Cloud Identity - Expert Insights, Best Practices & Tips
Cloud SecurityIAMThursday, November 14, 2024
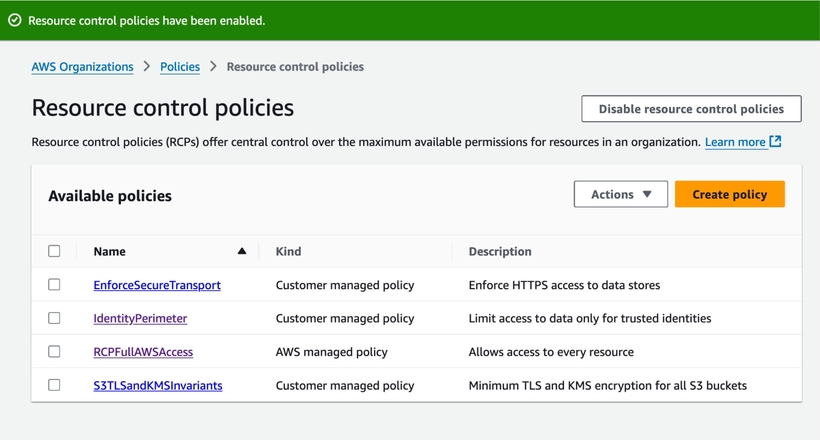
AWS Resource Control Policies (RCPs): Everything You Need To Get Started

Cloud SecurityIAMThursday, November 14, 2024
AWS Resource Control Policies (RCPs): Everything You Need To Get Started
Cloud SecurityIAMProductThursday, August 8, 2024
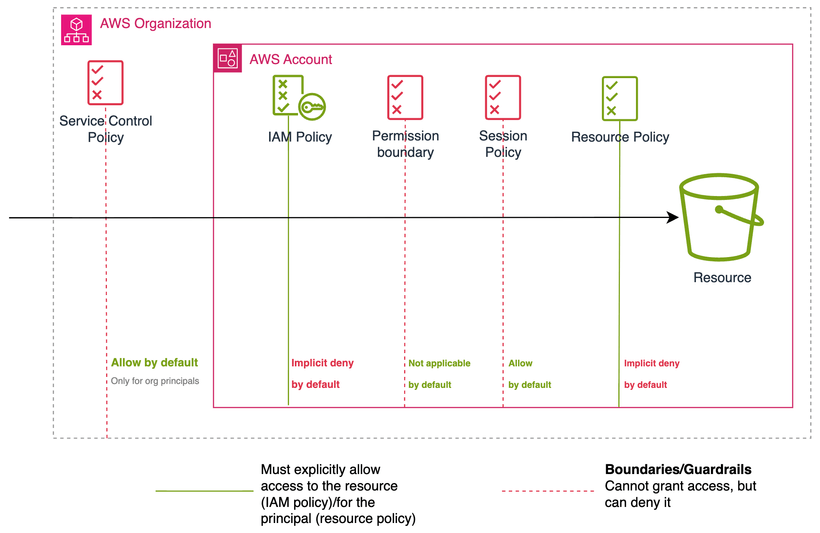
AWS IAM: A Comprehensive Guide Toward Least Privilege

IAMMonday, April 1, 2024
What are Non-Human Identities (NHIs), and how do we secure them?
IAMWednesday, February 21, 2024
Human and Non-Human Identity Management for Multi-Cloud






