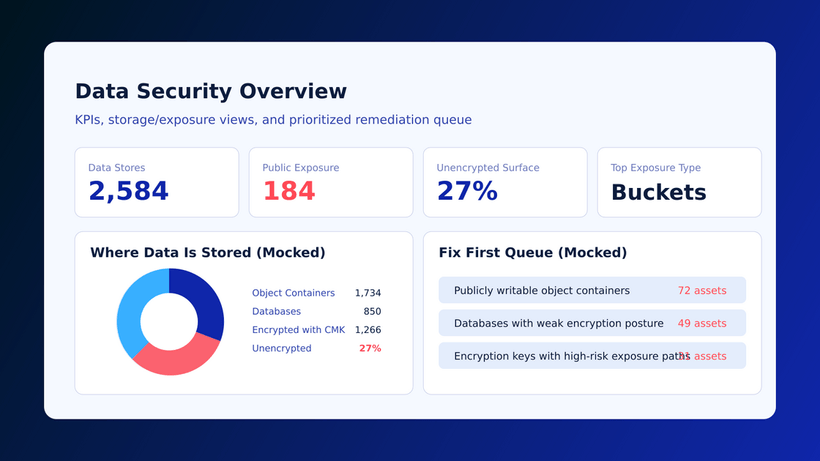
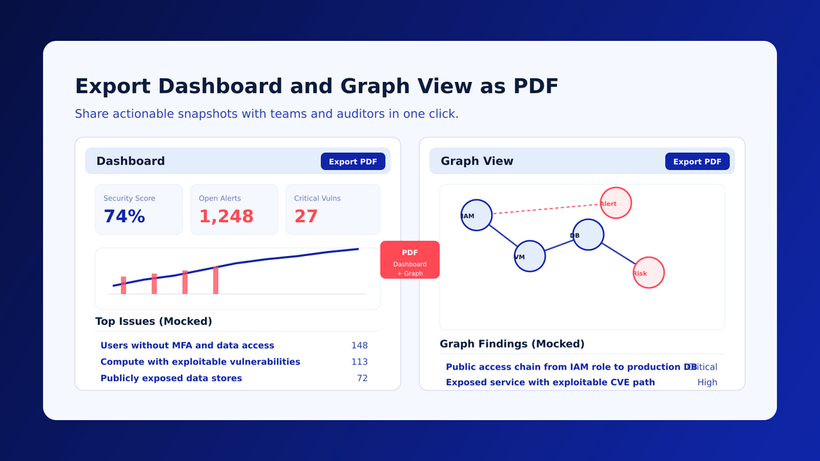
CONTENTS
Top 10 Cloud Security Challenges in 2024
Cloud Security Analyst at Cyscale
Friday, January 5, 2024

Any article covering the top cybersecurity challenges is typically dominated by the human element – humans being the weakest link, prone to errors, misconfigurations, and poor security hygiene. But this year it’s different.
The rapid and unpredictable rise of AI has drawn attention through all of 2023, leading to questions about the positive and negative impact it will have on lives and businesses going forward.
There’s no doubt AI-driven attacks will be a pivotal challenge that defines the cloud security landscape for 2024, but it’s not the only consideration characterized by intricate and cutting-edge vulnerabilities and attacks.
Let's take a close look at the top 10 cloud security challenges we've identified in the last year that need to be closely monitored in 2024 and beyond.
1. Advanced AI-driven threats
Throughout 2023, AI exploded as a megatrend that changes the risk landscape significantly – both positively and negatively. We’ve seen AI-powered DDoS attacks, where attackers use automation to adjust threat vectors based on real-time analysis of success against various attack surfaces, and ransomware and malware that can adapt to the environment and replicate using existing and newly discovered vulnerabilities.
The potential for generative AI and Large Language Models (LLMs) is a double-edged sword, and the cloud security landscape feels uncertain as attackers come up with more and more sophisticated attacks.
In 2023, hackers managed to abuse the growing popularity of OpenAI's well-known tool, ChatGPT. The chatbot was found to be "hallucinating" in its responses to questions about coding packages and libraries and recommending things that didn't exist.
Hackers went ahead and created malicious packages with the same names, so developers receiving the same recommendations from ChatGPT would download the malicious software.
Although the threat is of great concern, it’s not all doom and gloom, according to Google Cloud’s own CISO. While it’s true we expect to see AI help attackers, AI should also give defenders a significant advantage because AI is good at amplifying capability based on data — and defenders have more data.
Protecting against AI-driven threats
In this rapidly changing field, continuous education regarding emerging AI-threats is vital. Awareness campaigns and training are the best weapons against these kinds of attacks.
Cloud security solutions such as Cyscale are also leading the application of AI to make cybersecurity more human friendly. As security practitioners are overwhelmed by information, making sense of that information in terms of context and inference is becoming more of a challenge.
Cyscale’s AI-powered Security Assistant is a move towards making cloud security as intuitive as asking a question.
Our platform can automatically respond to queries and surface uncovered issues using the specific customers’ cloud footprint combined with LLMs of vulnerabilities and exploits.

2. Phishing and Social Engineering
Human behavior remains one of the staples in any list of risks, both as an external threat as well as an internal one due to disgruntled employees.
As an external threat, phishing is still one of the most effective attacks. Humans are always the weak link in the security chain, and AI is making defending from social engineering attacks even harder due to the ease with which deep fakes can be produced that appear to be someone you know, to automated, convincing emails, messages, and chats with no grammar errors or that take on the tone and style of a specific person.
In the cloud, IAM (Identity and Access Management) is the first line of defense when focusing on the prevention of unauthorized users and devices from accessing cloud assets.
Leaked credentials and bypassed authentication processes are very dangerous and can lead to massive disasters, such as data breaches and unauthorized access to sensitive resources.
Protecting against phishing and social engineering attacks
Training programs for social engineering attacks are necessary to prevent employees from falling for phishing scams.
Enforcing MFA (Multi-Factor Authentication) is essential. Whether you’re using a passwordless solution or passwords, MFA should be enabled for everyone and especially for high-privilege users.
3. Evolving regulatory frameworks
As technology advances, we see more and more updates and additions to compliance laws and standards ensuring both businesses and customer data are adequately protected.
Maintaining compliance with the increasing complexity of frameworks and benchmarks can become overwhelming very quickly, especially for small teams.
For example, in 2023, we saw multiple updates to CIS benchmarks for cloud services including Azure, AWS, and Kubernetes.
For financial institutions, the implementation deadline for DORA (Digital Operational Resilience Act) is also quickly approaching, with the release scheduled for early 2025 (17th of January).
All told, 2024 is a pivotal year for compliance and companies must keep up with the evolving regulations and maintain a good cloud security posture to protect themselves from emerging cybersecurity threats.
Maintaining compliance with cloud security regulations and standards
Because of the ever-changing landscape, staying on top of cloud security compliance is a continuous process that involves regular assessments of your cloud estate and compliance posture.
You can keep up to date on new and changing requirements by reading our blog posts. Furthermore, cloud security solutions like Cyscale can also help you keep track of your compliance progress and know where you’re standing.
4. Quantum computing for password cracking
Widely used encryption algorithms such as RSA were originally designed to withstand traditional computing attack methods, requiring a significant amount of computations to be made in order to crack passwords.
The entire cryptographic landscape is currently based on this solution, with RSA protecting sensitive data everywhere. But developments in quantum computing keep advancing and threaten to make the impossible number of computations achievable.
As a result, it’s expected that traditional encryption methods might one day become obsolete. The day quantum computing attacks will become possible is named Q-day, and it might be around the corner.
Protecting against quantum computing attacks
In parallel with developments in quantum computing, quantum-resistant cryptographic algorithms or post-quantum cryptography are our only solutions at this time, and the first group of encryption tools that are designed to withstand the assault of a future quantum computer are in development.
5. Complexity in multi-cloud environments
It’s often said that the real killer in cloud security is the complexity. Cloud platforms and products have evolved in a granular fashion and security has followed suit. One often quoted Gartner prediction is that 99% of cloud security failures through 2025 will be due to user error as admins struggle to keep control of sprawling estates.
Cloud service providers offer menus of products and services running into the hundreds, each with their own security configuration, and in a multi-cloud environment this complexity is amplified.
Managing data security in multi-cloud environments can be especially challenging due to cloud providers' different configurations, security policies, even their vocabulary. As new tools appear, fully understanding a multi-cloud infrastructure can become harder. Remember, a certified AWS cloud expert is not an Azure cloud expert by default, and vice versa.
Reducing complexity in multi-cloud environments
Bringing all your cloud assets, information, and configurations into one single platform is the key to not getting lost in your own cloud, and this means adopting a security strategy that includes a CSPM or a CNAPP solution.
Gartner research found that CSPM implementations can reduce cloud security incidents caused by misconfigurations by up to 80%. The single-pane-of-glass view across your multi-cloud estate also cuts down on the need to switch between multiple dashboards and means you can understand your entire cloud inventory in context.
6. Cybersecurity alert fatigue
Stress and burnout are rampant among cybersecurity professionals and the impact of user fatigue is no secret - thousands of alerts and logs that signal everything and anything that happens in the cloud is not a helpful approach. In many cloud security setups, the default process is to alert for every event, regardless of its criticality.
This flood of alerts can quickly become overwhelming for cloud security professionals who become used to severe or critical alerts popping up every day. When everything is critical, nothing is. So, this can desensitize them, and when an actual breach occurs and legitimately critical alerts are sent out, they can end up being overlooked.
This approach can also turn into a resource hog, giving security practitioners an endless list of tasks to work through that might not achieve the desired results.
Protecting against alert fatigue
To prevent user fatigue, contextual security is the best approach and your ability to prioritize remediation work efficiently depends on the capabilities of your CNAPP or CSPM.
By filtering out alerts that are not actually high risk in your unique cloud environment and shifting focus to your own most sensitive cloud resources, you can help your security people work more effectively.
7. Executive decisions and responsibilities
One of the biggest challenges a CISO or CTO faces when approaching the board or C suite for funding is justifying their cybersecurity spend. There has long been a perception gap between the cost of security versus the cost of a breach and the simple truth is, you can spend some money up front to reduce the likelihood of a breach, or you can spend more later when the breach has happened.
The global average cost of a data breach has climbed 15% over the last three years and with lagging investment, only about one third of breaches are picked up by an organization’s own team.
Furthermore, we’ve seen how decisions made by individuals in executive positions make or break a company through their impact on the company's security strategy. Look at the SolarWinds case as an example, where the SolarWinds CISO ended up being investigated for fraud over failure to fully disclose security gaps and issues in the company.
There’s also the issue of how those responsible for executing on the security strategy are impacted by executive decisions. The SEC investigation into SolarWinds found that “the volume of security issues being identified have outstripped the capacity of Engineering teams to resolve.”
Empowering security leaders to be effective
As increasing board liability for risk is sinking in, CTOs, CISOs, and security leaders should be looking to justify their security spend by aligning it with business goals, and instead of operating in a vacuum to build a culture of cybersecurity.
This also means formulating policies and establishing processes (and actually following them!) is an approach that all companies need to be doing to ensure employees follow good practices and don't move away from established rules.
8. Insider threats and privilege misuse
Sometimes, it's easy to focus on preventing unwanted access from external actors and forgetting that harm can also be done from the inside. Malicious or unintentional actions by employees with privileged access can pose significant security risks.
Estimates vary but most research agrees that more than half of security breaches experienced are a result of internal threats or abuse of privilege.
Protecting against insider threats
To prevent against damage caused by current or previous employees, ensure that:
- When offboarding users, you're removing all access and not leaving any dangling permissions that can be abused,
- You're following the Least Privilege Principle and only assigning the necessary permissions for the amount of time required,
- You're monitoring user activity and performing regular assessments of user access and permissions.
9. Cryptographic keys management
Managing encryption keys effectively is critical for safeguarding data. With the growing volume of encrypted data in the cloud, ensuring secure storage, access, rotation, and revocation of encryption keys has become challenging.
Why is the way you store and manage cryptographic keys so important? A good example is the leak of 38TB of secrets that occurred in 2023, when a GitHub repository owned by Microsoft’s AI research division provided a link to a misconfigured Azure storage resource.
Microsoft AI Researchers exposed crypto keys, passwords, and other data through a storage account that could be accessed using leaked SAS (Shared Access Signature) tokens. If encryption keys are leaked, the effort of encrypting data goes to waste.
And it’s not just about protecting data but maintaining access to it. If an encryption key expires before it’s rotated out, you could end up losing access to precious data.
Effective cryptographic keys management
As part of an effective CSPM approach, you need a solid crypto key management strategy. Cloud security platforms like Cyscale check a wide palette of settings using security controls across multiple cloud service providers to ensure keys on different platforms remain secure.
A few examples are:
- Ensure encryption keys are not expiring within the next 14 days
- Ensure encryption keys don't have permissive access policies
- Ensure in-use encryption keys are not scheduled for deletion
- Ensure Cloud KMS cryptokeys are not anonymously or publicly accessible
10. Incident Response
Preventative cybersecurity measures will only take you so far. Developing and implementing robust incident response plans specific to cloud environments is essential.
According to the annual M-Trends report by Mandiant, part of Google, global median dwell time was down to 16 days in 2023 from 21 the year before, meaning attacks are being detected more quickly than ever before.
Although this decrease is in part down to better tools and better approaches by defenders, an explosion in ransomware is also driving this number down as the point of these attacks is to make themselves known for extortion purposes.
So, when it comes to responding to an active incident, speed is of the essence.
Effective incident response in cloud security
Given the volume of tasks and pressure on human resources, automation can take a lot of the toil out of triage, prioritization, and remediation when it comes to detecting and acting on incidents.
Effective coordination, timely response to security incidents, and comprehensive recovery strategies are vital for minimizing damage and restoring operations.
Finally, while resumption of normal operations is the priority, care should also be taken to preserve evidence during the recovery and remediation phases. In some cases this may even be a regulatory requirement.
Challenges and opportunities in 2024: Adapting amid technological shifts
The challenges of 2024 bring forward a landscape where technological advancements intertwine with vulnerabilities, creating a need for adaptable and comprehensive security strategies.
As we navigate AI-driven threats, the looming potential of quantum computing, and growing multi-cloud environments, hackers find ever-more innovative ways to attack companies, and so we must focus on fortifying our defenses, meaning proactive measures become imperative.
To prepare for this changing landscape, book a free cloud security health assessment with Cyscale. Get complete visibility of your entire cloud estate in minutes and assess your cloud security posture, so you can expose, understand, and prioritize any threats.

Cloud Security Strategy Roadmap
While the challenges of cloud security can seem overwhelming, having a comprehensive and strategic roadmap in place can guide your journey towards a secure cloud environment. Whether you're a CISO, a Cloud Security Expert, or a Senior System Administrator, this roadmap is tailored to meet the unique requirements of your organization's cloud security posture.
1. Assessment and Understanding of the Current State:
- Security Posture Analysis: Understand the current security posture by evaluating the existing security controls, policies, and configurations.
- Risk Assessment: Identify potential risks, vulnerabilities, and threats specific to your cloud environment, including unauthorized access, data loss, and insider threats.
- Compliance Alignment: Ensure that your cloud infrastructure aligns with industry regulations and standards like PCI-DSS, GDPR, and HIPAA.
2. Creating a Security Framework and Policies:
- Define Security Objectives: Establish clear and measurable security goals that align with organizational priorities.
- Implement Security Frameworks: Utilize recognized frameworks such as NIST or ISO/IEC 27001 for a structured approach.
- Develop and Enforce Policies: Create comprehensive security policies, including identity and access management (IAM), endpoint security, and multi-factor authentication (MFA).
3. Implementing Security Controls and Tools:
- Leverage Security Solutions: Implement tools like Cyscale's CSPM tool for managing cloud security, and consider CNAPP security for application protection.
- Utilize Firewalls and Real-time Protections: Employ firewalls and real-time security solutions to protect against cyberattacks, phishing, and malware.
- Secure Cloud Data and Infrastructure: Use cloud security compliance platforms to ensure data protection and integrity across hybrid and multi-cloud environments.
4. Monitoring, Reporting, and Incident Response:
- Continuous Monitoring: Implement continuous monitoring of security threats, unauthorized access, and configurations through platforms like CSPM.
- Regular Reporting: Generate regular reports on security performance, compliance alignment, and potential vulnerabilities.
- Incident Response Plan: Develop a robust incident response strategy to address breaches and attacks, ensuring timely mitigation and recovery.
5. Ongoing Evaluation and Improvement:
- Review and Update Security Measures: Regularly review and update security measures to stay ahead of evolving threats and security landscape changes.
- Provide Continuous Training: Educate security teams and employees on emerging threats, security best practices, and ongoing compliance requirements.
- Evaluate Emerging Technologies: Keep up with new technologies and approaches in cloud security, like cloud security strategy best practices, to continually innovate and strengthen your security posture.
Building a comprehensive cloud security strategy is not a one-time effort. It's a dynamic and ongoing process that requires careful planning, execution, and adaptation. By following this roadmap, you can navigate the complex terrain of cloud security challenges and forge a path toward a resilient and secure cloud environment.
Putting the cloud security plan into action
In the ever-evolving landscape of cloud security, opportunities and challenges converge. From managing vulnerabilities, thwarting hackers, and grappling with misconfigurations, to mastering compliance and mitigating data loss, the hurdles are many but not insurmountable.
Understanding the top 10 challenges a comprehensive cloud security strategy needs to overcome can set you up for success when you face these complexities head-on. Remember, the key to your defense lies in continuous adaptation, education, and employing the right tools.
Don’t get overwhelmed with the scope of the task. Cyscale’s Automated Cloud Security platform can be a valuable partner in safeguarding your cloud infrastructure environment and ensuring compliance.
Further reading
Cloud Storage
Misconfigurations

Build and maintain a strong
Security Program from the start.
Cloud Compliance in
2026: An In-Depth Guide
The whitepaper talks about ISO 27001, SOC 2, PCI-DSS, GDPR, HIPAA.
Download WhitepaperShare this article
Cloud Security Analyst at Cyscale
Sabrina Lupsan merges her academic knowledge in Information Security with practical research to analyze and strengthen cloud security. At Cyscale, she leverages her Azure Security Engineer certification and her Master's in Information Security to keep the company's services at the leading edge of cybersecurity developments.
Stay Connected
Receive our latest blog posts and product updates.
TOP ARTICLES
Cloud Security
Our Compliance toolbox
Check out our compliance platform for cloud-native and cloud-first organizations:

LATEST ARTICLES
What we’re up to

Cyscale on AWS Marketplace Simplifies CNAPP Procurement and Deployment