Introducing the New Data Security Dashboard!
Cloud Security Analyst at Cyscale
Thursday, December 15, 2022
We have released a new, powerful Data Security Dashboard to provide the visibility you need for your cloud. The Dashboard displays information about:
- Encryption,
- The management of cryptographic keys,
- Publicly accessible storage assets such as VMs, databases, buckets, and others,
- Databases and misconfigurations related to them,
- Containers such as blobs and buckets that may vulnerable, and others.
These DSPM (Data Security Posture Management) capabilities enable users to detect attack paths for data storage assets and quickly mitigate them.
The first section of the dashboard shows us the percentage of storage assets that are:
- unencrypted,
- encrypted with provider-managed-key, and
- encrypted with CMK (Customer Managed Key).
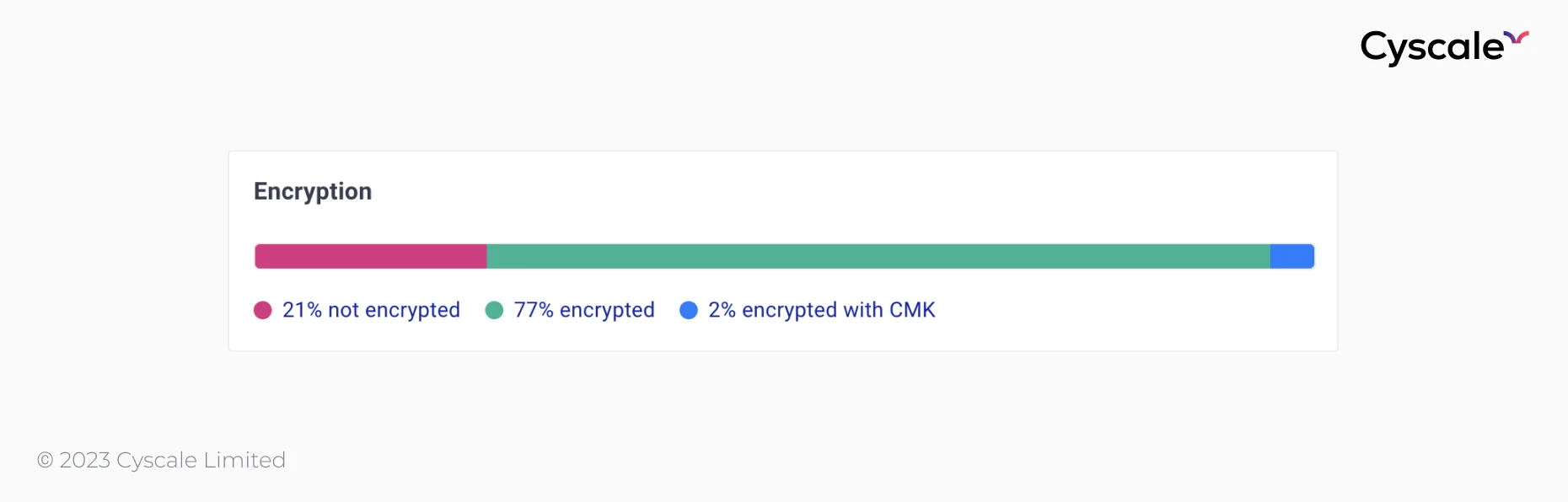
This card is a good indicator of progress, and, by clicking on each section of the status bar, we see which assets fit in each of those states. Using this feature, you are at a click away from finding out which of your storage cloud assets are unencrypted.
The next section contains the Publicly Accessible card, which provides visibility over a multitude of assets, as you can see in the image below. When you click on each element, you see a list of affected assets, along with the associated risk.
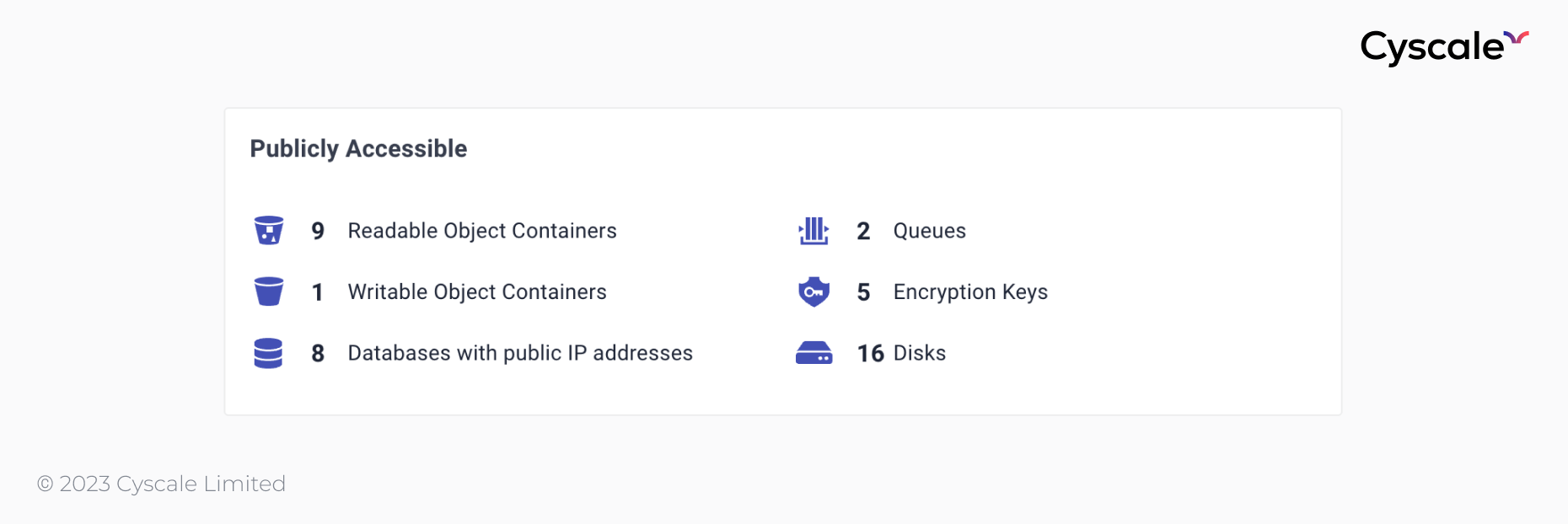
Let’s look at this feature in more detail to understand how this helps secure your cloud infrastructure.
The “Readable Object Containers” and “Writable Object Containers” refer to storage assets such as buckets and blobs. Object containers should not be publicly accessible unless it is necessary, since individuals could then read or overwrite possibly sensitive data without having to perform any kind of authentication or authorization.
The next item in this section highlights database instances that have public IP addresses. Databases should be configured with private IP addresses to reduce attack surface and increase security.
The last items in this list are publicly accessible:
- queues,
- encryption keys, and
- disks.
Cloud queues act like buffers to prevent data loss when services are too busy and cannot process incoming messages, and therefore should not be publicly accessible to prevent data leakage or data tampering. The control regarding encryption keys checks for attached policies that may allow public access to the key. The other control ensures there are no disks attached to VMs reachable from the internet.
The next card on the Data Security Dashboard provides an overview of the encryption keys used in your cloud infrastructure. Cryptographic key management is a very important but sometimes overlooked aspect of the encryption process.
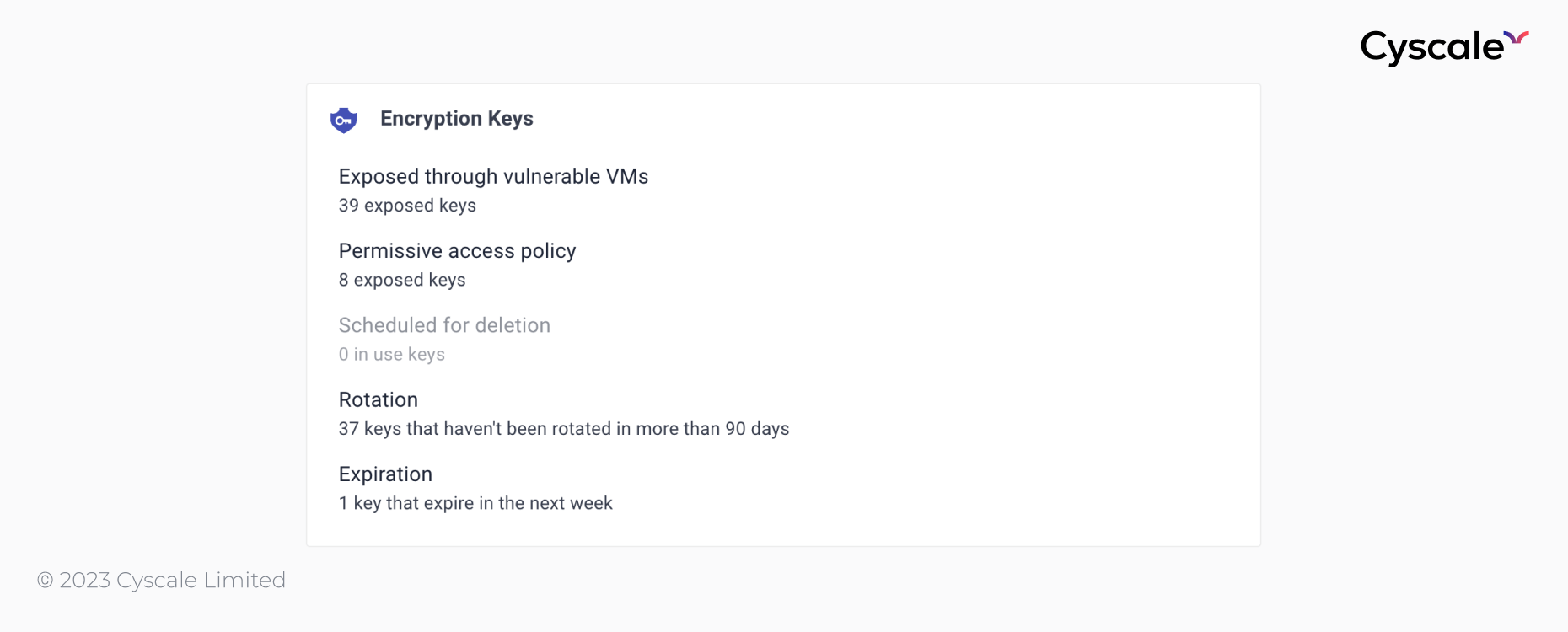
Cyscale checks if the encryption keys are stored on a vulnerable VM or if they have a permissive access policy to identify possible attack paths. Moreover, important information is highlighted, such as:
- keys that are in use and are scheduled for deletion,
- keys that haven’t been rotated in a long time, and
- keys that will expire soon.
The next two sections in this dashboard focus on object containers, such as buckets or blobs, and on databases. Here, you can see some of the categories of vulnerabilities Cyscale has identified and checked your cloud environment against.
The first card presents the state of your object containers.
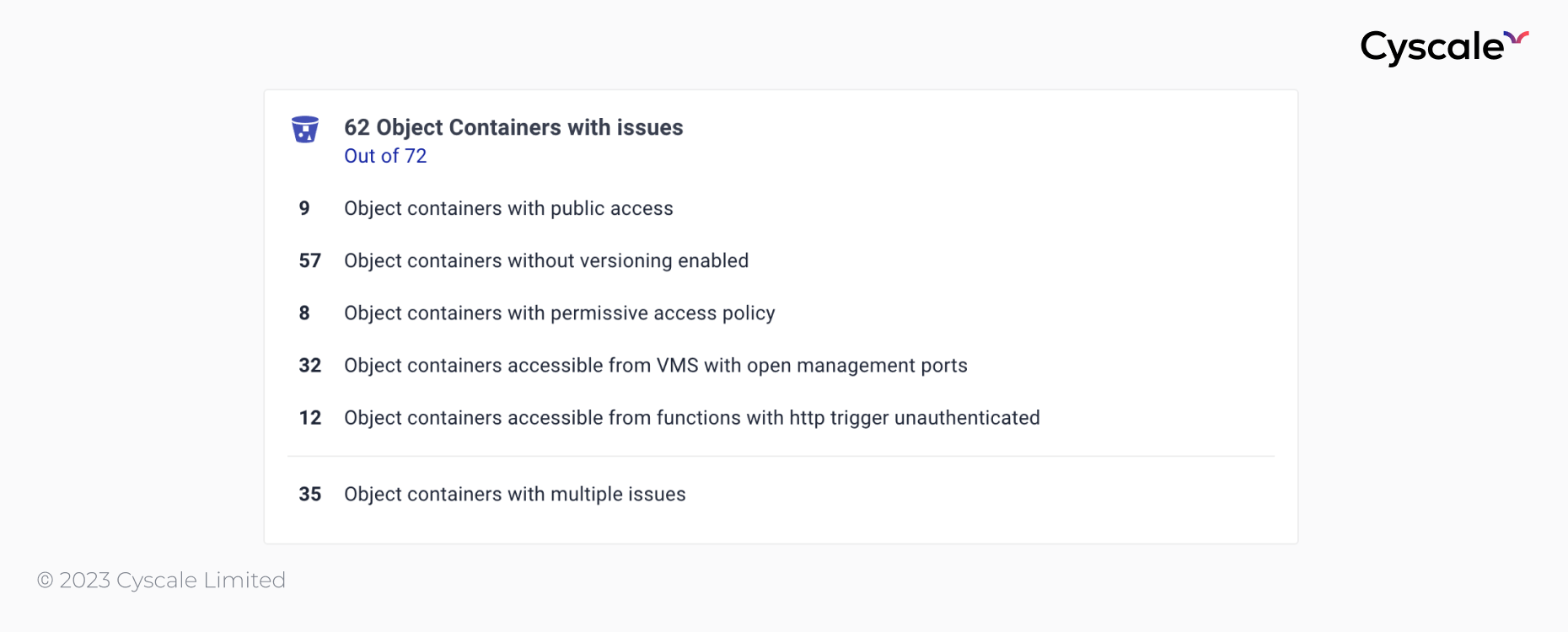
Using this feature, we identify attack paths that may compromise your cloud assets and help you solve them.
For example, a common attack is exploiting VMs that have open management ports. If you have a VM that has permissions on a bucket, and that VM is compromised, your bucket may be compromised as well.
Using the Cyscale Knowledge Graph, you can see that the VM named "sql-instance" has an instance profile that gives it full access to the bucket on the far right, and the VM also has port 22 (SSH) open. The VM is thus connected to the internet and therefore puts the data stored in the bucket at risk.
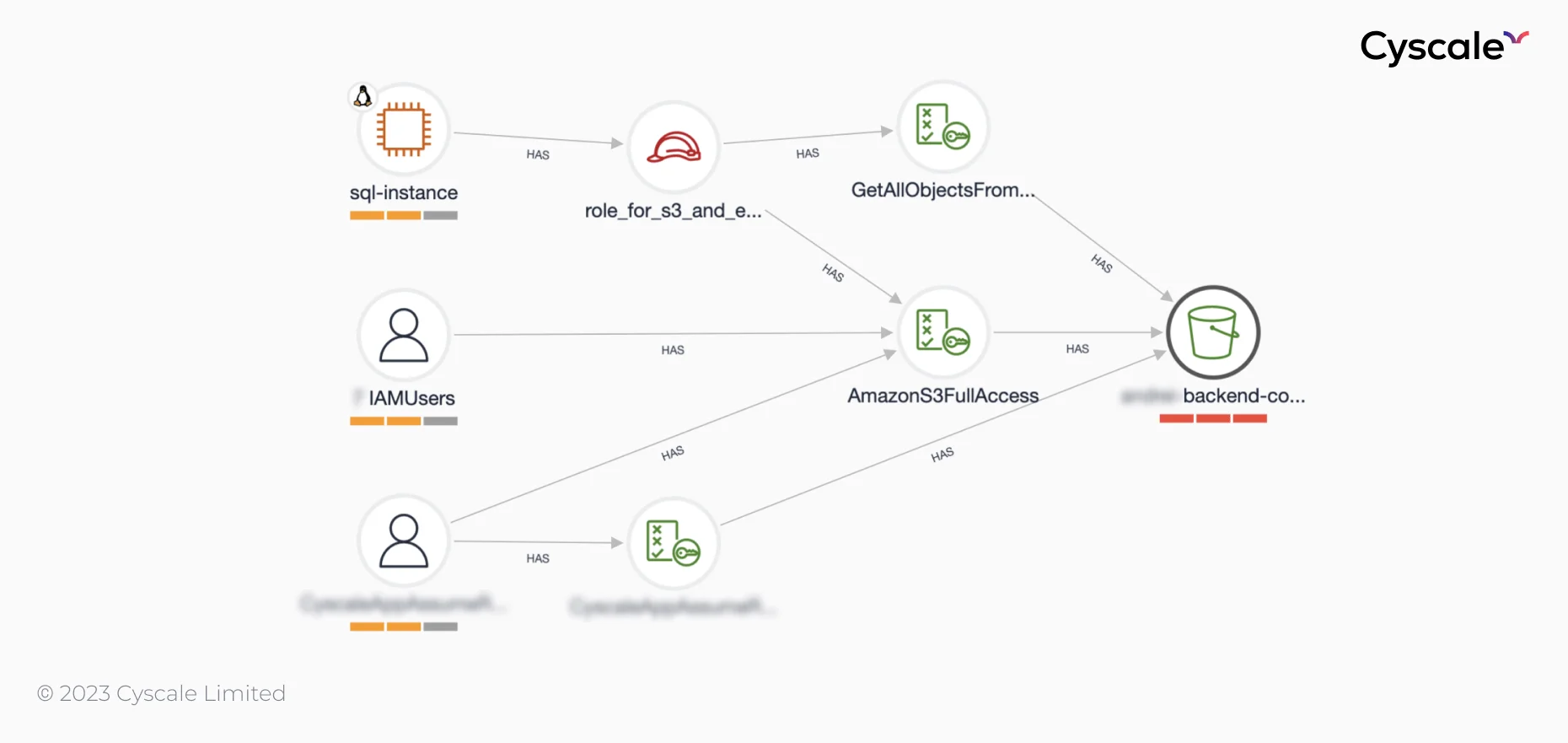
Other critical issues highlighted for object containers include:
- Enabling public access to storage assets,
- Having an overly-permissive access policy,
- Not enabling versioning, and others.
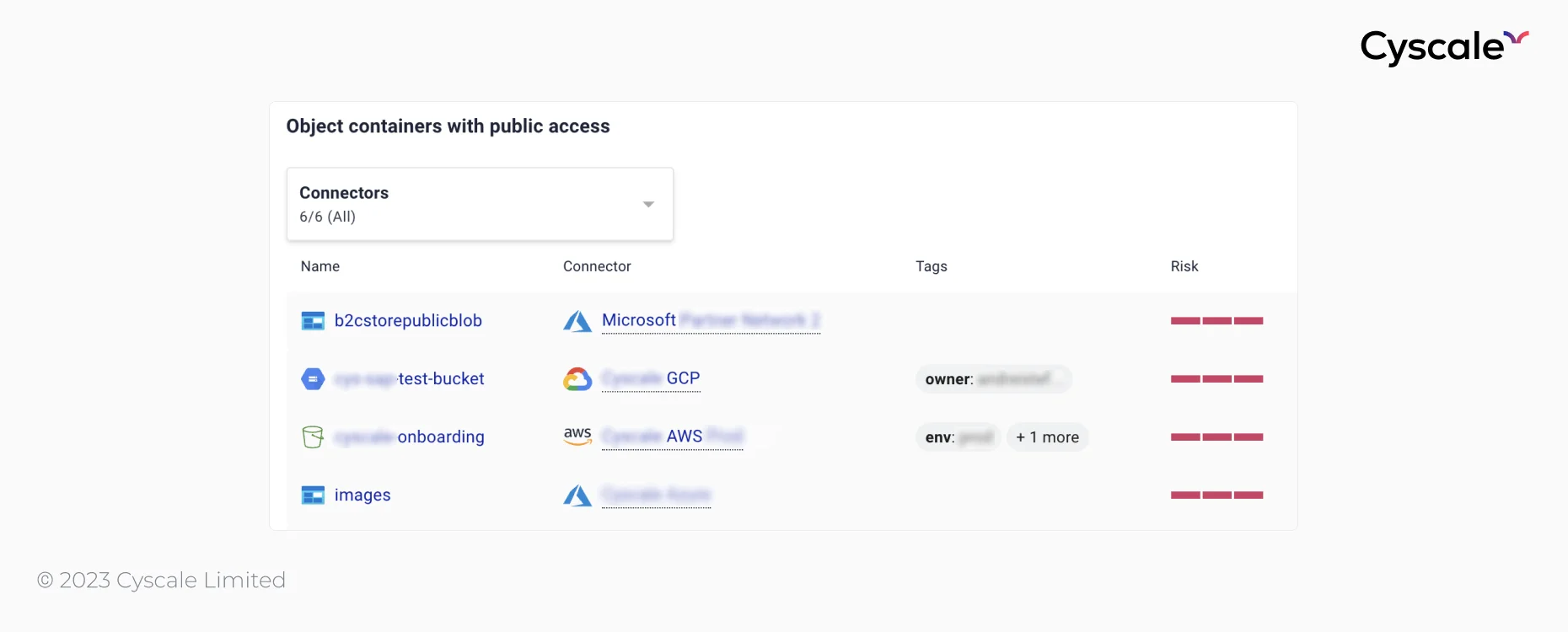
Clicking on “Object containers with public access”, we get a list of misconfigured assets as well as details like:
- Connectors, which represents the cloud or identity provider account,
- Tags,
- Risks.
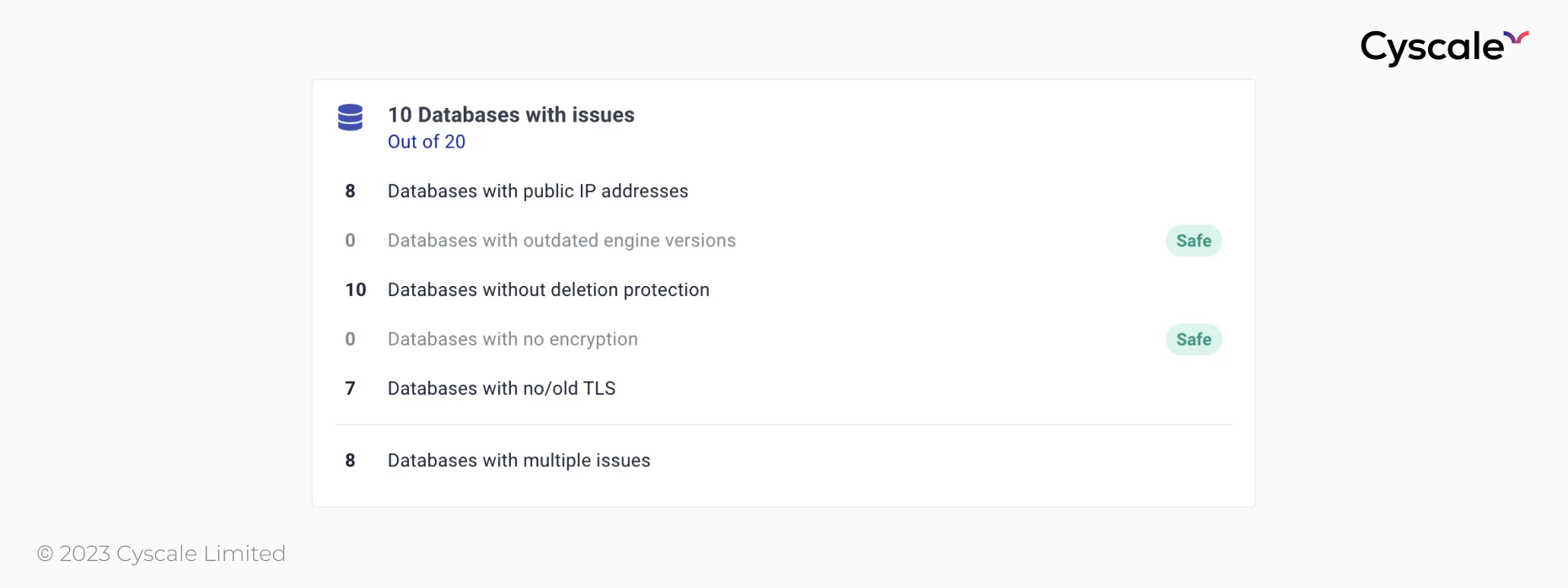
Moving on to the databases card, using controls, Cyscale checks for the following misconfigurations:
- Databases with public IP addresses,
- Databases with outdated engine versions,
- Databases without deletion protection,
- Databases with no encryption,
- Databases with no/old TLS.
Use the multitude of features present in the Cyscale Data Security Dashboard to eliminate data exposure through data storage misconfigurations. Check out our product in the playground or schedule a demo with us to start your cloud security journey!
Cloud Security Analyst at Cyscale
Sabrina Lupsan merges her academic knowledge in Information Security with practical research to analyze and strengthen cloud security. At Cyscale, she leverages her Azure Security Engineer certification and her Master's in Information Security to keep the company's services at the leading edge of cybersecurity developments.
Further reading
Cloud Storage
Misconfigurations

Build and maintain a strong
Security Program from the start.
Cloud Compliance in
2025: An In-Depth Guide
The whitepaper talks about ISO 27001, SOC 2, PCI-DSS, GDPR, HIPAA.
Download WhitepaperShare this article
Stay Connected
Receive our latest blog posts and product updates.
TOP ARTICLES
Product
Our Compliance toolbox
Check out our compliance platform for cloud-native and cloud-first organizations:

LATEST ARTICLES
What we’re up to

Why the world needs Cyscale in a post-Wiz era





