NIST CSF 2.0: A Detailed Roadmap for Modern Cybersecurity
Cloud Security Analyst at Cyscale
Tuesday, April 16, 2024
It’s been six years since The NIST Cybersecurity Framework (CSF) 1.1 was released. While NIST has been an important benchmark for professionals, the newer version delivers an updated, more complete version that is meant to guide companies through a complex landscape.
With its recent iteration, CSF 2.0 not only highlights the importance of robust governance and supply chain management but also offers a flexible roadmap adaptable to organizations of all sizes and sectors.
Let’s look at the structure of NIST CSF 2.0 and observe the differences between this version and its previous iteration.
The structure of NIST CSF 2.0
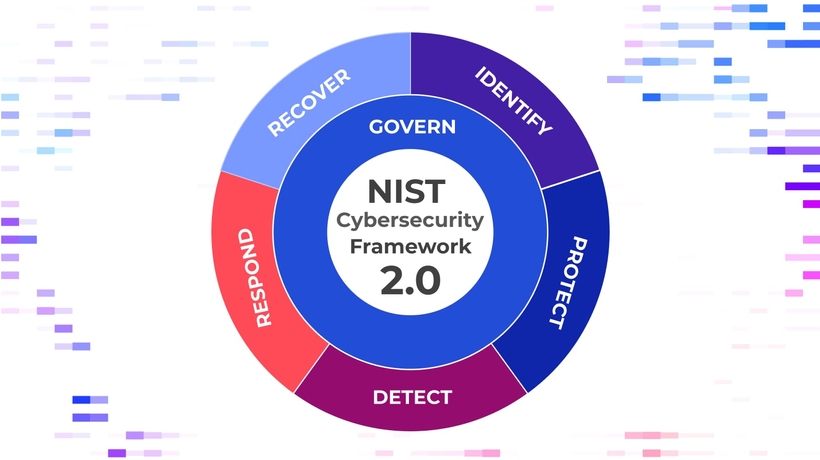
The new framework contains three main components:
- The CSF Core, which is made up of the well-known Functions which we will discuss in detail in this article, as well as Categories, and Subcategories. This is the most important and detailed part, because it describes cybersecurity outcomes that can be achieved by applying the Functions accordingly, as described in the Categories and Subcategories.
- CSF Organizational Profiles, which are meant to describe a company’s security posture in relation to the CSF Core. These profiles can be the Current State Profile, which provides insights into the current strengths, weaknesses, and possible improvements regarding the company’s security posture, as well as the Target State Profile, which contains the objectives and outcomes the organization strives for, similar to a roadmap.
- CSF Tiers, which describe a company’s rigor regarding cybersecurity and risk management. Possible tiers are partial, informed, repeatable, and adaptive.
The CSF Core Functions
Here, we can identify the first big change from the previous version. While NIST CSF 1.1 had five Functions in its Core, the 2.0 version introduces a new one, Govern. These are all of the functions:
- Govern
- Identify
- Protect
- Detect
- Respond
- Recover
These Functions describe the outcomes that will be achieved when following the guidance of the CSF. Therefore, they are not a list of actions that need to be made, but rather the outcome an organization will obtain when following best practices.
To fully understand this new version of the CSF, let’s look at each Function and describe it:
1. Govern (GV)
This new function introduces the importance of establishing robust cybersecurity risk management strategies, expectations, and policies within an organization. It serves as the foundation upon which all cybersecurity efforts are built and encompasses a range of critical activities.
The Categories in the Govern function are:
- Organizational context,
- Risk management strategy,
- Roles, responsibilities, authorities,
- Policy,
- Oversight, and
- Cybersecurity supply chain risk management.
2. Identify (ID)
The result of the second function is getting to understand the current cybersecurity risks associated with the organization fully. This means having visibility over all of the company's assets (in the context of the cloud, that would be all cloud resources such as VMs, data stores, apps, etc, but not only), suppliers, and risks, and prioritizing efforts accordingly.
Prioritization of assets can be very challenging for a cloud environment with thousands of resources and intricate relations between them. To be able to correctly prioritize assets, contextual security is the answer: knowing which VMs are Internet-facing, what IAM users and managed identities have privileged permissions, and who has access to high-value assets such as databases and buckets can make the difference nowadays; understanding which asset to secure first can make the difference between a successful and an unsuccessful hacker attack.
The Identify function also includes improvements for policies, procedures, plans that support the risk management plan and mission established under Govern. The Categories in Identify are the following:
- Asset management,
- Risk management, and
- Improvement.
3. Protect (PR)
The third function, Protect, identifies the need to secure assets by performing training and awareness programs, ensuring data and platform security, and managing the authentication and access control mechanisms. This function comes as a sequel to the previous functions, after risks and assets have been identified and prioritized.
The following Categories are in this function:
- Identity management, authentication, and access control,
- Awareness and training,
- Data security,
- Platform security, and
- Technology infrastructure resilience.
4. Detect (DE)
The Detect function refers to identifying possible attacks, IoCs (Indicators of Compromise), user suspicious behavior, and other anomalies. It also includes incident response and recovery outcomes. The Categories are:
- Continuous monitoring, and
- Adverse event analysis.
5. Respond (RS)
This function describes the outcomes of reacting to incidents that occurred in a company, which include incident management, analysis, mitigation, reporting, and communication. Nowadays, with emerging threats that are becoming increasingly more complex, it is essential to be able to react to attacks quickly and contain them. Suppose your company suffers a DDoS attack at peak usage times. In that case, processes should be in place to minimize consequences, which can affect the company's reputation and financial situation.
The categories in Respond are:
- Incident management,
- Incident analysis,
- Incident response reporting and communication, and
- Incident mitigation.
6. Recover (RC)
The last function of NIST CSF refers to restoring assets that have been affected by an incident and minimizing the consequences of a cybersecurity attack.
Categories in Recover include:
- Incident recovery plan execution, and
- Incident recovery communication.
NIST highlights that all Functions should be addressed continuously and consistently. The 6 Functions are divided into Categories and Subcategories to allow a granular approach in terms of technical and management decisions.
The new NIST CSF version serves as an updated, industry-recommended standard for navigating the complexity of the cloud security space. It provides clear guidance for organizations by emphasizing the need for risk management, recovery planning, and strong governance.
Cloud Security Analyst at Cyscale
Sabrina Lupsan merges her academic knowledge in Information Security with practical research to analyze and strengthen cloud security. At Cyscale, she leverages her Azure Security Engineer certification and her Master's in Information Security to keep the company's services at the leading edge of cybersecurity developments.
Further reading
Cloud Compliance in
2025: An In-Depth Guide

The whitepaper talks about ISO 27001, SOC 2, PCI-DSS, GDPR, HIPAA.
Download WhitepaperCloud Storage
Misconfigurations
Build and maintain a strong
Security Program from the start.
Share this article
Stay Connected
Receive our latest blog posts and product updates.
TOP ARTICLES
Compliance
Our Compliance toolbox
Check out our compliance platform for cloud-native and cloud-first organizations:

LATEST ARTICLES
What we’re up to

Why the world needs Cyscale in a post-Wiz era





