CNAPP Buyer’s Guide: How to Secure Your Cloud-Native Applications
Cloud Security Analyst at Cyscale
Monday, January 15, 2024

With the transition to the cloud, application architectures have shifted to make use of new technologies such as containers, Kubernetes, and serverless. But while these developments have made it easier than ever to deploy applications, they have dramatically changed the landscape in terms of security.
Since cloud-native applications are designed using a different architecture to traditional non-native applications, it is essential to understand how the key features of cloud-native applications introduce new and specific security concerns and are driving the adoption of the Cloud-Native Application Protection Platform (CNAPP) as a result.
How is cloud-native infrastructure different?
Cloud-native software is built in containerized environments, such as those managed with Kubernetes. Cloud-native applications are composed of microservices, which are components that communicate with each other through APIs (Application Programming Interfaces).
These technologies significantly increase scalability and flexibility in the cloud, but they introduce new concerns in terms of security along with a much larger attack surface area.
What is a CNAPP?
Due to the differences between native and non-native cloud applications, a CNAPP is becoming a necessary solution to cover the specific security needs of applications developed for the cloud.
Coined by Gartner, cloud-native application protection platforms (CNAPPs) are described as a unified and tightly integrated set of security and compliance capabilities designed to secure and protect cloud-native applications across development and production.
One of the key features being that CNAPPs consolidate several previously siloed capabilities, including container scanning, cloud security posture management, infrastructure as code (IaC) scanning, cloud infrastructure entitlement management (CIEM), runtime cloud workload protection and runtime vulnerability/configuration scanning, into one solution.
This guide will help you understand the most important features of a CNAPP that secure cloud-native applications and improve your organization’s cloud security posture.
A CNAPP combines multiple functionalities that are otherwise found in separate tools, including:
- CSPM (Cloud Security Posture Management)
- CWPP (Cloud Workload Protection Platform)
- CIEM (Cloud Infrastructure Entitlements Management)
- KSPM (Kubernetes Security Posture Management)
- Container Security
Get an overview of CNAPP capabilities
Visibility of cloud-native infrastructure
Whereas traditional environments relied largely on proprietary software, isolated hardware, and almost total control of the stack, cloud-native environments may stretch across multiple clouds, make use of open-source code, require identity-based segmentation, and feature ephemeral workloads.
As a result, context-aware visibility of all these assets and resources is crucial for identifying vulnerabilities in cloud-native applications. Not only is the surface area for attack dramatically increased, you also need to determine whether a vulnerability in one resource is innocuous or if it creates a toxic combination through its relationship with other assets.
A misconfigured API gateway that controls access to microservices may permit unauthorized access and serve as a jumping-off point to more resources, for example.
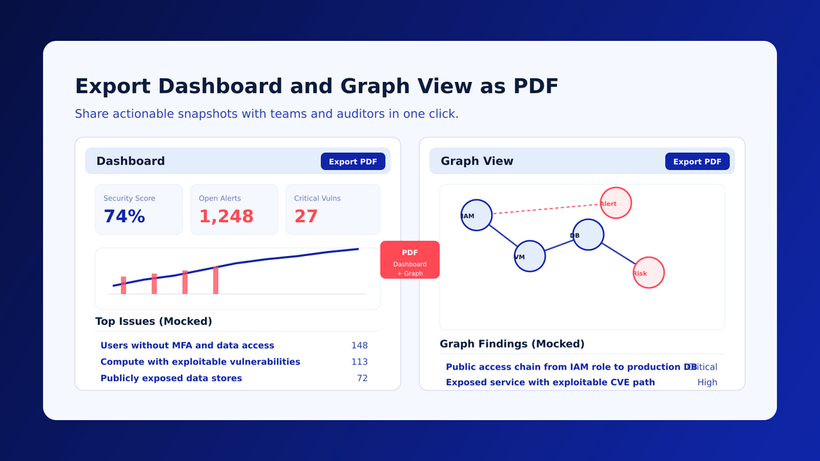
Therefore, the visibility features found in CSPM solutions are incorporated into CNAPP to identify and fix vulnerabilities in the cloud-native infrastructure. Usually, visibility comes in the form of comprehensive dashboards that can illustrate current security scores, assets that need your attention, and other elements that may help you understand your cloud.
Key considerations and questions:
- Does the CNAPP enable you to see all your cloud resources in one place, so as to be constantly aware of your cloud environment?
- Does it provide full coverage and visibility into your cloud estate and risks, including cloud configuration, workload, and identity?
- Does it bring your multi-cloud infrastructure together in one tool and deliver risk-aware context?
- Does it identify assets that might or have drifted from your organization’s compliance baseline?
Cloud-native security controls
Manually going through every cloud asset configuration to check for issues and vulnerabilities is tedious and error prone in smaller estates and impossible in large cloud environments where thousands of assets are in use. Don’t forget that the approach for AWS is different to that of Azure, is different to Google Cloud, and different again with Kubernetes.
A certified expert in one environment does not equal transferable skills to another.
To solve these challenges, automatic security controls are used to check for misconfigurations and vulnerabilities and either automate the remediation of or provide guidance to address issues. The application of automation, using Machine Learning and AI, not only saves considerable time but reduces the risk of human error, making it a crucial aspect of CNAPP.
Key considerations and questions:
- Does the CNAPP provide contextual triaging and prioritization or send targeted alerts for high-priority assets to reduce and relieve alert fatigue?
- Does it detect misconfigurations and vulnerabilities in real-time, enabling you to react and fix findings quickly, saving your organization from a breach?
- Does it deliver efficient remediation steps on detected issues?
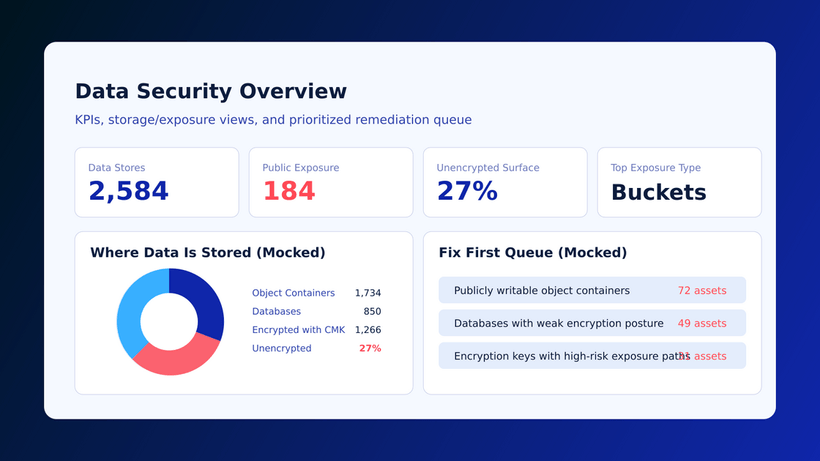
Data security in the cloud
Due to the dynamic nature of cloud-native applications with ephemeral workloads and infrastructure that is scaling up and down quickly, sensitive data may be unwittingly exposed. Through DSPM (Data Security Posture Management) capabilities, CNAPPs can help keep track of data stores and provide actionable suggestions for your organization to secure your crown jewels.
A CNAPP will detect and highlight unencrypted storage resources, cryptographic keys with insecure configurations or upcoming expirations, assets that are publicly accessible, and other vulnerabilities or misconfigurations that may leave your organization’s sensitive data exposed.
Key considerations and questions:
- Are the Data Security Dashboard capabilities of the CNAPP capable of pinpointing blind spots in your infrastructure?
- Some cloud providers encrypt data in storage resources by default, while others do not so it is easy to overlook what you think you know and miss important details. Does the CNAPP help you understand your encryption status?
- Instead of dealing with cryptographic key rotation and deletion, some CNAPPs show you what keys need to be rotated and when. Does the CNAPP provide this capability?
Container image scanning
Part of the process of securing containers is image scanning. This is essential because it checks container images for misconfigurations and vulnerabilities and reduces the risk of deploying containers with security issues.
Retroactively, a CNAPP can identify which container images have vulnerabilities and where those images are running in your infrastructure.
For example, if a container image uses an unpatched version of Log4J, this could introduce a critical vulnerability in your cloud environment. It may allow an attacker to execute arbitrary code on the system running the container, compromising the data and applications in that container.
Key considerations and questions:
- Does the CNAPP check container images for vulnerabilities to avoid introducing vulnerabilities in your infrastructure?
- Does the CNAPP help you understand who has permissions over containers to prevent unauthorized access?
- Are you able to monitor for and identify any misconfigurations developers might have missed when spinning up containers?
Cloud workloads protection
The Cloud Workload Protection Platform (CWPP) component of a CNAPP helps companies discover vulnerabilities and correlate them with cloud misconfigurations. Using a CWPP, you mitigate risk across multi-cloud environments by identifying vulnerabilities documented in CVEs and pinpointing which misconfigurations have exposed your cloud infrastructure to them.
To secure cloud-native applications, a CWPP tool analyzes:
- VMs
- Containers
- Serverless functions, and others.
Key considerations and questions:
- Does the CNAPP enable you to see running workloads in one dashboard to easily keep you up to date with your organization’s activity all the time?
- Does it help you prioritize vulnerable workloads efficiently based on severity to ensure effective remediation measures?
- Does it automatically keep up with emerging threats, so you don’t have to check the news all the time? Your CNAPP should do the work for you by constantly checking your workloads for newly discovered vulnerabilities.
Kubernetes cluster inspection
Cluster inspection is a feature of Kubernetes Security Posture Management (KSPM) that provides visibility into the security posture of a Kubernetes cluster by inspecting its configuration and runtime behavior.
Misconfigurations that can be found using cluster inspection are:
- Unauthorized access
- Missing patches
- Insecure network configurations, and others.
Key considerations and questions:
- Does the CNAPP give you visibility of your Kubernetes objects?
- Does it help you assess your cluster based on the CIS Kubernetes benchmark, which contains up-to-date and industry-standard best practices?
- Does it detect vulnerabilities in your Kubernetes cluster with no need for manual effort from your team? You should be able to see where you have Kubernetes images with vulnerabilities and where those images are deployed.
CIEM and IAM: Access management
IAM (Identity and Access Management) is an essential component of cloud-native applications security specific to the CIEM (Cloud Infrastructure Entitlement Management) part of the platform. With complex cloud environments, keeping track of users and services, their different access levels, and what impact certain permissions have can become challenging.
For cloud-native applications, IAM can become a very complex aspect of cloud security due to, but not limited to, the following aspects:
- Cloud-native applications are highly scalable, and identities and access levels may change rapidly, making them more difficult to manage
- Cloud-native software may run across multi-cloud environments as well as on-premises
- The microservices architecture can increase the difficulty of managing identities at the service level
Companies can use a CNAPP solution to better secure their cloud in terms of identity and access management.
Best practices regarding IAM:
- Implement multi-factor authentication for all users. This measure adds an additional layer of security by requesting at least two forms of identification
- Use role-based access control (RBAC) to limit access to sensitive data to authorized users and obtain high granularity
- Comply with the Least Privilege Principle to restrict access to the lowest privilege necessary for the user to do their job
- Assign permissions at group level and assign well-defined rules and privileges to groups. This decreases the risk of data breaches.
Key considerations and questions:
- Does the CNAPP identify any drifts from your company’s security or compliance posture using a powerful IAM dashboard that pinpoints users with issues, such as the ones that do not have MFA enabled?
- Does the CNAPP give you an understanding of your password policies and identify if users have old passwords?
- Does it help you understand if users or groups have more permissions than necessary?
- Does the CNAPP support you in performing effective access reviews that don’t take all day and require no manual work?
- Does it help you gain confidence in your organization’s security posture?
Compliance
CNAPP solutions help companies in their compliance journey. The CSPM (Cloud Security Posture Management) component of CNAPP provides reporting and policy management features that help companies meet the requirements of various compliance frameworks.
To become compliant, companies use CNAPP tools to perform assessments in preparation for audits. Some of the most popular accredited standards a CNAPP should provide support for are are:
- ISO 27001
- SOC 2
- GDPR
- PCI-DSS
- HIPAA
- NIST
Other standards like DORA are becoming increasingly important for some sectors, and there are regional equivalents of some regulations like Brazil’s LGDP data protection laws.
Key considerations and questions:
- Does the CNAPP help you track your compliance progress in real-time and ensure you are able to understand how your organization is doing in terms of compliance posture?
- Does the CNAPP keep a track record of your efforts that can be presented during an audit?
- Are all of your organization's cloud resources tracked in one place, so you know that the compliance assessment is comprehensive and accurate and you're not missing anything?
- Can you view your compliance score at-a-glance and at any time?
- Are you able to export detailed reports to help explain your security and compliance posture to other stakeholders or to help you make a case to the board?
Summary: CNAPP as a critical part of cloud-native security
As cloud-native application development has penetrated the market, it has not only expanded the infrastructure estate but also the number of teams involved, from devops, to platform engineers, cloud architects, security experts, compliance practitioners, and more.
Likewise, security solutions have evolved in tandem, moving beyond the more static nature of the CSPM, to the more dynamic capabilities of a CNAPP, with an integrated, lifecycle security and compliance approach to protecting workloads and applications.
The vendor landscape is competitive and vendor portfolios have either grown through acquisition or original development. The result is that many established vendor CNAPP offerings are bolted together point solutions with little or no integration.
Cloud-native organizations going down this route will need to ensure they have the resources available to learn and operate several different tools and even take on some of the work around correlation and context in cloud security.
The main concern with challenger or incoming CNAPP vendors, on the other hand, might be a lack of maturity in the components, even though the platform itself is designed with integration in mind.
Organizations will need to carefully assess the capabilities of the CNAPP solution to ensure it meets their specific needs, without requiring too many resources or investments, and with room for future growth.
That said, CNAPP (Cloud-Native Application Protection Platform) solutions are regarded as a critical security component for cloud-native applications. Due to the dynamic nature of the cloud, its high scalability, and different architecture, traditional security measures may not be sufficient.
Choosing a CNAPP
Overall, CNAPP solutions offer:
- Visibility
- Compliance
- Data security
- Runtime protection
- Container image scanning
- Kubernetes cluster inspection
- IAM
Cyscale’s CNAPP is designed to protect your entire stack, VMs (virtual machines), containers, and serverless, on any cloud environment, enabling you to confidently accelerate innovation.
By analyzing cloud configuration, workload, and identity, it identifies the most critical attack vectors that pose a threat, rather than overwhelming you with numerous alerts for vulnerabilities, permissions, and exposed services.
With our security platform, you can prioritize and address the most significant security risks, ensuring application security and the integrity of your cloud infrastructure.
You can sign up for a no commitment cloud risk assessment here, and check the health of your cloud estate in a matter of minutes.
Or explore each of the components that make up an effective CNAPP in our video tours, here.

Cloud Security Analyst at Cyscale
Sabrina Lupsan merges her academic knowledge in Information Security with practical research to analyze and strengthen cloud security. At Cyscale, she leverages her Azure Security Engineer certification and her Master's in Information Security to keep the company's services at the leading edge of cybersecurity developments.
Further reading
Cloud Storage
Misconfigurations

Build and maintain a strong
Security Program from the start.
Cloud Compliance in
2026: An In-Depth Guide
The whitepaper talks about ISO 27001, SOC 2, PCI-DSS, GDPR, HIPAA.
Download WhitepaperShare this article
Stay Connected
Receive our latest blog posts and product updates.
TOP ARTICLES
CNAPP
Our Compliance toolbox
Check out our compliance platform for cloud-native and cloud-first organizations:

LATEST ARTICLES
What we’re up to

Cyscale on AWS Marketplace Simplifies CNAPP Procurement and Deployment