Container Escaping with Leaky Vessels: A New Docker Vulnerability with 8.6 Severity
Cloud Security Analyst at Cyscale
Tuesday, February 27, 2024

New vulnerabilities revealed in the runc command line tool could be exploited to allow attackers to escape containers and potentially get unauthorized access to the host operating system and move laterally though a Kubernetes or cloud environment.
What are the Leaky Vessels vulnerabilities?
On the 31st of January 2024, Snyk revealed four Docker container vulnerabilities with a critical security score ranging between 8.6 and 10. These vulnerabilities allow attackers to escalate privileges and escape containers, gaining access to the underlying instance and possibly compromising secrets and other resources.
An attacker exploiting an orchestration-based setup utilizing runc, such as Kubernetes, could execute a breakout onto the underlying Kubernetes node. In multi-tenant environments, pods from different tenants can share nodes, meaning a breakout could lead to unauthorized access to other pods belonging to other tenants.
The vulnerabilities affect runc, a container runtime, and Buildkit, a builder for docker:
CVE-2024-21626, which affects runc, has a severity of 8.6. It occurs in runc versions 1.1.11 and earlier, so updating the CLI tool to version 1.1.12 would patch this vulnerability.
How does the Leaky Vessels exploit work?
By leveraging the “WORKDIR” command, the attacker can spawn a new process and have a working directory in the host��’s filesystem. This can be done either by running a malicious image or by building a container image using a malicious Dockerfile. These two attacks can also be used to overwrite host binaries, thus escaping the container.
Container escape elevates the attackers’ privileges and opens up other possibilities; by having access to the underlying system of a container, a hacker can access files and secrets on the host and even move laterally to compromise other systems.
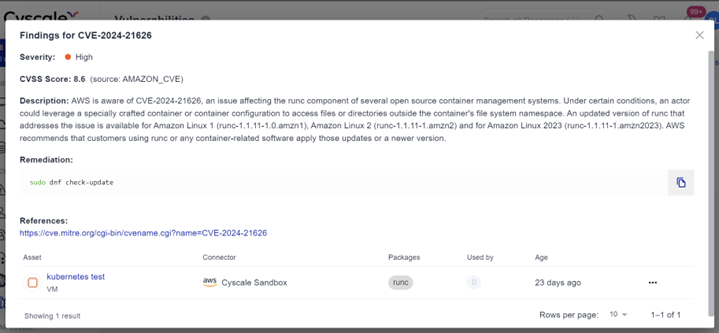
How do you fix it?
To determine if this vulnerability exists in your cloud or Kubernetes environment, you can start a free risk assessment with Cyscale. The Cyscale cloud security platform immediately detects vulnerabilities that can affect your cloud security posture and provides actionable remediation steps to help you fix findings quickly.
Cloud Security Analyst at Cyscale
Sabrina Lupsan merges her academic knowledge in Information Security with practical research to analyze and strengthen cloud security. At Cyscale, she leverages her Azure Security Engineer certification and her Master's in Information Security to keep the company's services at the leading edge of cybersecurity developments.
Further reading
Cloud Storage
Misconfigurations

Build and maintain a strong
Security Program from the start.
Cloud Compliance in
2025: An In-Depth Guide
The whitepaper talks about ISO 27001, SOC 2, PCI-DSS, GDPR, HIPAA.
Download WhitepaperShare this article
Stay Connected
Receive our latest blog posts and product updates.
TOP ARTICLES
News
Our Compliance toolbox
Check out our compliance platform for cloud-native and cloud-first organizations:

LATEST ARTICLES
What we’re up to

Why the world needs Cyscale in a post-Wiz era





