Vulnerability Management: Secure VMs, containers & data across your cloud
Continuously scan your multi-cloud environment, identifying vulnerabilities and ensuring compliance.
Experience real-time monitoring, intuitive insights, and streamlined security management - all through one unified CNAPP platform.
Protect Your Cloud Infrastructure
- Comprehensive Scanning: Scan your entire multi-cloud estate for insecure configurations, exposed vulnerabilities, and potential attack vectors.
- Enhanced Kubernetes Vulnerability Scanning: Identify vulnerabilities in Kubernetes pods in near real-time and understand their impact in the context of your cluster.
- Built on State-of-the-Art Open-Source Projects: Having Syft and Grype at its core, two well-maintained OSS projects, Cyscale is up to date with the vulnerabilities and scanning capabilities, while keeping a simple deployment model.
- Real-Time Monitoring: Monitor key indicators and potential threats to act quickly and prevent breaches.
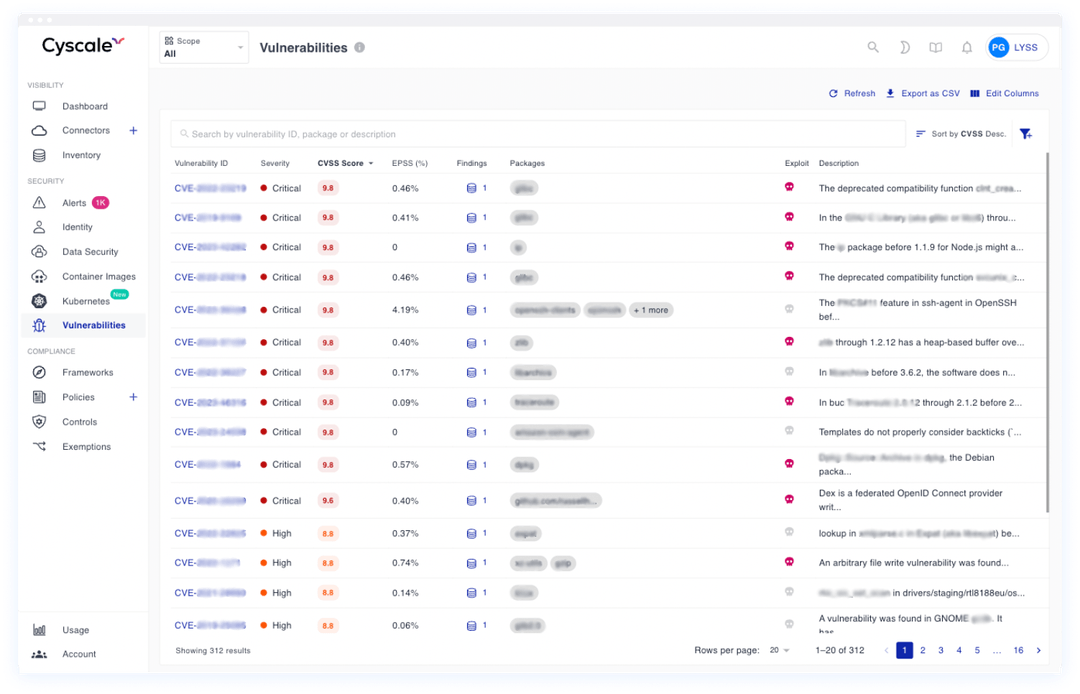
- Prioritize Vulnerabilities: Easily identify and prioritize vulnerabilities based on severity, ensuring timely remediation.
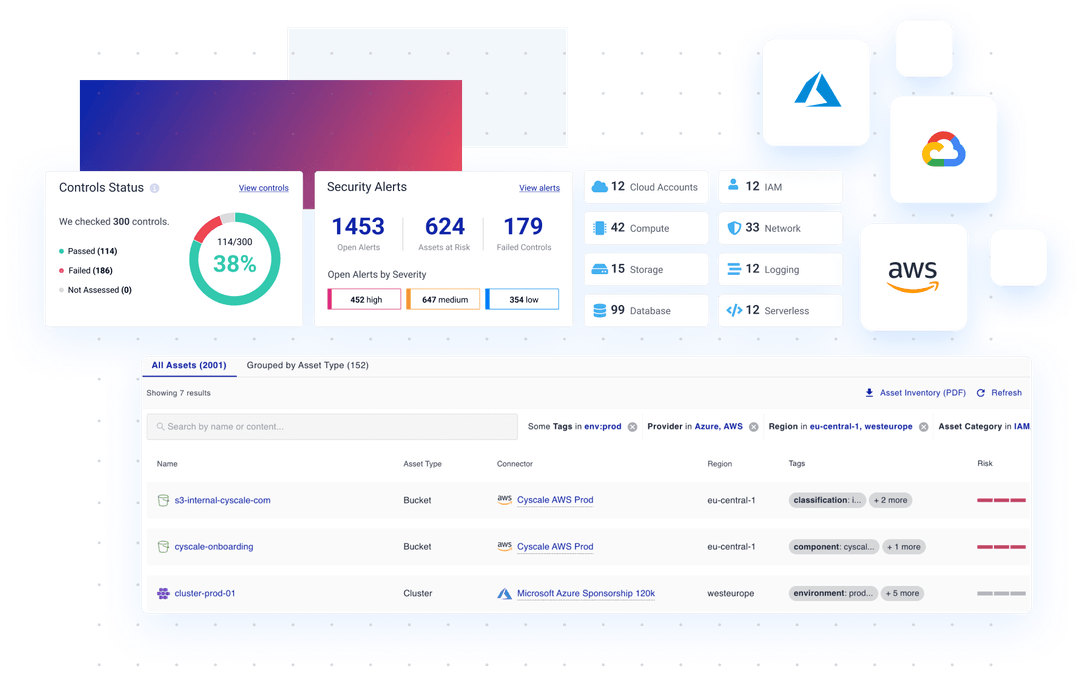
- Get a complete overview of your cloud assets and understand complex attack paths based on the relationships between resources.
- Complete Insights: Get a complete overview of your cloud assets and understand complex attack paths with intuitive visualization.
- Broad Coverage: Cover vulnerabilities across VMs, serverless functions, containers, and Kubernetes clusters for comprehensive protection.
Discover Simple, Secure Vulnerability Management with Our Tour
See how you can transform complex security tasks into a walk in the cloud.
Dive into real-time monitoring and protection for all your data across any cloud service.
Simplify Vulnerability Management
A single pane of glass view into all cloud-based assets helps you understand:
- Real-time vulnerability detection and alerts
- Detailed vulnerability assessment and impact analysis
- Remediation guidance and automation
- Risk prioritization based on potential impact
- Policy violations and compliance gaps
- User-related alerts and activity monitoring
- Customizable Deployment: Integrate with private repositories and generate SBOMs for comprehensive vulnerability assessment.
- Where to enforce best practices and mitigate risks
100% Confidence with
your Cloud Compliance
Meet Industry Regulations
Protect sensitive data and comply with strict industry regulations. Cyscale automatically runs all critical compliance checks across multiple public cloud providers such as AWS, Azure, and Google Cloud, as well as Kubernetes, identifying vulnerabilities that put your data at risk.
Built-in Compliance Templates
You can either use policy templates as a basis for your custom policies or create them from scratch. Control access through IAM policies, IAM roles and other IAM solutions to ensure a comprehensive identity management program and reduce the attack surface.
PCI-DSS, SOC 2, GDPR, and more
Cyscale offers a wide range of benchmarks and frameworks, including CIS, ISO27001, PCI-DSS, NIST, SOC2, GDPR, and helps you prepare for auditing.
500+ out-of-the-box security controls
Onboard teams in 30 minutes and coordinate efforts to apply 500+ out-of-the-box cybersecurity controls and a large set of policies and standards to prevent data breaches. From access control to MFA (multi-factor authentication) and the principle of least privilege, we help make regular access reviews for your cloud infrastructure quick and painless.
Cloud Vulnerability Management
Boost cloud security with CNAPP and advanced vulnerability management
for comprehensive, proactive threat protection.
RECOMMENDED ARTICLES
Cloud Security
Data Security
in the Cloud
A Comprehensive Guide
Explore effective strategies for cloud data security, including encryption, data classification, and misconfiguration remedies in this essential guide.

