5 Steps to Improve Your Company’s Cloud Security Posture
Cloud Security Analyst at Cyscale
Friday, April 15, 2022

Securing your cloud environment can be a very difficult task.
When configuring and maintaining your cloud environment, mistakes and misconfigurations are bound to happen. And, because of that,
- understanding how cloud assets are interconnected,
- establishing correct policies,
- regulating access control
are all tasks that should be carefully approached when thinking about your company’s cloud.
Therefore, it is necessary to take some steps to make sure your company’s cloud is secure.
In order to minimize risks and secure your cloud environment, you need to manage your cloud security posture.
In this article, you will see how to improve it and provide a safe environment for your assets.
Here are some key actions that you need to take to make sure that your cloud is secure.
- Assure discovery and visibility of cloud assets
- Detect misconfigurations
- Implement remediation for findings
- Ensure logging and monitoring
- Assure compliance with security standards
Let us talk more about these tasks and how to accomplish them.
1. Assure discovery and visibility of cloud assets
Looking at many configurations at once may become overwhelming very fast.
It is hard to notice flaws in your security design if discovery and visibility are not assured.
Discovery and visibility in cloud imply being able to visualize cloud assets in an organized and easily readable way, for example in a dashboard.
Even more useful is when visibility for each asset is enriched by additional context that may be provided in a graph view.
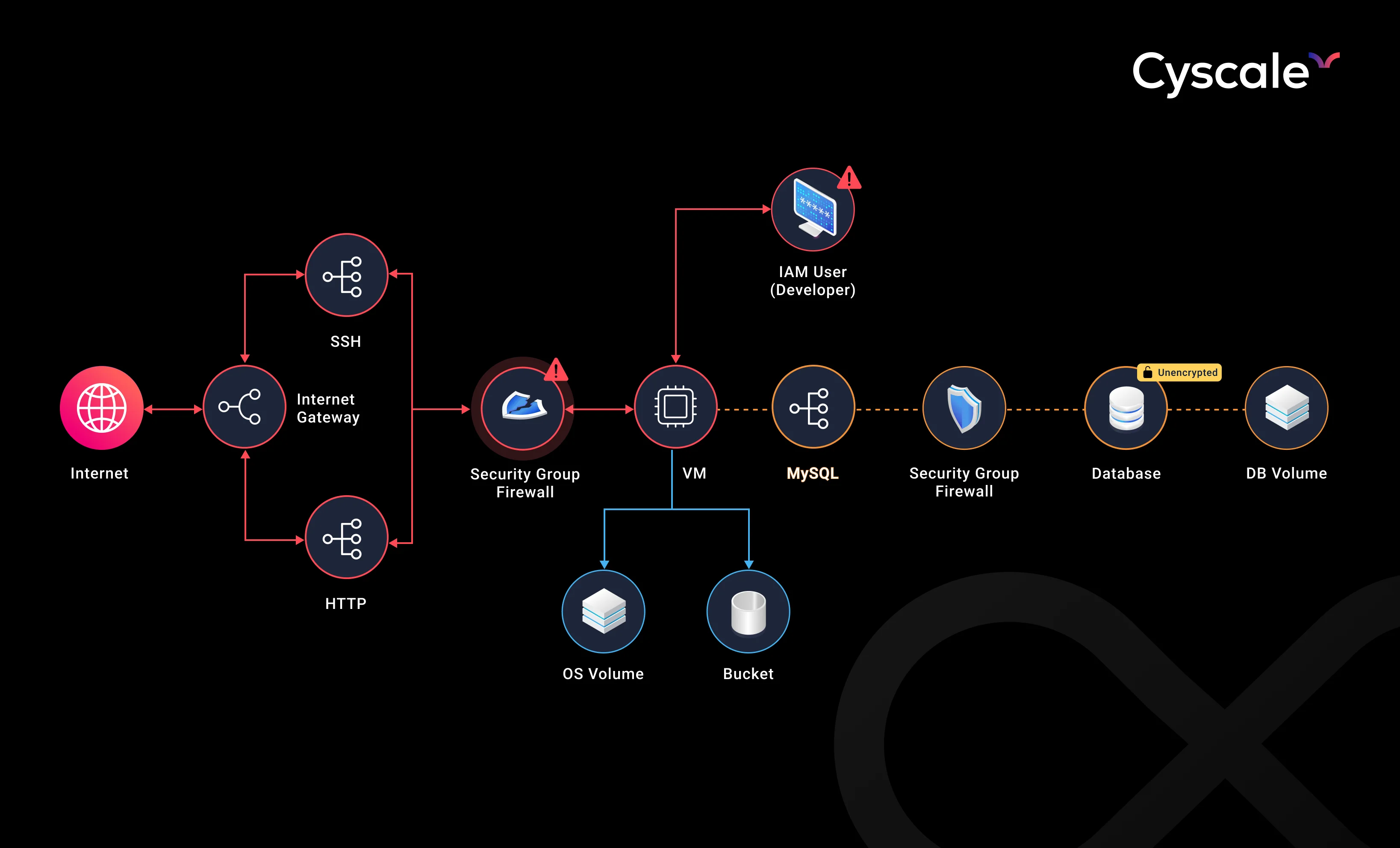
Looking at:
- policies,
- configurations,
- connections between assets
in a centralized fashion can help in pointing out:
- unnecessarily permissive rights
- vulnerabilities in your cloud configuration.
- odd changes in your infrastructure.
It is critical to make sure that visibility is satisfied, in order to enable threat discovery.
For example, a graph that maps networks of cloud assets. identities and workloads can help you properly understand relationships, properties, and types of assets in your cloud environment.
Visually examining the characteristics of your infrastructure may aid you in taking the right measures to improve security.
2. Detect misconfigurations
According to Continuity Central, misconfigurations in the cloud environment were the main cause of cloud security breaches in 2021. It is easy to overlook:
- a badly configured access list (ACL)
- a bad policy for access control
- an open port that should not be there, and others.
Humans make mistakes. Even a minor misconfiguration that does not impact the activity in your cloud may lead to catastrophic events such as:
- public access to your containers,
- malware intrusion,
- lateral movement.
Discovering these mistakes before they are exploited is critical.
Ideally, you should have an automated way to check for common cloud misconfigurations.
We will provide you with a solution later in this article to easily keep misconfigurations under control and be notified when new ones appear.
3. Implement remediation for findings
It is not enough to only discover threats in your design.
You need to also be able to remediate the flaws in your cloud infrastructure.
Knowing how to properly fix misconfigurations and vulnerabilities is a key factor in improving your cloud security.
Examples of misconfigurations remediations are:
- restricting overly permissive access to users,
- closing unnecessarily open ports,
- blocking inbound & outbound traffic.
4. Ensure logging and monitoring
It is very important to catch threats before they become incidents.
A good measure to take is keeping logs and documenting every event that occurs.
In this case, targeted alerts can save your company from disaster by pinpointing:
- misconfigurations
- suspicious activity
- attacks coming from outside.
Spotting threats immediately or within a short period of time may save your cloud environment from being breached.
5. Assure compliance with international standards
Making sure that your company is compliant with international standards such as ISO 27001 not only consolidates your data protection services but also shows your clients that you acknowledge the importance of cybersecurity.
Following best practices recommended by standards can greatly improve your cloud security posture.
However, fulfilling all of the requirements consistently to become compliant with an international standard is a very tedious and time-consuming job.
A solution to this would be automating controls and compliance checks that scan your platform for every requirement and show if you are fulfilling every request.
We have reached the end of the article and now you are probably wondering:
How do you implement all of the mentioned steps?
The tasks described above can be implemented using a CSPM product (Cloud Security Posture Management).
CSPM is a component of cloud security that analyzes your cloud environment and alerts you on what controls are failing in your infrastructure.
Your cloud security posture would be improved significantly and promptly when using a CSPM.
Cyscale is a CSPM that provides solutions to all of the problems raised in this article.
With Cyscale, you can:
- get an overview of your assets and configurations,
- easily manage misconfigurations,
- receive targeted and precise alerts,
- remediate accidents and flaws in your cloud environment faster,
- become compliant with international standards.
Start automating tasks, make these processes easier for you and generate reliable results, with Cyscale.
Cloud Security Analyst at Cyscale
Sabrina Lupsan merges her academic knowledge in Information Security with practical research to analyze and strengthen cloud security. At Cyscale, she leverages her Azure Security Engineer certification and her Master's in Information Security to keep the company's services at the leading edge of cybersecurity developments.
Further reading
Cloud Storage
Misconfigurations

Build and maintain a strong
Security Program from the start.
Cloud Compliance in
2025: An In-Depth Guide
The whitepaper talks about ISO 27001, SOC 2, PCI-DSS, GDPR, HIPAA.
Download WhitepaperShare this article
Stay Connected
Receive our latest blog posts and product updates.
TOP ARTICLES
CSPM
Our Compliance toolbox
Check out our compliance platform for cloud-native and cloud-first organizations:

LATEST ARTICLES
What we’re up to

Why the world needs Cyscale in a post-Wiz era





