CSPM SOLUTION
Contextual Cloud Security Posture Management
Continuous visibility of multi-cloud environments to identify cloud misconfiguration vulnerabilities, ultimately securing your cloud from data breaches and leaks. Scan, monitor, and remediate across AWS, Microsoft Azure, Google Cloud, Alibaba Cloud.
01
ONBOARDING
Time to value: 5 minutes
Agentless deployment
No-hassle onboarding
Full map of cloud assets & security score
02
CONFIGURATION
Customize your setup in 60 mins
Expand cloud infrastructure securely
500+ ready to use security controls and policies
03
CONTINUOUS
MONITORING
Easily surface and manage cloud assets that fail security policies
In-app security consultancy & remediation steps
Onboard teams in 30 mins
04
REPORTING
See compliance with regulatory frameworks and policies at a glance
Up to 1-year data retention Data Exports (CSV, PDF)
LEVERAGE THE BEST SECURITY TOOLS FOR
CLOUD-NATIVE APPLICATIONS
Demonstrate your cybersecurity posture to auditors and
customers to enable the business and scale securely
A single misconfiguration can compromise your efforts with devastating impact. Use Cyscale and leverage
public cloud infrastructure with confidence and peace-of-mind.
Automate cloud misconfiguration
checks and eliminate manual efforts
Cyscale provides continuous and automated detection of cloud misconfigurations across multiple cloud providers. Based on contextual analysis that uses graph technology, the platform ensures there are no blind spots in the effectiveness of your cloud security policies. Cyscale assesses impact and highlights top risks, making it easy to leverage your cloud environment with confidence.
Reduce tedious compliance tasks and
streamline audits
Compliance with industry frameworks and regulations such as ISO27001, SOC2 and PCI-DSS has never been easier. Mappings of cloud security controls to standards and policies generate compliance scores, guiding you when preparing for audits. When security posture falls behind a customizable threshold, you get notifications so that you can react quickly.
Discover the most flexible cloud security posture management
solution in the cloud security industry
GET A DEMOKEY CSPM FEATURES
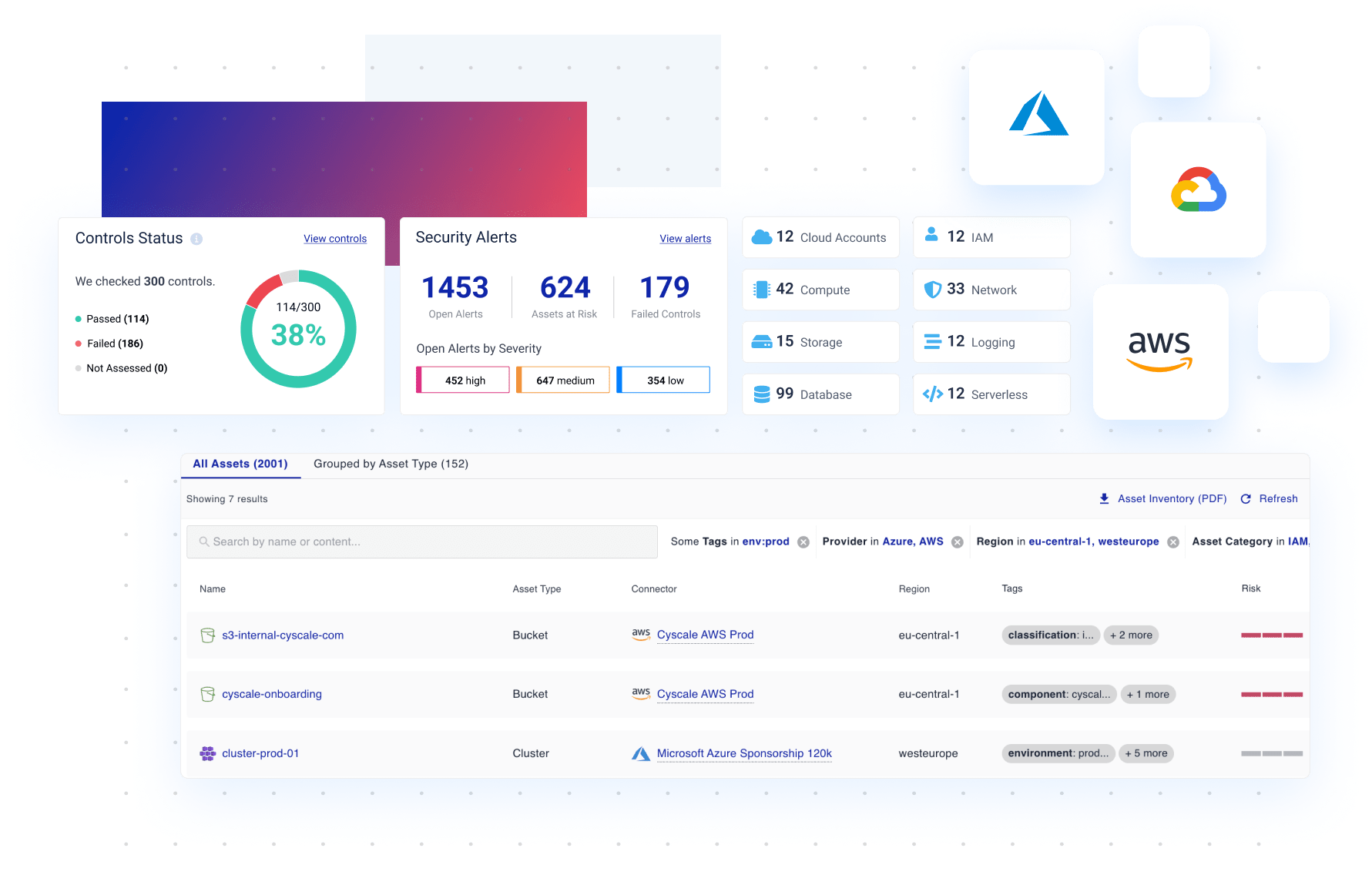
Achieve visibility over your cloud estate to prevent security incidents
Effective risk assessment with no blind spots
- Track cloud resources with a searchable, easy to use, exportable Cloud Asset Inventory. Cyscale integrates with AWS, Microsoft Azure, Google Cloud, Alibaba and identity providers such as Okta, Entra ID, Google Workspace.
- Easy cloud security posture management with powerful dashboards highlighting top cloud security risks across IaaS, PaaS, identity and data. Eliminate lack of visibility and make sure you're always working on what matters most.
- Dive deep into cloud configurations and enable teams to build common understanding with graph-based infrastructure diagrams that contain risk information. Easily visualize access to S3 buckets, misconfigured ports that provide unintended internet exposure, and so on.
- Enhanced visibility for the entire cloud is complemented with custom defined views based on scopes: cloud account, application, environment, end-customer, and many others.
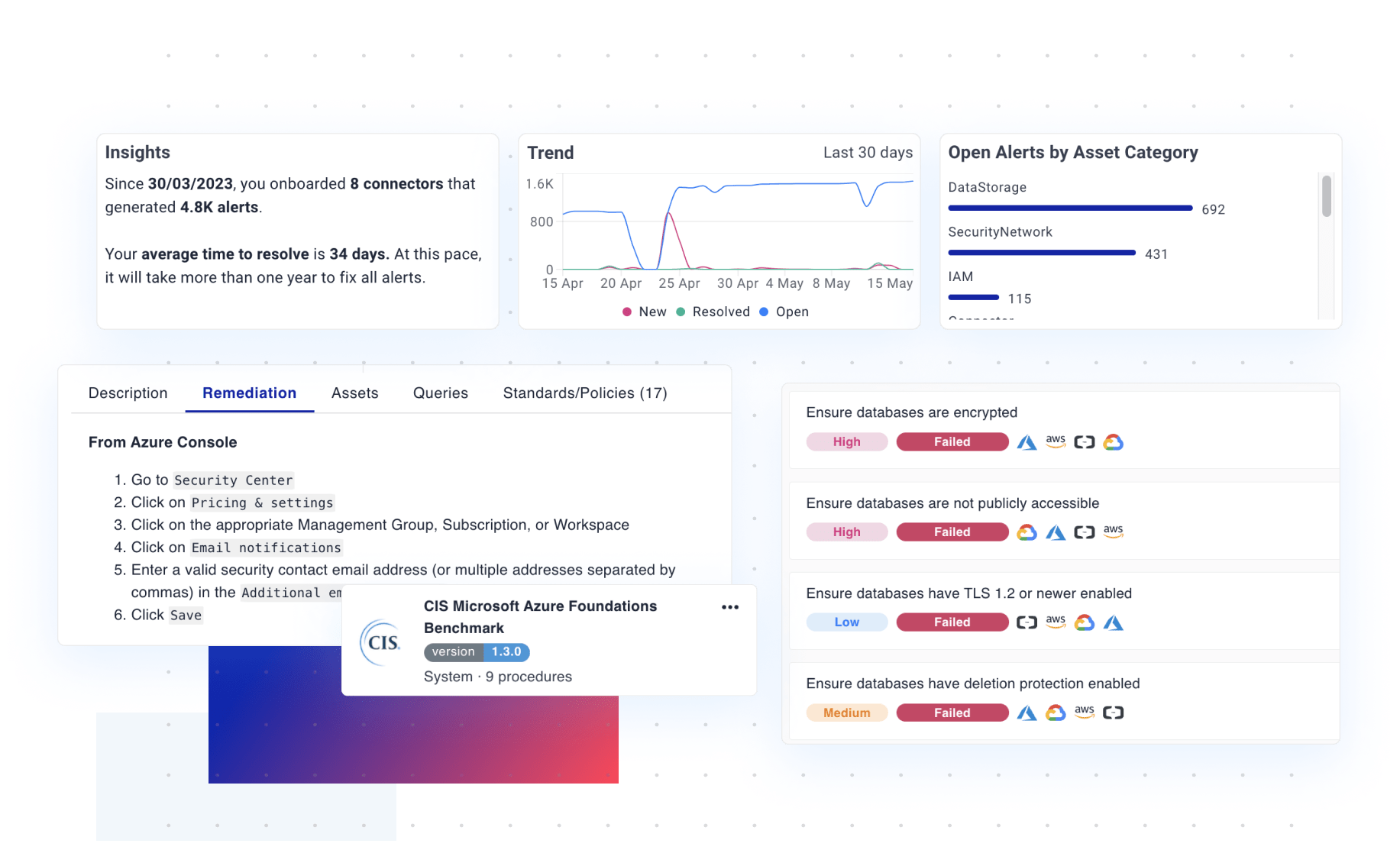
Harden your cloud and enable continuous protection
Drift detection reduces the risk of a data breach
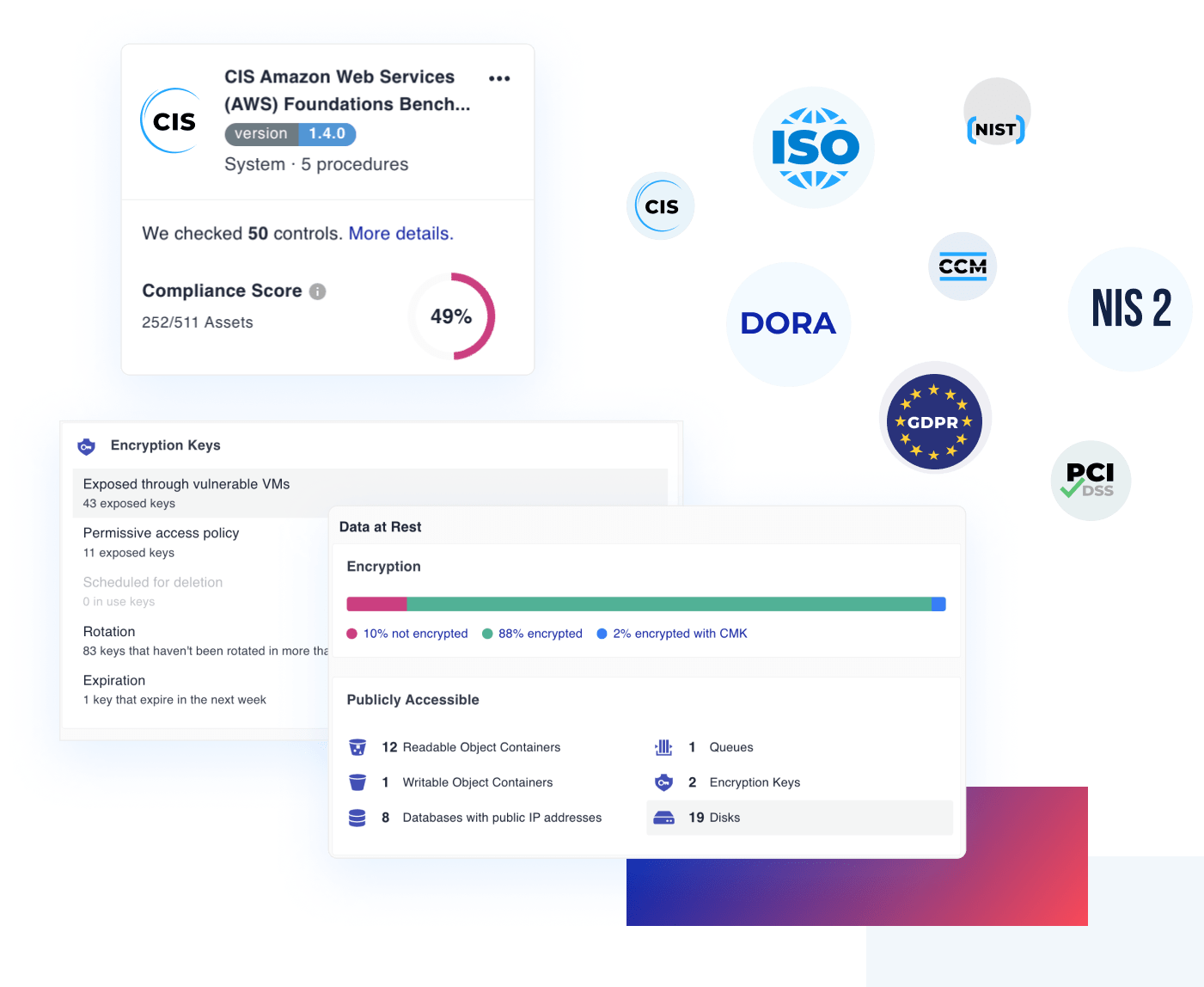
- Benefit from a large library of security controls drawing from industry benchmarks such as CIS, as well as our security expertise. Cyscale controls cover cloud services including identity, storage, networking, container services, and managed Kubernetes.
- Eliminate false positives with exemptions, complete with an exemption approval process and adequate reporting.
- Enable productivity for team members of all skill levels through detailed remediation steps.
- The Platform leverages the Security Knowledge Graph to perform contextual analysis of misconfigurations, by automatically correlating them with exploitable vulnerabilities, identities and paths to sensitive data.
- React quickly to new vulnerabilities with the help of continuous monitoring and configurable alerts. Use integrations to route alerts to relevant teams, on their preferred communication channel.
Automate compliance and gain back time for your team
Out-of-the-box actionable policies and standards
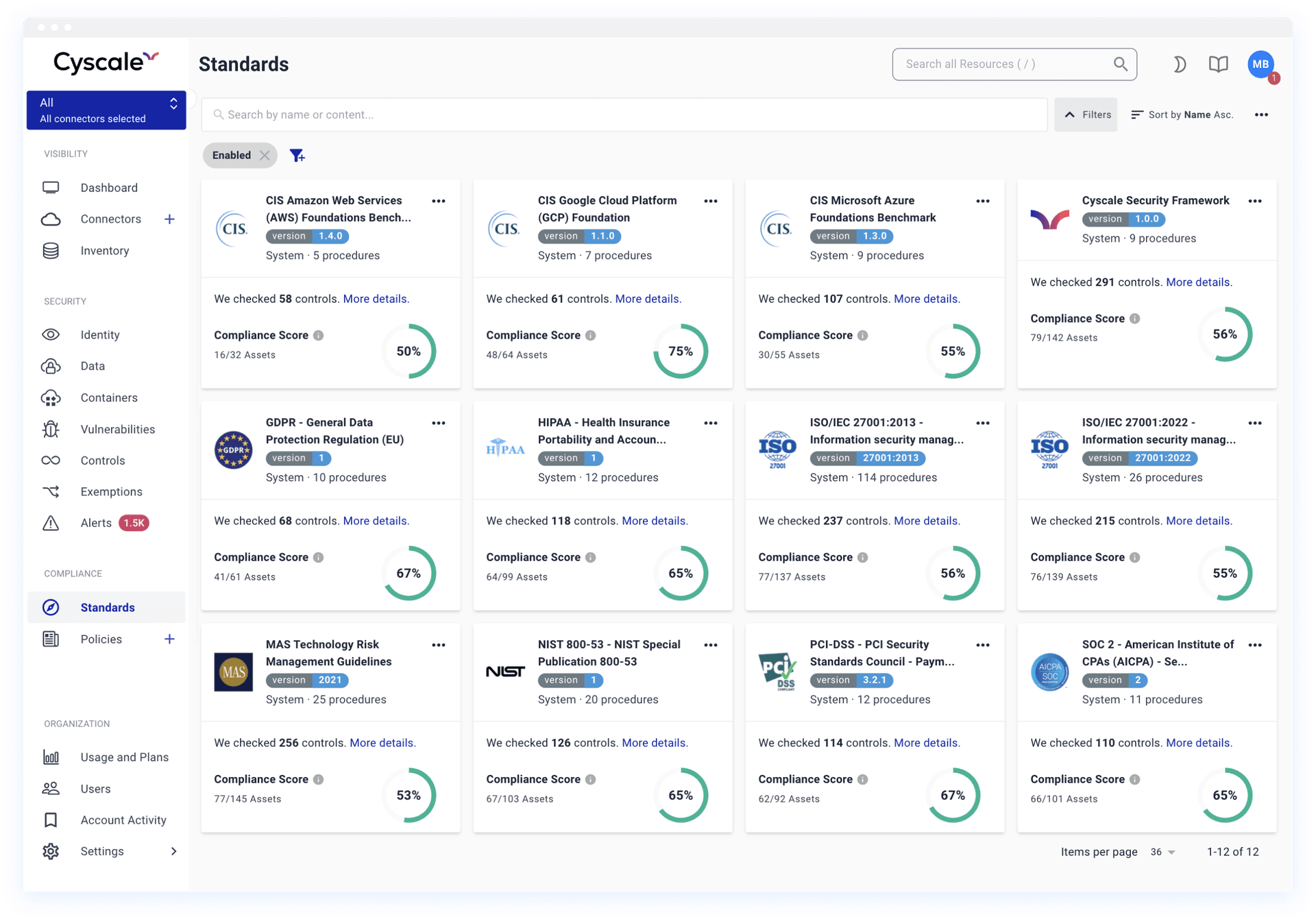
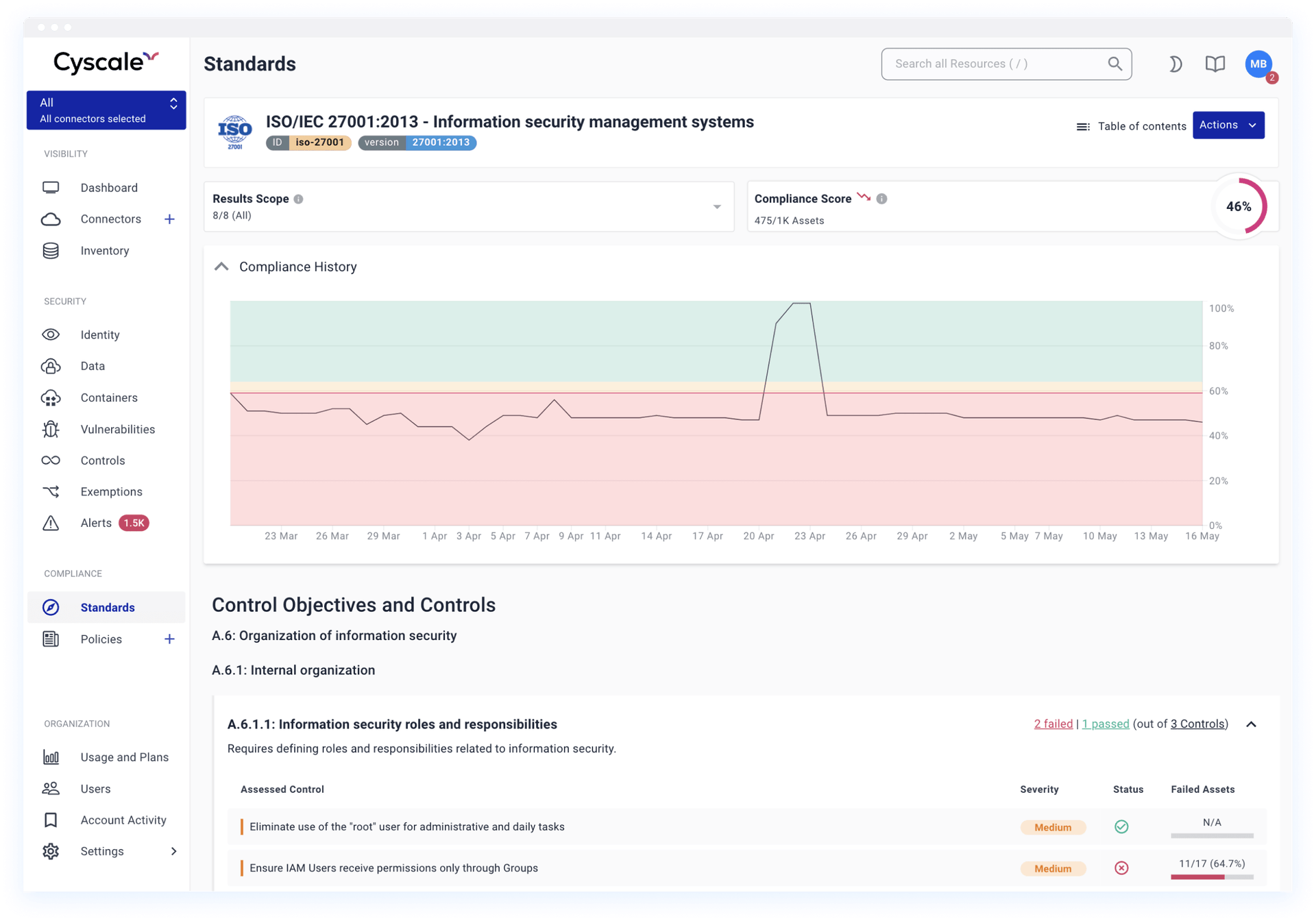
- Continuous compliance monitoring for industry standards and regulations such as ISO27001, SOC2, PCI-DSS, GDPR, HIPAA, NIST, and many others.
- In-app policy templates such as Data Protection, Identity and Access Management, Incident Response etc, and the ability to define your own.
- Requirement-based automated evidence collection.
- Get notified whenever policy violations occur and your compliance score falls beneath a customizable threshold. This helps you prevent security risks while maintaining compliance.
- Enhanced visualization with comprehensive pdf reports for auditors, customers, or other stakeholders. A powerful scoping mechanism allows for granular reporting.
- Look at your cloud estate through the data lens with the help of a Data Security Dashboard that highlights data exposure and toxic combinations of risks that jeopardize your crown jewels.
- Easily perform regular access and permissions reviews with the help of an Identity Dashboard that highlights least privilege violations and other security issues in IAM.
CASE STUDY
Data security in a
multi-cloud environment
This US-based data intelligence platform was experiencing strong growth, resulting in significantly more customer data being stored in the cloud. As the company approached the 400-employee mark and began to feel more pressure on its cybersecurity team, the time came to sunset in-house tools developed on open-source offerings and deploy a solution that would make it easier to maintain a strong security posture over a sprawling multi-cloud estate.
Read the case studyCASE STUDY
“It’s been great at identifying blind spots”: Bays Consulting achieves 50% productivity gain with Cyscale
“Exceptionally helpful when doing access reviews; I’m using the platform monthly and it simply automates my work!”

James Hawkes
Head of Delivery at
Bays Consulting
CASE STUDY
Smart Fintech uses Cyscale to gain IAM visibility and ensure cloud security and compliance
“The platform helps me with IAM visibility a lot: I can understand who has access and why. When a person leaves the company, I can detect if their permissions remain hanging.”

Alex Cociu
Risk and Compliance Officer at
Smart Fintech
Explore other Cyscale security solutions
Frequently asked questions
What is a Cloud Security Posture Management (CSPM) tool?
CSPM is a group of security tools and technologies that empower security users to identify and remediate risk and misconfigurations in their cloud environments.
Read more in our guide.What are some key capabilities of a CSPM solution?
- Continuous compliance monitoring of your cloud resources, so you can identify and remediate risk in areas such as storage, encryption, and permissions
- Technical security controls and visibility over IAM (Identity and Access Management) configuration, to help provide risk assessment and ensure that compliance standards are met
- Easily identify risks that could compromise your cloud network across cloud providers, such as Google Cloud, AWS and Microsoft Azure
- Remediation guidance, to quickly solve misconfigurations leading to compliance violations for Saas (Software as a Service), Iaas (Infrastructure as a Service) and Paas (Platform as a Service)
What are some benefits of utilizing a CSPM tool?
Visibility into your company's cloud infrastructure and security configurations.
Security teams can assess posture across multiple cloud environments and accounts through a centralized dashboard that can give actionable metrics.
Evidence.
Violations in your cloud infrastructure are mapped to regulatory standards, security frameworks, as well as internal security policies, resulting in evidence collection that enables audits.
Reporting and alerting.Insights on your cloud's risk posture, as well as alerts and notifications bring risk to your attention, enabling investigation and in-time remediation.
Automation.One of the most important features of a CSPM tool. Automated remediation, helps security teams reduce the time and effort required by manual remediation, at the same time enabling evidence collection.
Read more in our guide.RECOMMENDED ARTICLES
CSPM
The Complete Guide
to Cloud Storage Misconfigurations
This guide helps CIOs, CISOs and security staff to understand the risk & dangers of data security breaches and the importance of a secure cloud storage infrastructure.