SOC 2 Compliance in The Cloud
Cloud Security Analyst at Cyscale
Wednesday, August 3, 2022

SOC 2 is an international compliance standard that defines rules for B2B (business-to-business) organizations regarding data security.
SOC (Service and Organization Controls) 2 was developed by AICPA (The American Institute of Certified Public Accountants).
It regulates data security management based on the following five cybersecurity principles, which are also defined as Trust Service Criteria (TSC):
- Security
- Availability
- Processing Integrity
- Confidentiality
- Privacy
SOC 2 requirements, explained for cloud
In order to become SOC 2 compliant, you must fulfill 64 trust service criteria across the 5 TSCs mentioned above.. Based on them, the organization establishes corresponding controls to demonstrate compliance.
In this section, we will look at some of the points of focus necessary to obtain the accreditation. They should be taken into account by companies that use cloud services.
Grouped by criteria and explained, here are examples of requirements:
1. Security
- Implements Boundary Protection Systems - The company uses firewalls, IDSs, DMZs to secure devices.
- Requires Additional Authentication or Credentials - Multi-Factor Authentication (MFA) is configured for all users.
2. Availability
- Designs Detection Measures - Logging and monitoring are implemented.
- Implements Alerts to Analyze Anomalies – Targeted alerts are used to ensure fast remediation for high-priority assets.
3. Processing Integrity
- Protects Stored Items – Sensitive data is safely stored in order to prevent it from being tampered.
- Creates and Maintains Records of System Storage Activities – Logging and monitoring are required for this criterion as well.
4. Confidentiality
- Restricts Logical Access– Access to sensitive cloud assets is limited, and the Least Privilege Principle is implemented.
- Identifies and Authenticates Users – The company follows good practices regarding IAM.
5. Privacy
- Uses Encryption to Protect Data – All assets of type storage are encrypted.
- Protects Identification and Authentication Credentials – Managing access to cloud assets is a matter of privacy since an entity that isn't authorized should not be able to access them.
How do you obtain the SOC 2 accreditation?
The process of obtaining it depends on the type of accreditation you’re going for. There are two types of SOC audits, which require different reports:
- Type 1: a single audit and a single report are required at a specific date and time. For this type, the design of the security program put in place is evaluated.
- Type 2: to obtain the SOC 2 Type 2 accreditation, an audit is carried out over a period of time, usually a minimum of six months. For type 2, the execution of the security program is evaluated.
There are advantages and disadvantages to both types.
While type 1 requires less effort and is easier to get, it is also less valuable, since the evaluation result only reflects the state of the company's data security at a given point in time.
With type 2, you invest more time and resources into getting accredited, but the result shows more effort and commitment toward the customer's data security.
Once you’ve decided which SOC 2 type you want to obtain, you need to start the long process of obtaining the accreditation.
Use Cyscale to make this process easier for you
Cyscale can help you obtain the SOC 2 accreditation for your company by:
- checking with the use of in-app controls whether you're implementing the requirements,
- providing you with remediation steps for any findings,
- helping you to demonstrate, during the audit, that you’re SOC 2 compliant and should receive the accreditation.
In the image below, you can see a part of the SOC 2 standard page in Cyscale, which gives you metrics to know how you're doing in your process of becoming compliant.
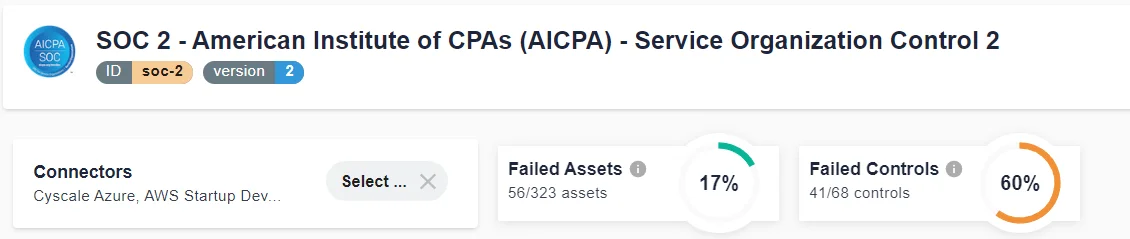
A large set of technical controls included in this standard are mapped to SOC 2 points of focus to easily understand which ones you’re correctly implementing, and which require your attention.
Cloud Security Analyst at Cyscale
Sabrina Lupsan merges her academic knowledge in Information Security with practical research to analyze and strengthen cloud security. At Cyscale, she leverages her Azure Security Engineer certification and her Master's in Information Security to keep the company's services at the leading edge of cybersecurity developments.
Further reading
Cloud Compliance in
2025: An In-Depth Guide

The whitepaper talks about ISO 27001, SOC 2, PCI-DSS, GDPR, HIPAA.
Download WhitepaperCloud Storage
Misconfigurations
Build and maintain a strong
Security Program from the start.
Share this article
Stay Connected
Receive our latest blog posts and product updates.
TOP ARTICLES
Compliance
Our Compliance toolbox
Check out our compliance platform for cloud-native and cloud-first organizations:

LATEST ARTICLES
What we’re up to

Why the world needs Cyscale in a post-Wiz era





