CIEM and IAM: The 2 Critical Components of Cloud Security
CEO & Founder at Cyscale
Monday, May 27, 2024
As cloud adoption speeds up, many organizations face the tricky task of managing access and identities. Unauthorized access and mismanaged identities (shadow IDs) are leading causes of data breaches, making strong cloud security essential.
Cloud Infrastructure Entitlement Management (CIEM) and Identity and Access Management (IAM) are vital to overcoming these challenges. CIEM ensures precise control over permissions in dynamic cloud environments, while IAM secures entry points by managing human (employees or contractors) and non-human identities (machine to machine or service accounts).
In this post, we will explore the unique strengths of CIEM and IAM and why only their combined capabilities can strengthen your cloud security posture.
1. CIEM: The Precision Expert
Cloud Infrastructure Entitlement Management (CIEM) is an advanced approach to managing and securing access permissions within complex cloud environments. As organizations increasingly rely on multiple cloud platforms, the complexities of controlling who has access to what become exponentially challenging. CIEM addresses this by providing a centralized mechanism to ensure that access rights are both appropriate and compliant, reducing the risk of unauthorized access and potential data breaches.
Key Powers of CIEM:
-
Pinpoint Access Control: CIEM introduces the concept of "just enough" access (enforce least privilege principle), ensuring that users have only the permissions they need to perform their tasks—nothing more, nothing less. This granular level of control is crucial in preventing data breaches caused by over-privileged access. By continuously monitoring and adjusting permissions, CIEM helps organizations maintain a tight security posture, minimizing the attack surface.
In the context of AWS environments, enforcing AWS Least Privilege is critical to achieving the level of granular access control that CIEM offers. AWS Least Privilege ensures that users, services, and applications only have the necessary permissions to perform their tasks, reducing the risk of over-privileged access that could lead to security vulnerabilities. By implementing AWS Least Privilege as part of your CIEM strategy, you can effectively minimize your attack surface and safeguard your cloud assets.
-
Unified Multi-cloud Defense: Managing security across multiple cloud platforms can be daunting, with each platform having its own set of rules and configurations. CIEM offers a unified view and control over these different environments, enabling consistent security policies and streamlined management. This holistic approach simplifies the complexity of multi-cloud security, ensuring that all environments adhere to the same rigorous standards.
-
Automated Guardrails: The dynamic nature of cloud environments demands real-time adjustments to access controls. CIEM can provide automated guardrails that adapt to changes in the cloud infrastructure, such as new user accounts, services, or policy updates. These automated systems ensure that access permissions are always up-to-date, reducing the risk of human error and enhancing overall security.
2: IAM: The Identity Guardian
Identity and Access Management (IAM) is the foundation of an organization’s security framework, focusing on managing digital identities and controlling access to critical resources. IAM ensures that the right individuals have the appropriate access to technology resources, enabling organizations to secure their systems while enhancing operational efficiency.
Core Strengths of IAM:
- Fortified Entry Points: IAM strengthens security by implementing robust authentication and authorization mechanisms. Multi-factor authentication (MFA), single sign-on (SSO), and role-based access control (RBAC) ensure that only authenticated and authorized users can access sensitive information. By fortifying entry points, IAM significantly reduces the risk of unauthorized access and potential breaches.
- Strategic Policy Playbook: Effective IAM systems leverage detailed access policies to manage and secure user access. These policies dictate who can access what resources under what conditions, aligning access privileges with the organization’s security requirements. A well-defined policy framework helps in minimizing insider threats and ensures that users only have access to the resources necessary for their roles.
- Compliance Assurance: Compliance with regulatory standards is a critical aspect of IAM. Continuous monitoring and logging of user activities help organizations maintain compliance with regulations such as GDPR, HIPAA, and others. IAM solutions provide comprehensive audit trails and reports, facilitating easier management of compliance requirements and ensuring that organizations can quickly address any irregularities or breaches.
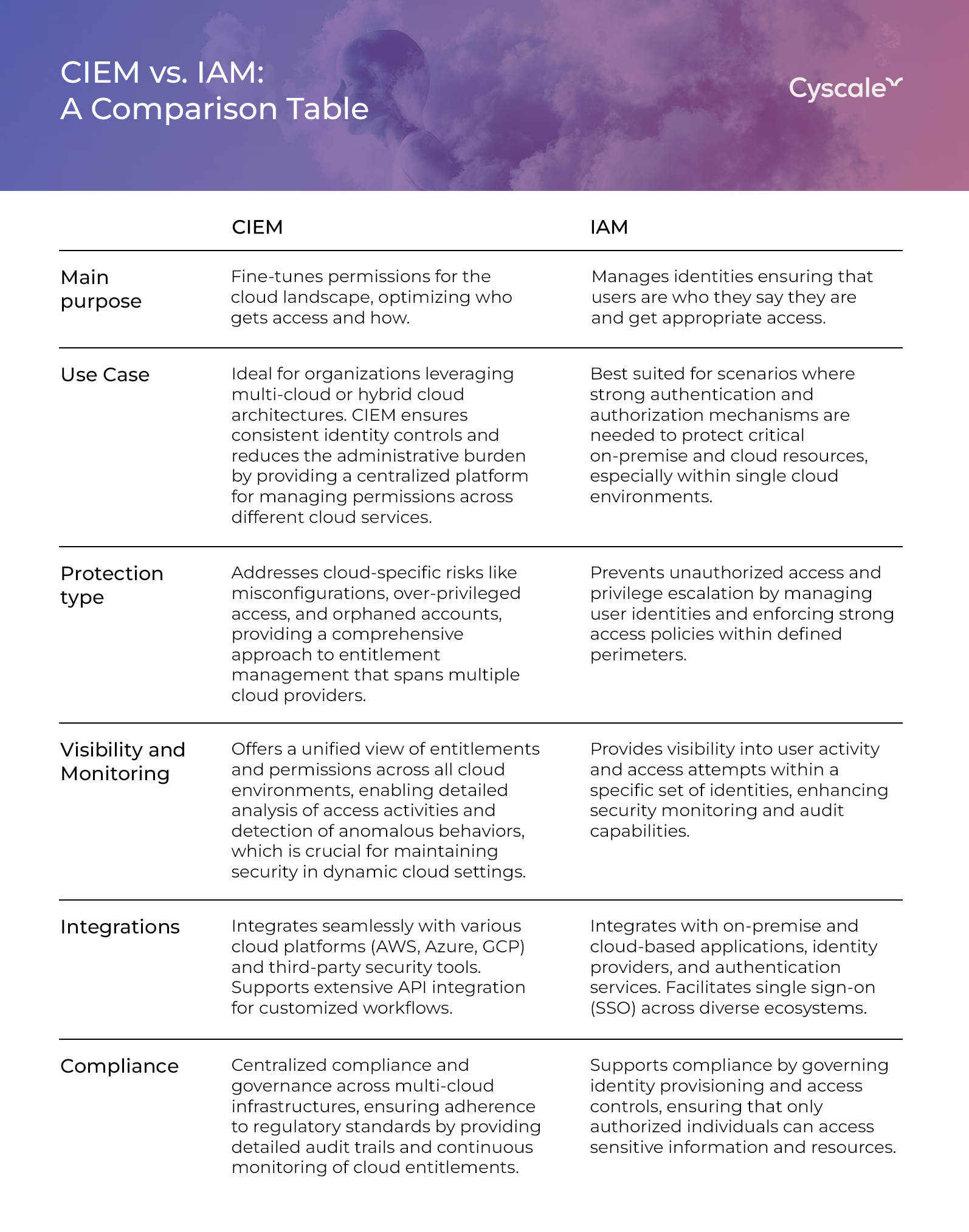
3. Combined Strengths of CIEM and IAM
- Comprehensive View of Permissions and Access: When integrated, CIEM security and IAM provide a holistic view of an organization’s access landscape. CIEM’s granular control over permissions complements IAM’s robust identity management, ensuring that every access point is monitored and managed with precision. This comprehensive oversight helps in identifying and rectifying over-privileged access, thereby minimizing security risks.
- Minimized Risks and Enhanced Security: The synergy between CIEM and IAM enhances an organization’s ability to enforce the principle of least privilege. CIEM’s capability to dynamically adjust permissions in real-time, combined with IAM’s strong authentication and access policies, ensures that users have just the right amount of access needed to perform their duties. This minimizes the risk of data breaches and unauthorized access.
- Ensured Compliance and Auditability: CIEM and IAM together streamline compliance management by providing detailed logs and audit trails. Organizations can easily track and report access activities, ensuring adherence to regulatory requirements. This integrated approach simplifies compliance audits and helps in quickly addressing any compliance issues that arise.
- Enhanced Security Posture Management: Using a unified CNAPP platform, organizations can visualize how CIEM and IAM work together to boost security. This provides real-time insights into access permissions, identity management, and potential security threats. This visibility allows security teams to make informed decisions and respond promptly to emerging risks.
CEO & Founder at Cyscale
Ovidiu brings his cybersecurity experience to the table, innovating with AI-powered solutions that address the real-world challenges of cloud security. His approach is focused on providing SaaS companies with the tools they need to navigate the complexities of compliance and grow securely within their regulated environments.
Further reading
Cloud Storage
Misconfigurations

Build and maintain a strong
Security Program from the start.
Cloud Compliance in
2025: An In-Depth Guide
The whitepaper talks about ISO 27001, SOC 2, PCI-DSS, GDPR, HIPAA.
Download WhitepaperShare this article
Stay Connected
Receive our latest blog posts and product updates.
TOP ARTICLES
IAM
Our Compliance toolbox
Check out our compliance platform for cloud-native and cloud-first organizations:

LATEST ARTICLES
What we’re up to

Why the world needs Cyscale in a post-Wiz era




