What to Look for in a CSPM?
Cloud Security Analyst at Cyscale
Monday, May 23, 2022

A Cloud Security Posture Management (CSPM) tool is a product that scans your cloud environment for vulnerabilities. It alerts you if it finds any misconfigurations in the cloud infrastructure.
This article will discuss what you need to look for in a CSPM and help you make the right choice regarding your cloud's security posture.
Does it check for a wide variety of vulnerabilities?
There is a long list of possible misconfigurations, policy violations, and mistakes that can disrupt your cloud system.
A good CSPM tool will have controls to check for a wide variety of vulnerabilities and correctly identify any misconfigurations.
Some of the most common cloud misconfigurations are:
- Poor storage access configuration,
- Broken access control,
- Unrestricted inbound and outbound traffic,
- Missing encryption,
- Disabled or unconfigured logging and monitoring.
Does it have an integration with your preferred cloud platform?
The CSPM tool you choose must be compatible with the cloud platform your system is using. The top three vendors in the cloud industry are:
With Cyscale, you can scan and maintain your cloud security posture for all three of the vendors mentioned above, as well as Alibaba Cloud.
Another essential feature is that Cyscale integrates Okta identities.
What compliance frameworks does it support?
A certificate of compliance with a standard such as ISO 27001 or SOC 2 can be an asset because it advertises the following things about your company:
- You understand the significance of cybersecurity,
- Your organization is working to reduce the risk of information security breaches,
- You are adequately managing information security.
In order to make the best use of your CSPM, take into account what compliance standard or certification your company is going for. A few examples are:
- ISO 27001
- SOC 2
- NIST 800-53
- PCI-DSS
- CIS
- GDPR
Some standards require you to write your own policies such as Data Protection or Disaster Recovery.
You can manage them using traditional tools such as Microsoft Word and Sharepoint, or you can use a powerful policy editor and gain inline evidence collection offered by Cyscale.
Is the CSPM providing vulnerability and risk scoring?
Prioritization of issues and risk scoring is an essential feature of a CSPM.
Assigning risk levels to assets and prioritizing remediation can significantly increase a company's security.
Vulnerability scoring is another essential feature that can help you avoid false positives and prioritize tasks. Time is crucial when discussing vulnerabilities, so quick actions need to be taken to prevent breaches.
This is why it is essential to ensure that false positives are avoided because they can cause noise that may distract employees from more important matters.
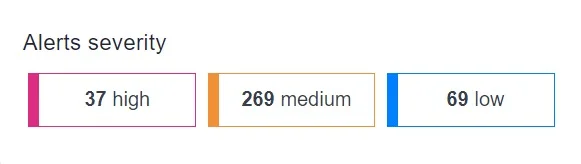
Do you receive targeted alerts?
Receiving thousands of alerts can be overwhelming. Your CSPM tool needs to filter them and send relevant, targeted alerts.
Cyscale currently has two types of notifications that can be customized to your preference:
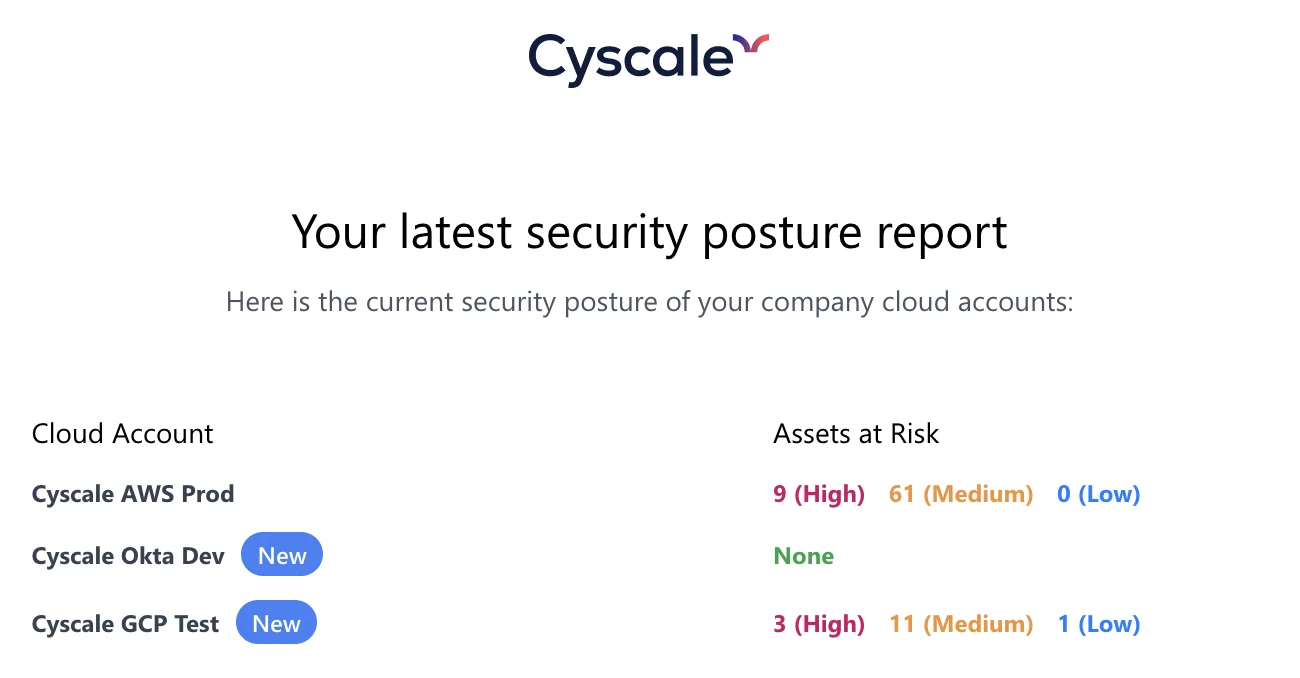
- Security Posture. These weekly digests show you your cloud security posture trend and a high/medium/low-risk asset count. You can see an example below.
- Alerts. They are sent in batches for a given cloud account in a single email to ensure that they do not become overwhelming. These alerts inform you of new vulnerabilities found in your cloud infrastructure.
Besides these personal notifications sent to your email, you can also enable alerts on Slack, Teams, or an app of your choice, by using Webhook.
Does it provide remediation for found vulnerabilities?
Finding misconfigurations and vulnerabilities in your cloud infrastructure is just the first step.
Applying the correct remediation before it becomes a breach is critical to securing your cloud.
Cyscale provides, along with the controls that pinpoint what vulnerability has been identified, the following:
- an explanation of the cause of the control failure,
- how the vulnerability was identified,
- remediation steps.
The remediation steps can ensure you're applying the modifications correctly and speed up the process of securing your assets.
Make the right decision for your company by using a robust CSPM that helps secure your cloud infrastructure and provides all of the features mentioned above and more.
Cyscale ensures the following features:
- checks for a wide variety of vulnerabilities,
- integration with AWS, Google Cloud, Azure, Alibaba, Okta,
- support for compliance frameworks and standards,
- prioritization of assets remediation and alerts,
- targeted and custom alerts,
- remediation steps and vulnerabilities reports.
Cloud Security Analyst at Cyscale
Sabrina Lupsan merges her academic knowledge in Information Security with practical research to analyze and strengthen cloud security. At Cyscale, she leverages her Azure Security Engineer certification and her Master's in Information Security to keep the company's services at the leading edge of cybersecurity developments.
Further reading
Cloud Storage
Misconfigurations

Build and maintain a strong
Security Program from the start.
Cloud Compliance in
2025: An In-Depth Guide
The whitepaper talks about ISO 27001, SOC 2, PCI-DSS, GDPR, HIPAA.
Download WhitepaperShare this article
Stay Connected
Receive our latest blog posts and product updates.
TOP ARTICLES
CSPM
Our Compliance toolbox
Check out our compliance platform for cloud-native and cloud-first organizations:

LATEST ARTICLES
What we’re up to

Why the world needs Cyscale in a post-Wiz era





