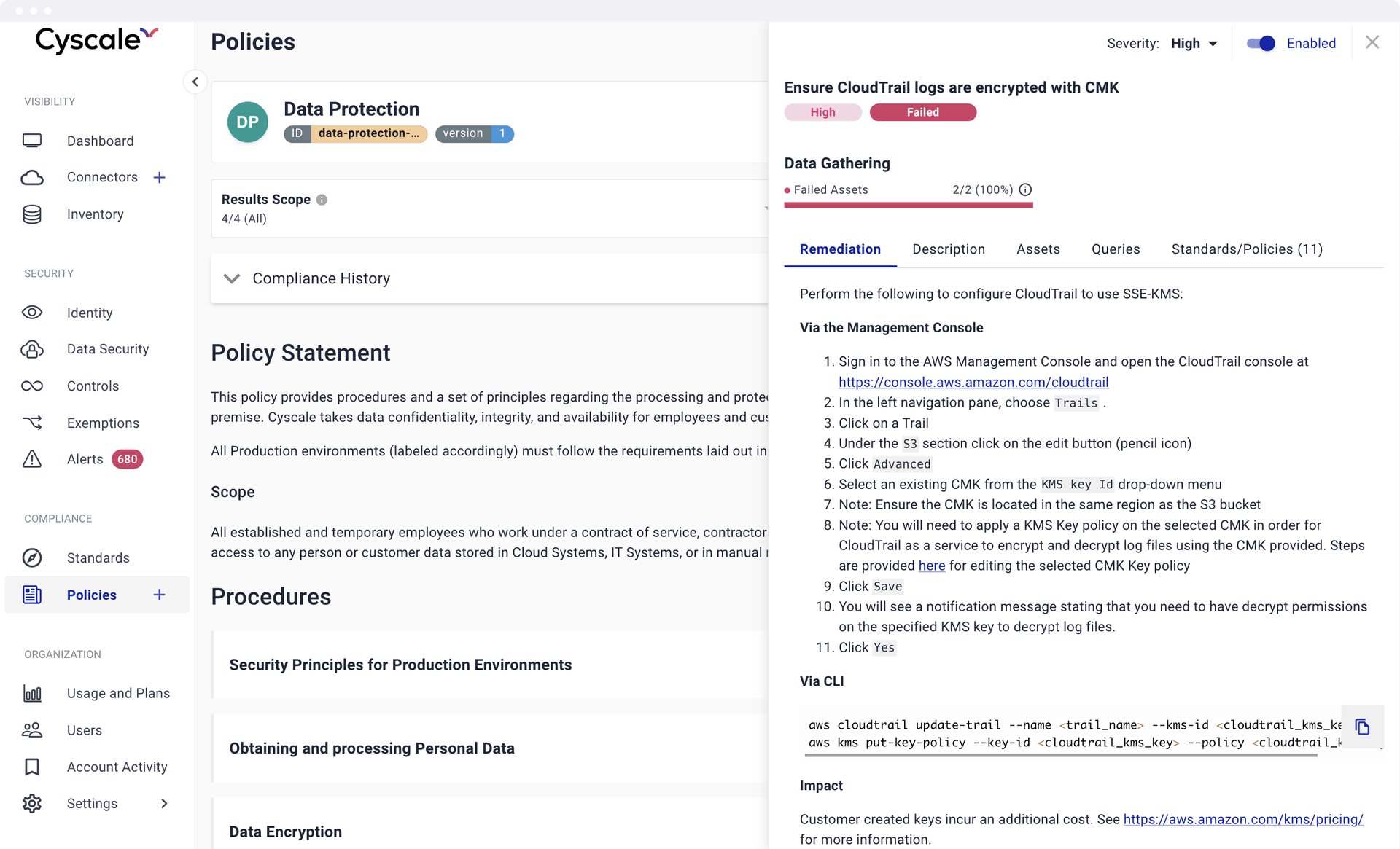
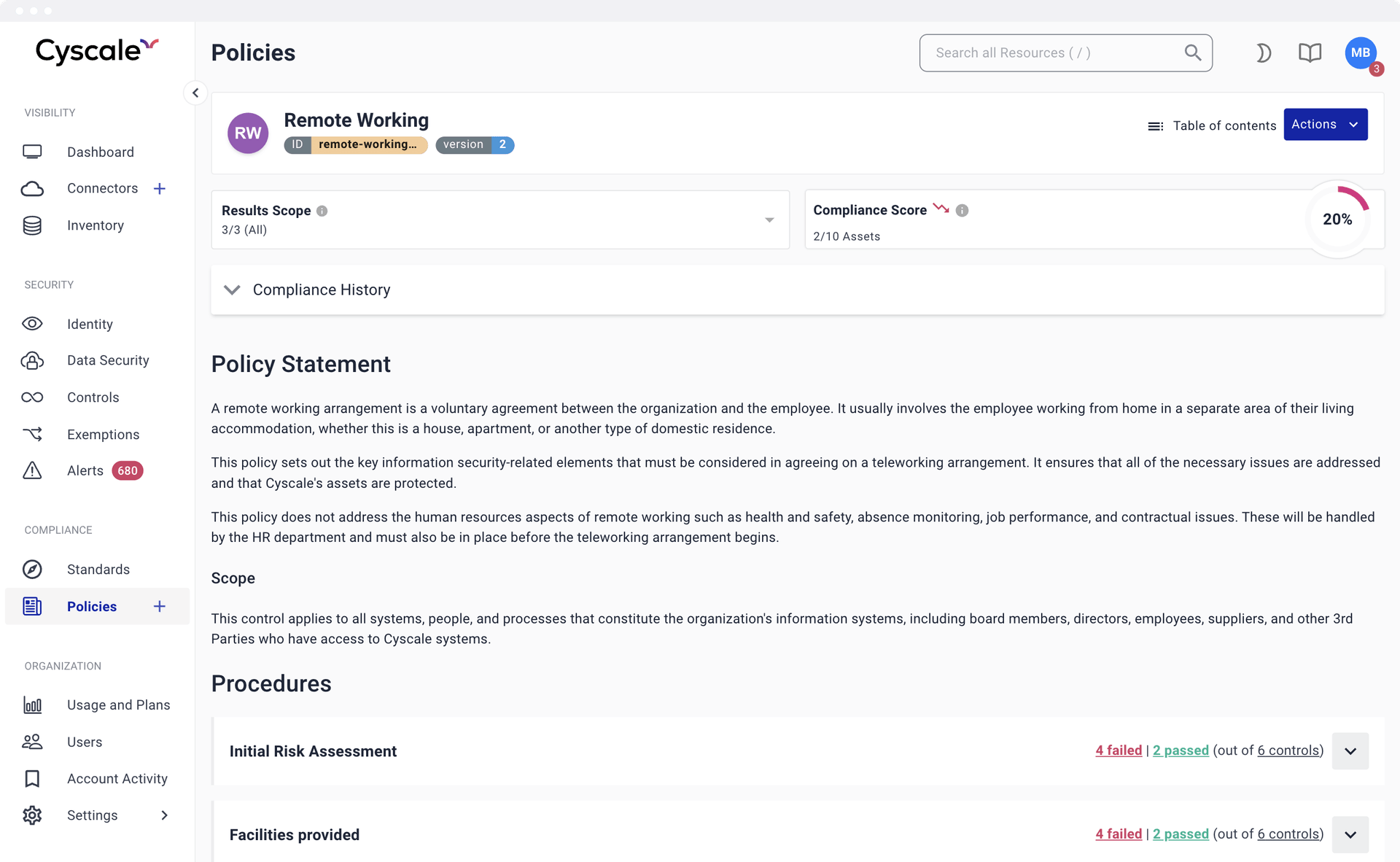
Actionable Policies
Cyscale enables you to link procedures to actual technical verifications and security controls. You know at any moment the exact compliance status of your assets right inside the policy that describes how they are secured. In other words, inline evidence collection. Moreover, you can automate compliance checks to streamline the process of obtaining the ISO 27001 certification. We also support GDPR, HIPAA, and other regulatory frameworks.
RECOMMENDED ARTICLES
Compliance
What every SaaS needs to knowAWS SOC 2 Compliance Checklist:
A Detailed GuideCloud Security and Compliance:
A Guide for Your Cloud InfrastructureCloud Compliance 101:
From Basics to Best Practices
The In-Depth Guide
to Cloud Compliance
in 2024
What standards exist on the market, and who are they destined for?
Download the whitepaper to read about ISO 27001, SOC 2, PCI-DSS, GDPR, HIPAA.