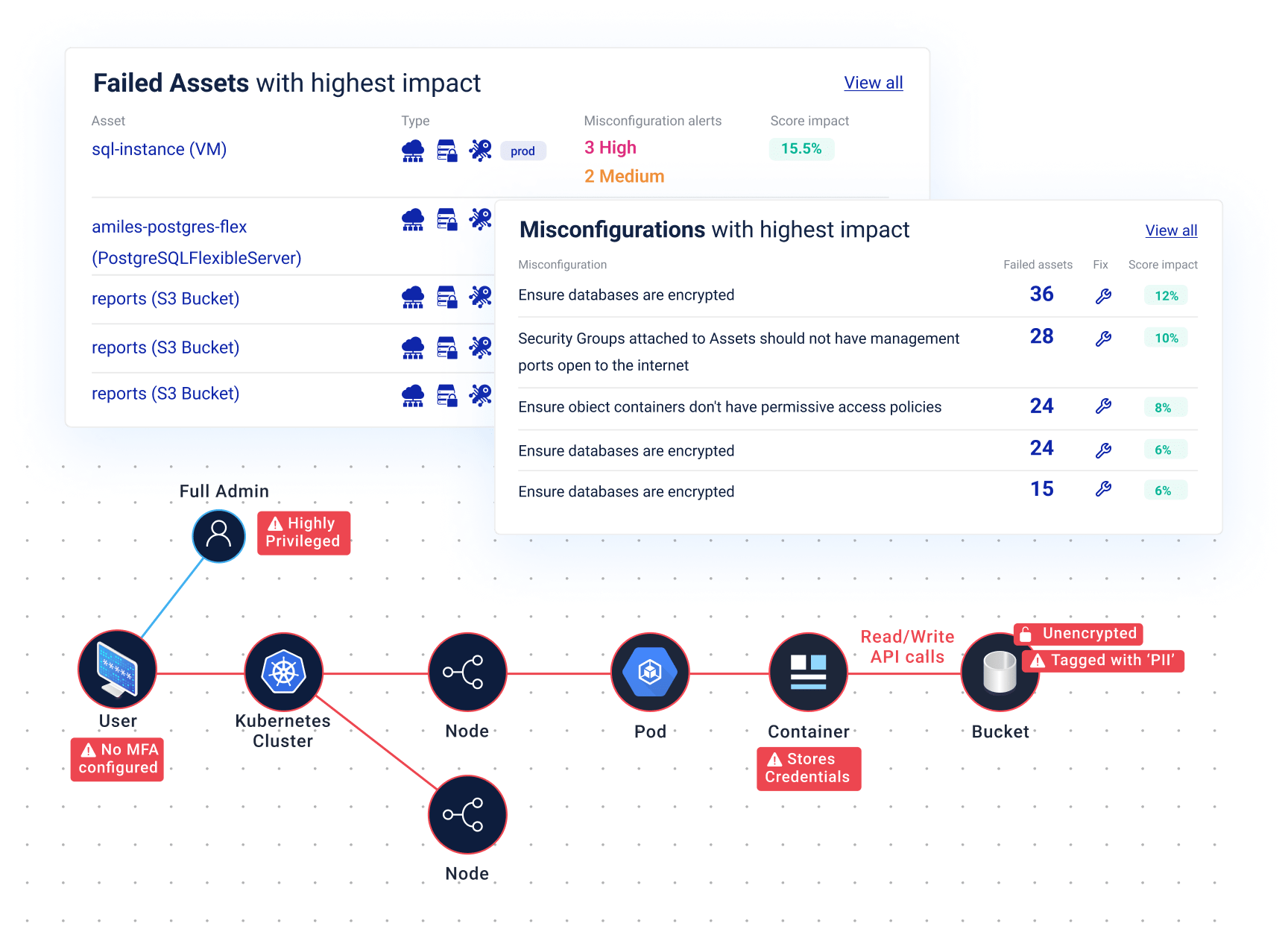
Cyscale has you covered
Prevent misconfigurations & mistakes
A single misconfiguration can have a devastating impact on your cloud security.
Cyscale automatically detects misconfigured services across identity, compute, storage, networking, container services, managed Kubernetes, and many more.
Get step-by-step remediation guidelines for any finding, so that you can act fast to reduce your attack surface and prevent incidents.
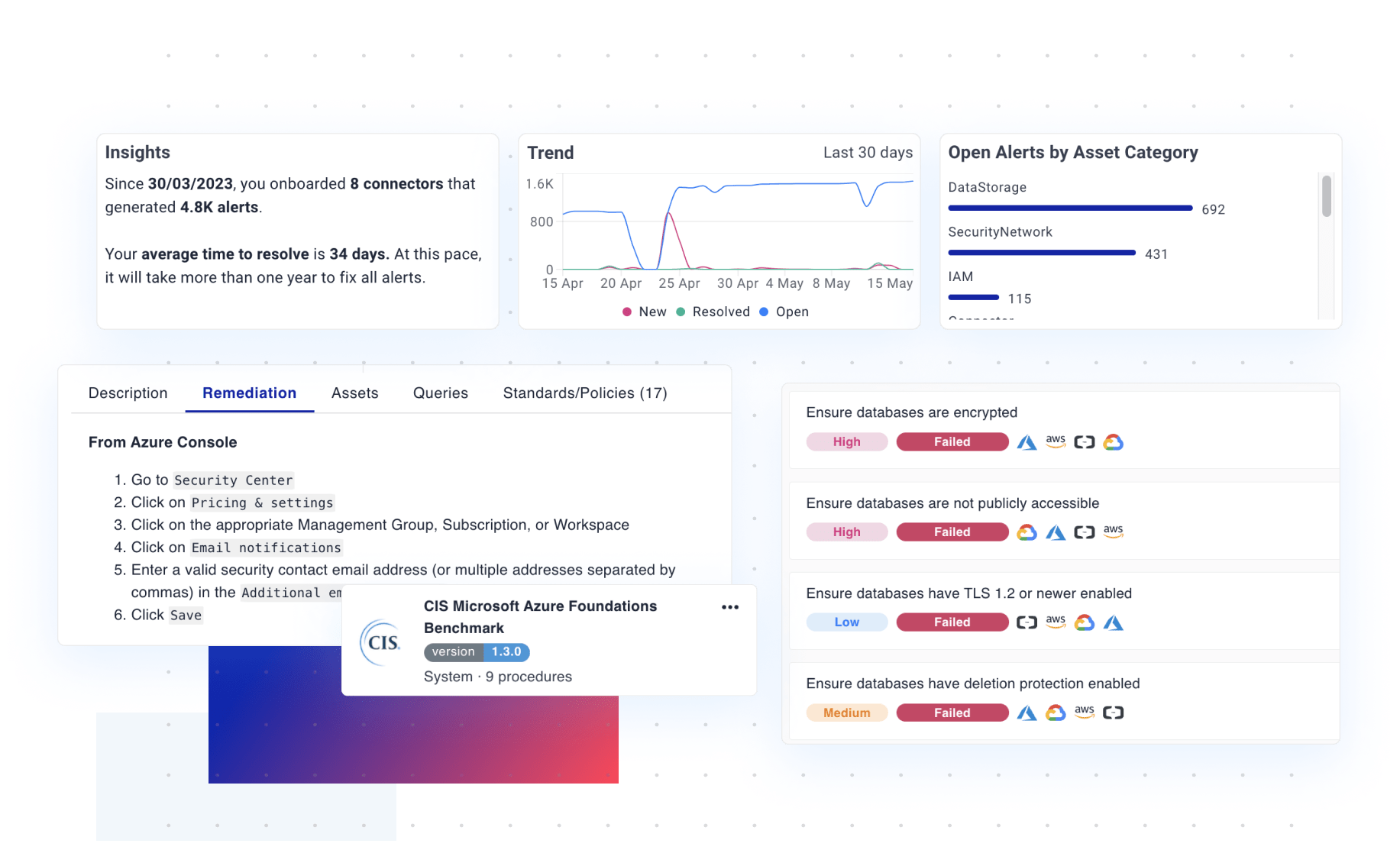
Cut through
the noise
Don't waste time chasing false positives. Get contextual alerts when your cloud assets drift away from established security and compliance standards.
Instead of overwhelming list-based management, Cyscale's Security Knowledge Graph™ makes precise correlations between all your cloud assets and data repositories to automatically pinpoint critical security improvements.
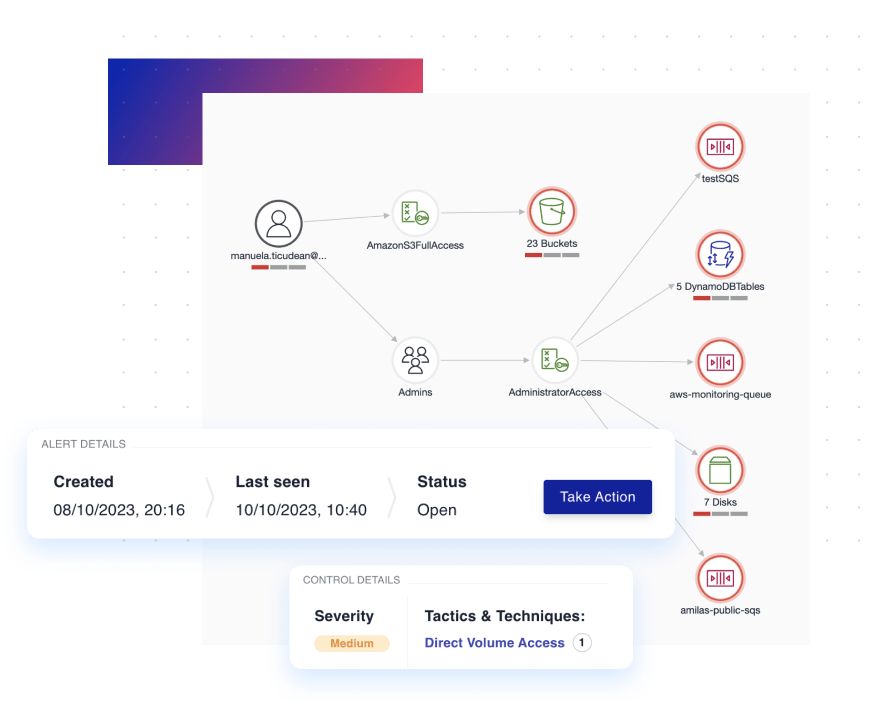
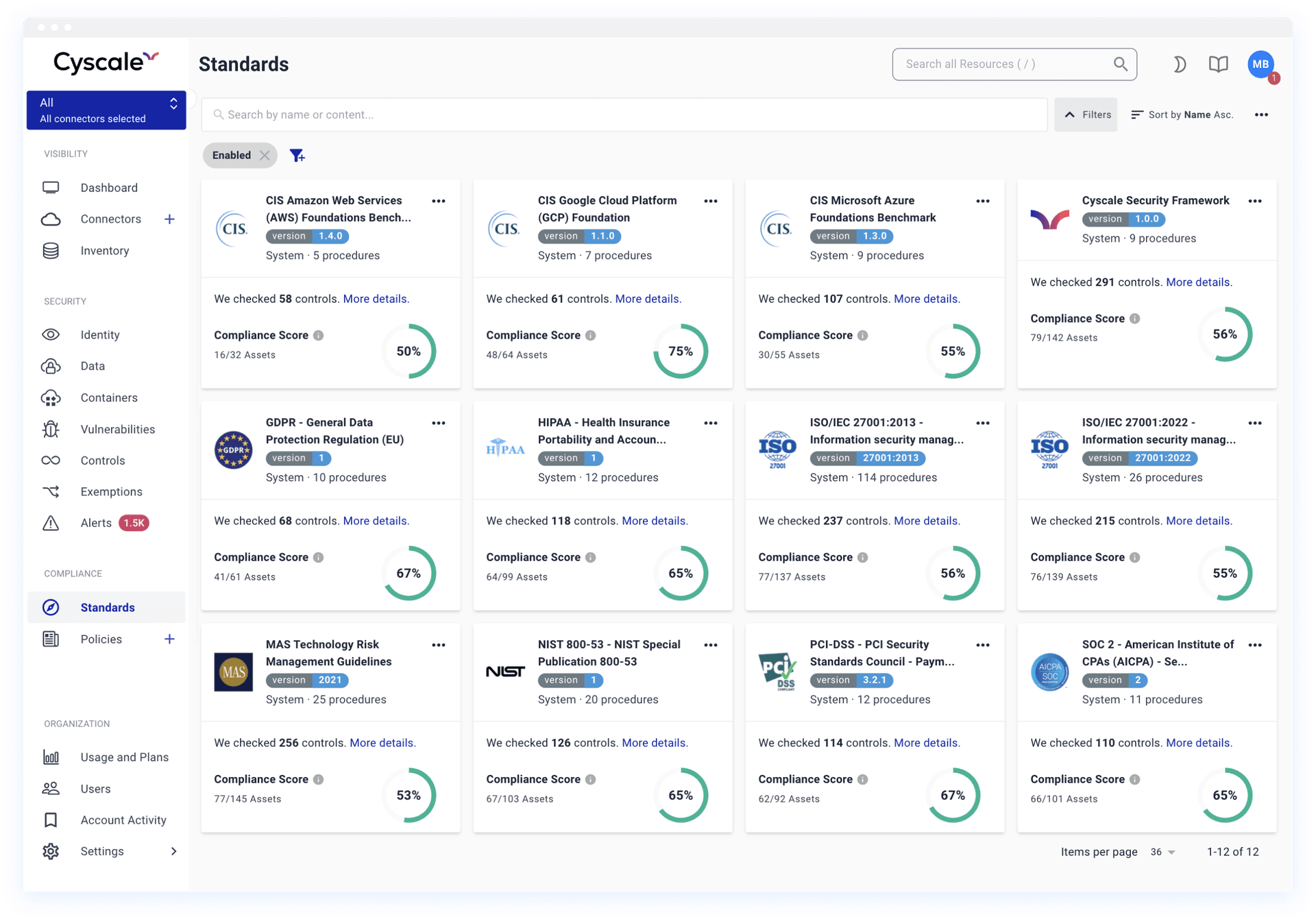
Out-of-the-box actionable policies and standards
In-app security standards and organizational security policy templates for CIS Cloud Benchmarks, ISO 27001, SOC 2, GDPR, HIPAA, PCI DSS, NIST, and many more help your team with internal or external audits.
Automated and continuous assessment of your cloud compliance, with custom Controls that tap into our Security Knowledge Graph to deliver the security and compliance checks that matter most to your organization.
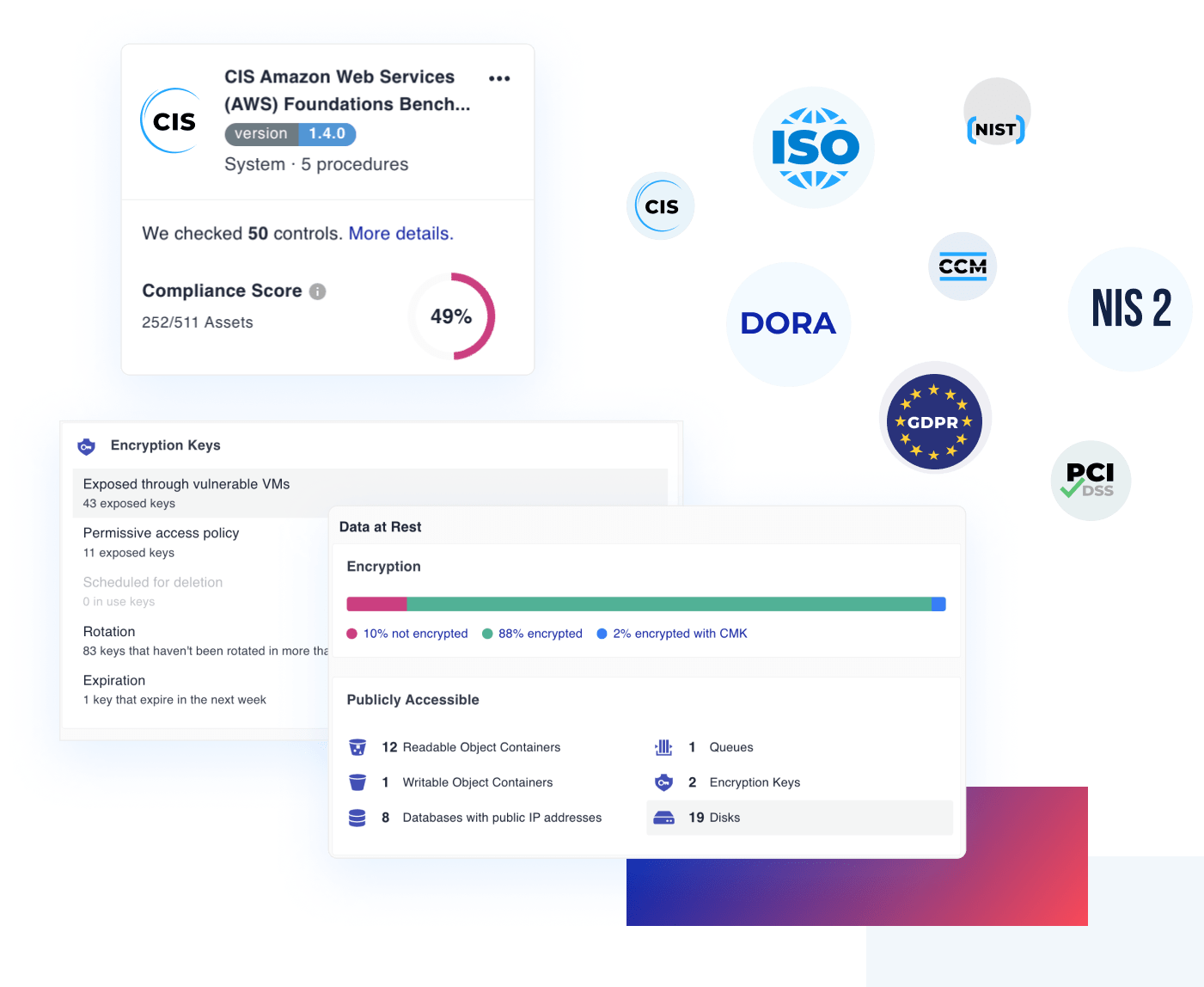
Extensive cloud misconfiguration
detection across all of your cloud assets
Analyze cloud misconfigurations
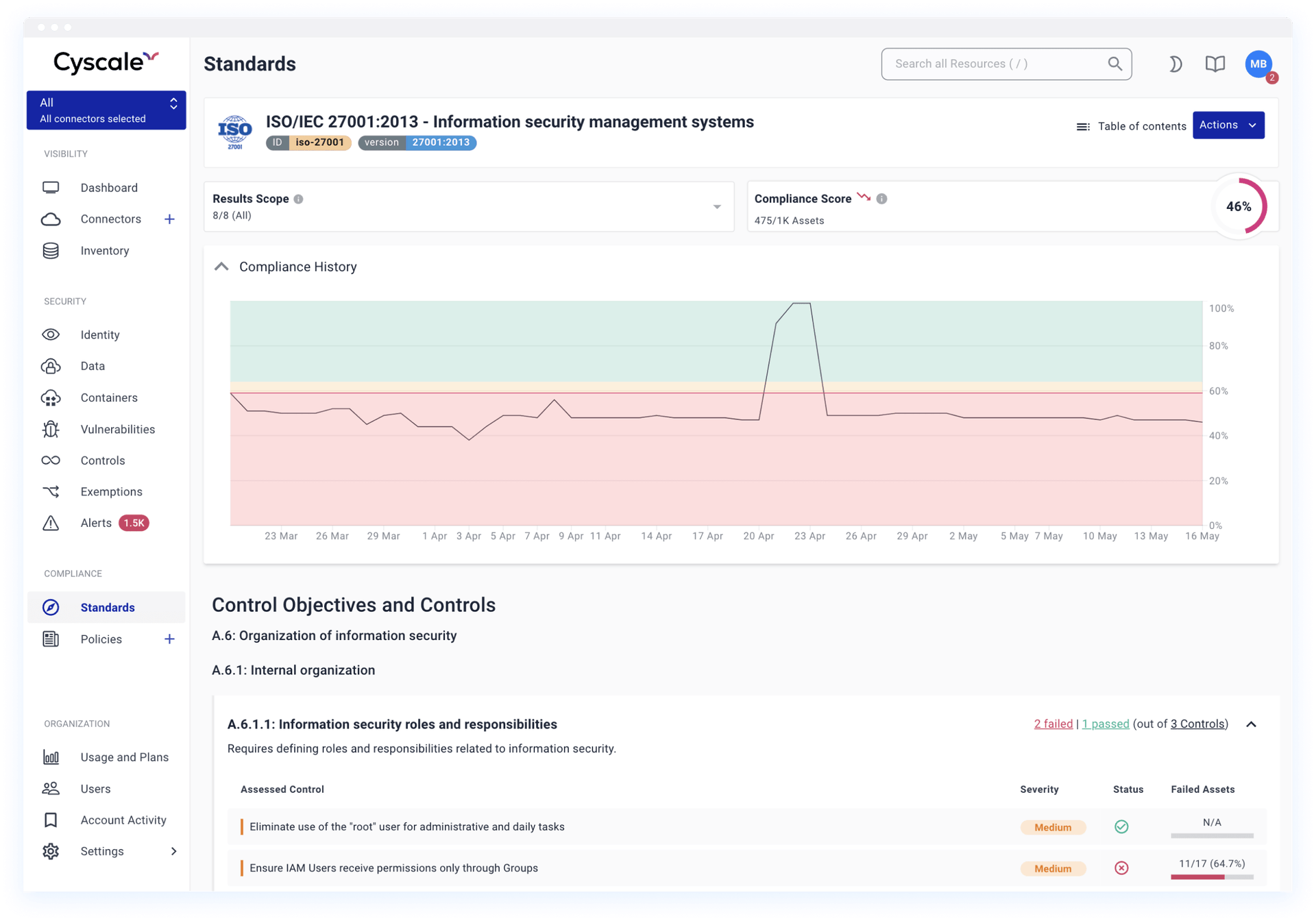
Analyze misconfigurations against the most popular industry and regulatory frameworks, including a wide range of CIS control benchmarks, ISO 27001, and SOC 2.
Ensure security and compliance
Prove alignment with the highest industry standards, enforce policies consistently across cloud providers and scale compliance efforts without overhead.
400+ unique configuration controls
Unique and customizable controls, including authentication, data protection, logging and monitoring, network configurations, system integrity, and more.
Prioritize misconfiguration risk
Contextual prioritization and remediation through our Security Knowledge Graph, which surfaces crucial issues based on the correlation of insights from a deep understanding of all your interlinked assets.
Get peace of mind with automated cloud security
RECOMMENDED ARTICLES
Misconfigurations
The Complete Guide
to Cloud Storage Misconfigurations
This guide helps CIOs, CISOs and security staff to understand the risk & dangers of data security breaches and the importance of a secure cloud storage infrastructure.