KSPM SOLUTION
Kubernetes Security
and Compliance Platform
Protect your K8s environments with a complete Kubernetes Security Posture Management (KSPM) and misconfiguration detection solution. See where you have Kubernetes images with vulnerabilities and where those images are deployed.
Map, secure, and monitor your Kubernetes environment in minutes.
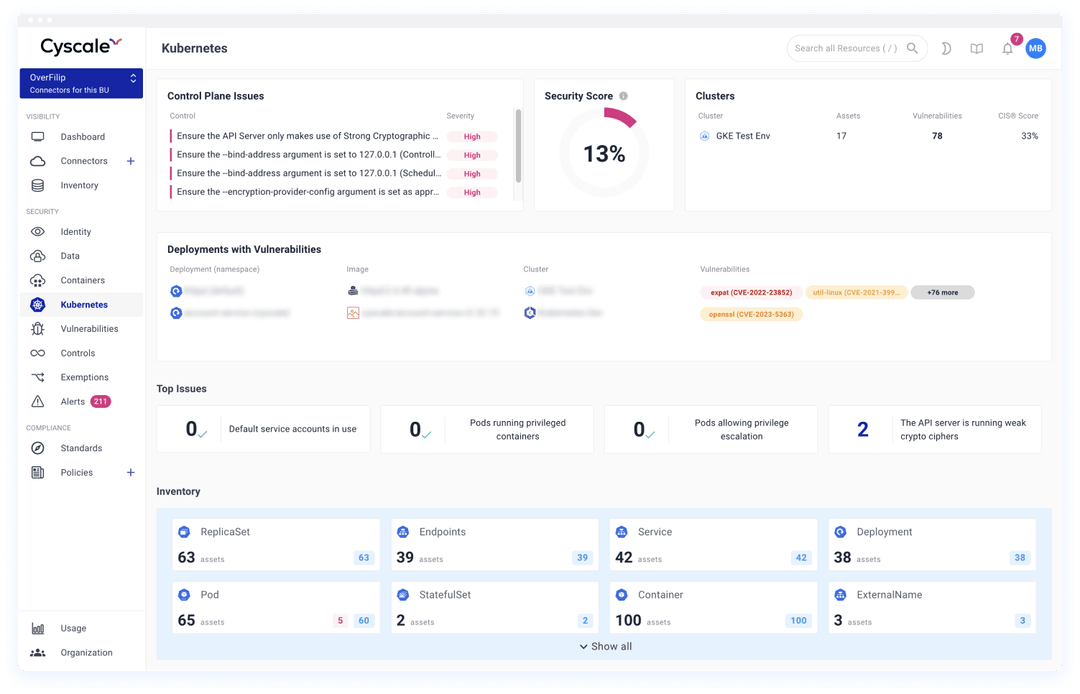
Streamline posture management with Cyscale’s Kubernetes security platform. Get visibility into your K8s security and achieve continuous compliance.
- Cloud-native cybersecurity across workloads, with Azure Kubernetes Service (AKS), Amazon Elastic Kubernetes Service (EKS), and Google Kubernetes Engine Service (GKE) management and monitoring.
- Security controls for Kubernetes clusters, pods, containers and other services to ensure comprehensive misconfiguration coverage.
- Map components from your Kubernetes cluster to the actual infrastructure on which it is running. See where you have Kubernetes images with vulnerabilities and where those images are deployed.
- Ensure least privilege access in Kubernetes with Identity and Access Management (IAM) assessments to continuously reduce the risk of over-provisioned roles and service accounts.
- Audit-ready PDF report with Asset Inventory across your Kubernetes estate.
Automate Kubernetes compliance checks & security control audits
Automate compliance checks of your managed and unmanaged K8s environments. Cyscale covers all the AWS, Google Cloud, Azure, and general CIS Kubernetes Benchmarks, with 100+ security controls checked.
100% Confidence in your Kubernetes Compliance
See and respond to known Kubernetes threats
Find and prevent misconfigurations and threats in your Kubernetes environments, without dealing with false positives and overwhelming alerts.
Meet industry regulations
Protect sensitive data and comply with strict industry regulations in your organization. Cyscale automatically runs all critical compliance checks and finds data at-risk.
Built-in compliance templates
You can either use dozens of out-of-the-box policy templates as a basis to configure custom policies or import your own using a smart text editor.
PCI-DSS, SOC 2, GDPR, and more
Cyscale offers a wide range of benchmarks and frameworks, including CIS, ISO27001, PCI-DSS, NIST, SOC2, GDPR, to help you obtain certifications.
Dozens of out-of-the-box security controls
Onboard teams in 30 minutes and coordinate efforts to apply out-of-the-box security controls and a large set of policies and standards covering containers, access control, authentication, firewall configuration, permissions, network security, identity and others.
RECOMMENDED ARTICLES
Compliance
Google Cloud - A Cloud Industry OverviewSecuring IAM - Best Practices Recommended by AWS, Azure, and Google CloudCloud Security and Compliance:
A Guide for Your Cloud InfrastructureUnderstanding serverless computing:
how you can use it and how to secure itWhat Is Data Classification And
Why Is It Important?Cloud Compliance 101:
From Basics to Best Practices
The In-Depth Guide
to Cloud Compliance
in 2024
What standards exist on the market, and who are they destined for?
Download the whitepaper to read about ISO 27001, SOC 2, PCI-DSS, GDPR, HIPAA.