CONTENTS
Kubernetes Security: Best Practices for SMEs
CEO & Founder at Cyscale
Wednesday, June 12, 2024
Businesses of all sizes are adopting cloud-native technologies to enhance agility, scalability, and efficiency. Among these technologies, Kubernetes has emerged as a leading platform for container orchestration, enabling organizations to manage and deploy applications with unprecedented ease and speed.
However, with the growing reliance on Kubernetes comes a need for strong security measures, particularly for small and medium-sized enterprises (SMEs) that may lack the extensive resources of larger corporations. This guide dives into the best practices for Kubernetes security tailored specifically for SMEs, with a focus on real-time threat detection and response to help protect your digital environment and ensure seamless operations.
Overview of Kubernetes and its importance
Kubernetes, an open-source platform originally developed by Google, has become the de facto standard for automating the deployment, scaling, and management of containerized applications. Its modular architecture and powerful features enable businesses to build resilient, scalable infrastructure, and facilitate continuous delivery and DevOps practices.
For SMEs, Kubernetes offers several key benefits:
- Scalability: Easily scale applications up or down based on demand without significant manual intervention.
- Efficiency: Optimize resource utilization, leading to cost savings and better performance.
- Portability: Deploy applications across various environments, whether on-premises, in the cloud, or in hybrid settings.
- Resilience: Ensure high availability and fault tolerance through automated failover and self-healing capabilities.
These advantages make Kubernetes a valuable asset for SMEs looking to stay competitive and innovate rapidly in their respective markets.
As SMEs increasingly adopt Kubernetes, they also become more attractive targets for cloud threats. Unlike large enterprises, SMEs often operate with limited security budgets and smaller IT teams, making them more vulnerable to attacks. The consequences of a security breach can be devastating, ranging from financial losses and reputational damage to regulatory penalties and operational disruptions.
Several factors contribute to the growing need for Kubernetes security in SMEs:
- Increased Attack Surface: Kubernetes environments, with their numerous components and configurations, present a larger attack surface.
- Complexity: The complexity of managing Kubernetes security can overwhelm smaller IT teams, leading to potential misconfigurations and vulnerabilities.
- Data Sensitivity: SMEs handle increasingly sensitive data, from customer information to proprietary business data, which must be protected against breaches.
- Compliance Requirements: Adherence to regulatory standards and industry-specific compliance mandates necessitates stringent security practices.
A. Understanding Kubernetes Security
Kubernetes security is an interdisciplinary field that contains a range of strategies and practices designed to protect containerized applications and the underlying infrastructure.
Basic Concepts of Kubernetes Security
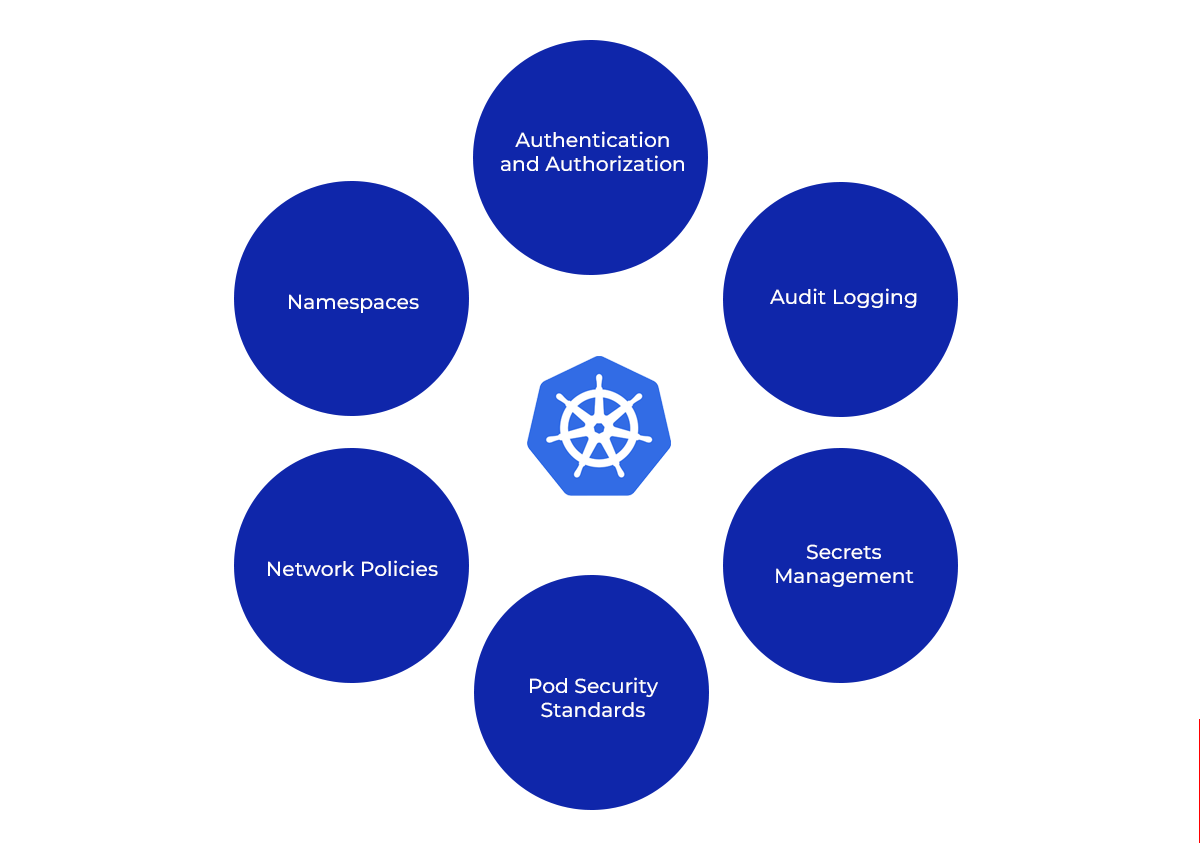
1. Authentication and Authorization:
- Authentication: Ensures that users and service accounts are who they claim to be. Kubernetes supports multiple authentication mechanisms, including client certificates, bearer tokens, and integrations with external identity providers.
- Authorization: Controls access to resources based on the authenticated identity. Kubernetes uses Role-Based Access Control (RBAC) to manage permissions, defining what actions users and service accounts can perform within the cluster.
2. Namespaces:
Namespaces provide a way to divide cluster resources between multiple users or teams. They help in organizing resources and applying security policies at a granular level, ensuring that different projects or environments (e.g., development, testing, production) are isolated from each other.
3. Network Policies:
Network policies in Kubernetes control the traffic flow between pods and services. They are essential for implementing micro-segmentation, allowing you to define which pods can communicate with each other and which are restricted, thereby reducing the attack surface.
4. Pod Security Standards:
Kubernetes offers pod security standards to enforce security contexts and configurations at the pod level. These standards include setting constraints on privilege escalation, running as a non-root user, and limiting access to the host's filesystem and network.
5. Secrets Management:
Kubernetes provides mechanisms to securely store and manage sensitive information, such as passwords, tokens, and keys, using Secrets. This ensures that sensitive data is protected and not hardcoded into application code or configuration files.
6. Audit Logging:
Audit logging is critical for monitoring and recording all interactions with the Kubernetes API. These logs provide an audit trail that can be used for forensic analysis and compliance reporting, helping to detect and investigate suspicious activities.
Common Security Challenges in Kubernetes Environments
1. Misconfigurations:
one of the most common security issues in Kubernetes environments. These can arise from incorrect settings in network policies, RBAC roles, or pod security contexts, potentially exposing the cluster to unauthorized access or attacks.
2. Vulnerabilities in Container Images:
Using outdated or insecure container images can introduce vulnerabilities into your Kubernetes environment. It's essential to regularly scan images for known vulnerabilities and apply updates or patches promptly.
3. Insufficient Network Segmentation:
Without proper network segmentation, malicious actors can move laterally within the cluster once they gain a foothold. Implementing and enforcing robust network policies is crucial to limit communication pathways and contain potential breaches.
4. Inadequate Access Controls:
Poorly managed access controls can lead to unauthorized access and privilege escalation. Ensuring that RBAC policies are correctly configured and regularly reviewed is vital to maintaining a secure Kubernetes environment.
5. Data Exfiltration:
Protecting sensitive data from being exfiltrated by malicious actors is a significant challenge. This requires robust encryption practices, both in transit and at rest, as well as stringent access controls and monitoring mechanisms.
6. Complexity and Lack of Visibility:
The inherent complexity of Kubernetes can make it challenging to achieve comprehensive visibility into all aspects of the environment. This can hinder the detection and response to security incidents. Utilizing centralized logging and monitoring tools can help overcome this challenge.
7. Insecure Default Settings:
Kubernetes, by default, may have configurations that are not secure enough for production environments. It's important to review and harden these settings to align with best security practices.
See how Cyscale helps you detect and respond to security threats in Kubernetes clusters.
B. Best Practices for Kubernetes Security
Securing your Kubernetes environment requires an approach that addresses multiple layers of security. This section outlines best practices across key areas, including network security, pod security, cluster security, and configuration management to help SMEs build and maintain a secure Kubernetes deployment.
Network Security
Securing Network Policies
- Define Clear Policies: Use Kubernetes Network Policies to define which pods can communicate with each other and which cannot. This helps to limit the potential spread of malicious activity within the cluster.
- Least Privilege Principle: Apply the principle of least privilege to network policies. Allow only the minimum necessary communication between pods and services.
- Regular Audits: Regularly review and update network policies to ensure they reflect the current needs and architecture of your applications.
Implementing Network Segmentation
- Segregate Sensitive Workloads: Separate sensitive or critical workloads into different namespaces or clusters. This limits the impact of a potential security breach.
- Use Dedicated Networks: Implement dedicated networks for different parts of your application (e.g., frontend, backend) to isolate them from each other.
- Zero Trust Networking: Adopt a zero trust approach where every communication within the network must be authenticated and authorized, minimizing the risk of lateral movement by attackers.
Pod Security
Enforcing Pod Security Standards
- Security Contexts: Define security contexts for your pods to control privileges. For instance, run containers as non-root users and restrict the capabilities they have.
- Pod Security Admission: Utilize Pod Security Admission (formerly known as Pod Security Policies) to enforce security standards across your cluster, ensuring that only compliant pods are deployed.
Managing Pod Security Policies
- Regular Reviews: Continuously review and refine your pod security policies to adapt to new threats and changing application requirements.
- Policy Automation: Use automation tools to enforce pod security policies consistently across all environments, reducing the risk of human error.
Cluster Security
Securing Kubernetes Clusters
- API Server Protection: Secure access to the Kubernetes API server using strong authentication and authorization mechanisms. Limit access to the API server to only those who need it.
- Etcd Security: Protect the etcd datastore by encrypting data at rest and ensuring access is restricted to only those who need it.
- RBAC Configuration: Implement Role-Based Access Control (RBAC) to manage permissions within the cluster. Regularly audit RBAC policies to ensure they are up-to-date and reflect the principle of least privilege.
Regular Cluster Audits and Compliance
- Audit Logs: Enable and regularly review audit logs to monitor access and modifications to the cluster. In case of a security incident, use these logs for forensic analysis.
- Compliance Checks: Perform regular compliance checks against industry standards and regulations relevant to your business. Use automated tools to assist with continuous compliance monitoring.
- Third-Party Audits: Consider engaging third-party security experts to conduct periodic security assessments and penetration tests to uncover potential vulnerabilities.
Configuration Management
Managing Configuration as Code
- Infrastructure as Code (IaC): Use IaC tools like Terraform or Ansible to manage Kubernetes configurations. This ensures that your configurations are version-controlled and can be rolled back if necessary.
- Version Control: Store all configuration files in a version control system like Git. This enables tracking changes and securely collaborating on configurations.
- Code Reviews: Implement code review processes for configuration changes to catch potential security issues before they are applied to the cluster.
Continuous Monitoring for Misconfigurations
- Automated Scanning: Utilize automated tools to continuously scan your Kubernetes configurations for misconfigurations and compliance violations. Tools like kube-bench and kube-hunter can help identify and remediate security issues.
- Alerting and Reporting: Set up alerting mechanisms to notify your team of any detected misconfigurations or policy violations. Regular reports can help track your cluster's security posture over time.
- Remediation Playbooks: Develop and maintain playbooks for common misconfigurations and security issues. This ensures a swift and standardized response to potential threats.
By applying these best practices, SMEs can significantly enhance the security of their Kubernetes environments, reducing the risk of breaches and ensuring that their applications run safely and reliably.
c. Real-Time Threat Detection
In a Kubernetes environment, real-time threat detection is essential for maintaining security and operational integrity. The ability to identify and respond to threats as they occur minimizes potential damage and ensures business continuity. This section explores the importance of real-time threat detection, outlines the key features of an effective threat detection system, and provides insights on integrating real-time threat detection into your Kubernetes setup.
Importance of Real-Time Threat Detection
Minimizing Damage:
- Immediate Response: The quicker you detect a threat, the faster you can respond, reducing potential damage. Real-time detection enables immediate actions such as isolating affected components, blocking malicious traffic, and initiating incident response protocols.
- Proactive Defense: Identifying suspicious activities early allows for proactive defense mechanisms, preventing minor issues from escalating into major security incidents.
Enhancing Incident Response:
- Rapid Investigation: Real-time alerts provide immediate data about suspicious activities, enabling rapid investigation and response. This reduces the time attackers have to exploit vulnerabilities or exfiltrate data.
- Improved Accuracy: With timely information, security teams can more accurately distinguish between false positives and genuine threats, ensuring resources are focused on real issues.
Protecting Sensitive Data:
- Preventing Data Breaches: Real-time detection helps in quickly identifying and stopping attempts to access or steal sensitive data, thereby protecting your organization's most valuable assets.
- Compliance Adherence: For many SMEs, adhering to regulatory requirements (such as ISO, PCI DSS, SOC 2, NIST, HIPAA, etc.) is crucial. Real-time threat detection helps ensure compliance by continuously monitoring for activities that could lead to regulatory violations.
Maintaining Business Continuity:
- Uninterrupted Operations: By swiftly addressing security threats, real-time detection helps maintain business operations without significant disruptions, ensuring continuous productivity and customer trust.
- Mitigating Financial Losses: Early detection and mitigation of threats can prevent financial losses associated with downtime, data breaches, and recovery efforts.
Key Features of an Effective Threat Detection System
Comprehensive Visibility:
- Cluster-wide Monitoring: An effective system should provide visibility across the entire Kubernetes cluster, including nodes, pods, containers, and network traffic.
- Detailed Logs: Access to detailed logs and events enables thorough analysis and investigation of potential threats.
Behavioral Analysis:
- Anomaly Detection: The system should employ behavioral analysis to detect deviations from normal activity patterns and identify potential threats based on unusual behavior.
- Machine Learning: Advanced threat detection systems leverage machine learning algorithms to continuously improve their detection capabilities by learning from historical data and emerging threats.
Automated Response:
- Real-Time Alerts: Immediate notification of suspicious activities allows for quick action. These alerts should be customizable to reduce noise and focus on critical threats.
- Automated Remediation: Integration with automation tools to perform predefined actions (such as isolating compromised pods or blocking IP addresses) can significantly reduce response times.
Integration Capabilities:
- SIEM Integration: Seamless integration with Security Information and Event Management (SIEM) systems allows for centralized analysis and management of security events.
- API Access: Open APIs enable integration with other security tools and workflows, enhancing the overall security posture.
User-Friendly Interface:
- Dashboards: Intuitive dashboards provide real-time insights and visualizations, making it easier for security teams to monitor and respond to threats.
- Reports: Regular reports on security status, incidents, and trends help in assessing the effectiveness of security measures and making informed decisions.
Integrating Real-Time Threat Detection in Kubernetes
Deploying Security Agents:
- Node-Level Agents: Install security agents on each Kubernetes node to monitor and collect data on container and pod activities. These agents provide visibility into runtime behavior and detect anomalies in real-time.
- Pod-Level Instrumentation: Use instrumentation within pods to gather detailed information on application behavior and interactions. This can include monitoring system calls, network connections, and file accesses.
Centralized Monitoring:
- Unified Dashboard: Implement a centralized monitoring system that aggregates data from all nodes and pods, providing a single pane of glass for security operations.
- Correlation and Analysis: Use centralized systems to correlate events from various sources, enabling comprehensive threat analysis and identification of complex attack patterns.
Automated Workflows:
- Alerting Mechanisms: Set up automated alerts to notify security teams of detected threats. Ensure these alerts are prioritized based on severity to facilitate quick action on the most critical issues.
- Incident Response Playbooks: Develop and integrate automated response playbooks that outline the steps to be taken when specific threats are detected. These playbooks can be executed automatically or with minimal human intervention.
Continuous Improvement:
- Regular Updates: Ensure that your threat detection tools and systems are regularly updated to incorporate the latest threat intelligence and security patches.
- Feedback Loop: Create a feedback loop where insights from detected threats and incidents are used to refine and improve detection algorithms and response strategies.
D. Threat Response Strategies
Effective threat response strategies are essential for mitigating the impact of security incidents in a Kubernetes environment. By implementing automated response mechanisms, strong incident response plans, and thorough post-incident analysis, SMEs can enhance their ability to handle threats efficiently and minimize potential damage.
Automated Response Mechanisms
Real-Time Mitigation:
- Immediate Containment: Automatically isolate compromised pods or nodes to prevent the spread of threats within the cluster. This can include stopping affected containers, disconnecting them from the network, or moving them to a quarantine environment.
- Blocking Malicious Traffic: Deploy network security policies that automatically block malicious IP addresses or suspicious traffic patterns detected in real-time.
Predefined Actions:
- Automation Scripts: Utilize automation scripts to perform predefined actions when specific threats are detected. For example, scripts can be triggered to restart pods, revoke access tokens, or modify firewall rules.
- Integrate with Orchestration Tools: Leverage orchestration tools like Ansible or Terraform to automatically execute complex response procedures, ensuring a swift and coordinated reaction to security incidents.
Alerting and Notification:
- Customized Alerts: Set up alerts to notify security teams of critical incidents. Ensure these alerts are detailed and actionable, providing relevant information for quick decision-making.
- Integration with Communication Tools: Integrate threat detection systems with communication platforms (e.g., Slack, Microsoft Teams) to ensure real-time notifications and facilitate rapid team collaboration.
Incident Response Plans
Developing a Response Framework:
- Defined Roles and Responsibilities: Clearly outline the roles and responsibilities of each team member involved in incident response. This ensures that everyone knows their duties and can act quickly and efficiently during an incident.
- Response Procedures: Develop detailed procedures for handling various types of incidents, including steps for identification, containment, eradication, and recovery. These procedures should be well-documented and easily accessible.
Regular Training and Drills:
- Training Programs: Conduct regular training sessions for your security and IT teams to ensure they are familiar with the incident response plans and can execute them effectively.
- Simulated Drills: Perform regular simulated incident response drills to test the effectiveness of your plans and identify areas for improvement. These drills help teams practice their response in a controlled environment, ensuring they are prepared for real-world incidents.
Communication Plans:
- Internal Communication: Establish clear internal communication protocols to ensure that all relevant stakeholders are informed during an incident. This includes executive management, IT teams, and affected departments.
- External Communication: Prepare communication templates and guidelines for notifying external parties such as customers, partners, and regulatory bodies in the event of a significant breach. Transparency and timely communication can help maintain trust and comply with legal requirements.
Post-Incident Analysis and Improvements
Root Cause Analysis:
- Detailed Investigation: Conduct a thorough investigation to determine the root cause of the incident. Identify how the threat entered the system, what vulnerabilities were exploited, and the extent of the damage.
- Documentation: Document all findings, including a timeline of events, actions taken, and lessons learned. This documentation is crucial for future reference and improving response strategies.
Continuous Improvement:
- Incident Review Meetings: Hold post-incident review meetings with all relevant stakeholders to discuss what worked well and what could be improved. Use these discussions to refine your incident response plans and procedures.
- Update Security Policies: Based on the findings from the root cause analysis, update your security policies and controls to prevent similar incidents in the future. This may include patching vulnerabilities, enhancing access controls, or adjusting network security configurations.
Feedback Loop:
- Learning from Incidents: Establish a feedback loop where insights gained from incidents are used to inform ongoing security improvements. This iterative process ensures that your security posture evolves with emerging threats and changing environments.
- Metrics and Reporting: Track metrics related to incident response, such as detection time, response time, and impact. Regularly report on these metrics to measure the effectiveness of your security program and demonstrate continuous improvement.
By deploying these threat response strategies, SMEs can significantly enhance their ability to handle security incidents effectively. Automated response mechanisms, comprehensive incident response plans, and rigorous post-incident analysis all contribute to a robust and resilient security posture, ensuring that your Kubernetes environment remains secure and operational.
Further reading
Cloud Storage
Misconfigurations

Build and maintain a strong
Security Program from the start.
Cloud Compliance in
2025: An In-Depth Guide
The whitepaper talks about ISO 27001, SOC 2, PCI-DSS, GDPR, HIPAA.
Download WhitepaperShare this article
CEO & Founder at Cyscale
Ovidiu brings his cybersecurity experience to the table, innovating with AI-powered solutions that address the real-world challenges of cloud security. His approach is focused on providing SaaS companies with the tools they need to navigate the complexities of compliance and grow securely within their regulated environments.
Stay Connected
Receive our latest blog posts and product updates.
TOP ARTICLES
Cloud Security
Our Compliance toolbox
Check out our compliance platform for cloud-native and cloud-first organizations:

LATEST ARTICLES
What we’re up to

Why the world needs Cyscale in a post-Wiz era




