5 CSPM Best Practices & Strategies
Cloud Security Analyst at Cyscale
Friday, July 15, 2022
In the context of a constantly growing trend of worldwide cyberattacks and breaches, every company needs to secure its cloud environment and make sure they have a robust cloud security posture.
This article will look at best practices and strategies to mitigate cybersecurity risks and understand the importance of a CSPM tool.
A CSPM (Cloud Security Posture Management) product is a component of cloud security that:
- uses controls to identify misconfigurations and vulnerabilities in a cloud environment,
- sends alerts to help companies promptly remediate findings,
- provides steps on how to fix misconfigurations,
- enables you to achieve compliance with international standards.
Best practices
The following best practices we recommend can be implemented and followed with a CSPM.
1. Ensure visibility of assets
If you have a large number of assets, it is challenging to guarantee discovery and visibility and to find security design issues.
Broad visibility and discovery of assets may help you identify:
- misconfigurations that may cause vulnerabilities in your system,
- poor access control,
- weak data security, and others.
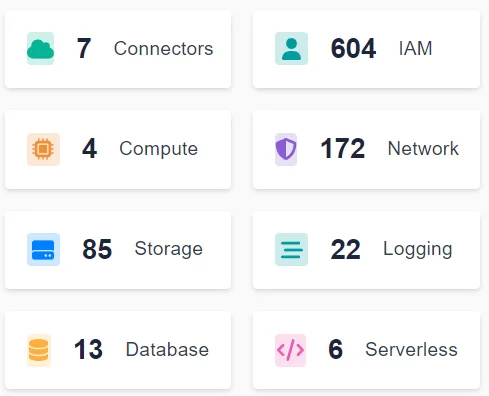
Below, you can see a section of Cyscale’s powerful dashboard, where you can also find the status of your controls, alerts, and others.
This inventory helps you keep track of assets and be aware of the different components in your cloud environment.
2. Classify assets and prioritize the most important ones
Asset classification is very important; it will help you prioritize the assets with high risk and high importance.
A company's security can be considerably improved by categorizing assets according to their risk and by setting remediation priorities.
3. Achieve compliance with frameworks such as GDPR, ISO 27001, PCI-DSS, and others.
A CSPM can help you achieve compliance by:
ensuring your cloud environment is implementing requirements and best practices,
providing evidence of your organization’s efforts and speeding up the auditing process.
There is a long list of international standards that regulate configurations of cloud environments:
- ISO 27001,
- GDPR,
- HIPAA,
- PCI-DSS,
- NIST, and many more.

4. Monitor your infrastructure
Identifying threats early is crucial to preventing incidents. Keep logs and document every action and event to be able to respond to threats as they appear.
Monitoring and logging your infrastructure can help you:
- notice odd behavior,
- identify misconfigurations,
- provide accountability for employees’ and customers’ actions.
5. Remediate findings quickly
Solving misconfigurations and responding to incidents promptly is essential – it can prevent a threat from becoming a breach.
Examples of misconfigurations remediations are:
- implementing strong encryption for sensitive data,
- eliminating administrator or root accounts that are not necessary,
- using access lists and policies to restrict unwanted traffic.
A CSPM can help you remediate failed controls and quickly patch your systems.
Cyscale is a CSPM that can help you implement the best practices described in this article and even more. You can use over 400 controls and powerful dashboards to:
- obtain visibility and discovery of your cloud environment,
- manage high priority assets,
- identify misconfigurations in a timely manner,
- ensure compliance with international standards,
- solve findings and ensure security.
Cloud Security Analyst at Cyscale
Sabrina Lupsan merges her academic knowledge in Information Security with practical research to analyze and strengthen cloud security. At Cyscale, she leverages her Azure Security Engineer certification and her Master's in Information Security to keep the company's services at the leading edge of cybersecurity developments.
Further reading
Cloud Storage
Misconfigurations

Build and maintain a strong
Security Program from the start.
Cloud Compliance in
2025: An In-Depth Guide
The whitepaper talks about ISO 27001, SOC 2, PCI-DSS, GDPR, HIPAA.
Download WhitepaperShare this article
Stay Connected
Receive our latest blog posts and product updates.
TOP ARTICLES
CSPM
Our Compliance toolbox
Check out our compliance platform for cloud-native and cloud-first organizations:

LATEST ARTICLES
What we’re up to

Why the world needs Cyscale in a post-Wiz era





