CONTENTS
Why the world needs Cyscale in a post-Wiz era
CEO & Founder at Cyscale
Thursday, March 20, 2025

When I heard about Google’s $32 billion acquisition of Wiz, my first thought wasn’t about the staggering valuation or the market consolidation implications. Instead, my mind flew to a conversation I had with a CISO at a financial services company just a few weeks earlier. “Ovidiu, we’ve invested heavily in cloud security, but I still wake at night wondering if we’ve missed something critical - Wiz is helping us with that.” We all know that Wiz has the best multi-cloud security platform for Fortune 100 companies, much like Cyscale has the best solution for SMBs and Mid-Market companies, but at a fraction of the price.
The acquisition of Wiz by Google is a clear testament to the escalating value of cloud security solutions. This move not only reinforces the significance of robust cloud security but also sets new benchmarks for innovation and scalability in our field. Industry giants are doubling down on cloud security, highlighting that the traditional silos of security tools are giving way to holistic, integrated solutions.
The elephant in the room: Google’s Wiz acquisition
Google’s acquisition of Wiz represents the largest security acquisition in history and signals a fundamental transformation in how companies approach cloud security. Having spent the last decade in cloud security trenches, from leading security teams to architecting multi-cloud environments, and now building multi-cloud security software that is the best for SMBs and Mid-Market, I’ve witnessed firsthand how this space evolves in sometimes unpredictable ways.
In 2019, I was advising Rolls-Royce migrating to cloud infrastructure and I got a seemingly simple question: “Will this make us more secure or less?” The honest answer then, as now, was “it depends.” Cloud security isn’t binary; it’s a complex graph of configurations, identities, vulnerabilities, and data flows that require constant monitoring and vigilance. You either have an army of security people, or you need to buy the best cloud security tool outhere.
This complexity explains why Google paid such a premium for Wiz. And for their customers. With AWS and Azure generating $107 billion and $105 billion respectively in cloud revenue during FY2024, compared to Google’s $43 billion, Google needed to strengthen its security posture to compete effectively. But this acquisition creates significant questions for organizations invested in Wiz: Will Google maintain Wiz’s platform-agnostic approach, or will it gradually optimize for GCP environments at the expense of AWS and Azure coverage? Will AWS and Azure share their roadmaps with Wiz now, as they used to do?
Common acquisition aftermaths
I still remember sitting across from a distraught security director in 2018 after a major security vendor had been acquired (Skyhigh Networks). “A lot of our security architecture relied on their capabilities”, he explained, “but post-acquisition, feature development for competing platforms slowed to a crawl”.
This isn’t speculation about Wiz’s future but rather a pattern I’ve observed repeatedly in the security industry. Acquisitions invariably shift priorities, and when the acquirer has a competing cloud platform, objectivity becomes challenging to maintain. Palo Alto Networks, a great cybersecurity company nonetheless, turned into a Hydra with multiple heads because of the acquisitive philosophy they have.
The evolution of cloud security: from fragmentation to consolidation (Platformization)
To understand where we are today, we need to recognize where we’ve been. From 2016 to 2019, when I first began working with enterprise cloud deployments, the landscape was entirely fragmented:
- CSPM was in its infancy, with RedLock (now PANW) and Dome9 (now CheckPoint) emerging as main players, but these tools handled misconfigurations but knew nothing about workloads
- CWPP solutions monitored workloads but were blind to identity issues
- IAM tools managed permissions but couldn’t correlate with where data was
- DSPM wasn’t even a recognized category yet
Each solution created its own silo of alerts, leading to what one of my clients memorably called “security tool fatigue syndrome”, a situation where their team was drowning in 1,000+ daily alerts across seven platforms, with no way to prioritize effectively.
The market’s natural response was consolidation into Cloud-Native Application Protection Platforms (CNAPP). According to Gartner’s latest analysis, 75% of organizations that previously used standalone CSPM solutions will shift to integrated CNAPP platforms by 2025. This convergence makes strategic sense, because security teams need holistic visibility rather than fragmented snapshots.
Current players: technical reality vs. marketing hype
Developing, but also implementing and evaluating major cloud security platforms over the past 5-7 years, I can offer an unbiased perspective on the current landscape:
Wiz: technical brilliance, but with uncertain future now
Wiz’s meteoric rise to a $32 billion valuation wasn’t accidental. Their architecture brilliantly solved the scalability challenges that plagued earlier cloud security tools. By implementing a unique scanning approach that combined agentless inventory with targeted deep inspection, they could process massive environments without the performance penalties of traditional solutions.
In a 50,000-resource AWS environment I worked with last year, Wiz completed its initial scan in under 10 hours, approximately 5x faster than competitor solutions. But their technical advantage came with tradeoffs: limited historical data retention and gaps in runtime protection that required supplementary tools. Not to mention the price tag, out of this world.
Now, with Google’s acquisition, customers face legitimate questions about Wiz’s future direction. Will its engineering resources focus primarily on GCP integration? Will pricing models evolve to incentivize Google Cloud adoption? These concerns are already driving many security leaders to reevaluate their long-term strategies.
Orca Security: the Agentless sidescanning pioneer with coverage gaps
I first encountered Orca Security in 2022 when a retail client asked for alternatives that could provide rapid visibility into their sprawling cloud environment. Orca’s agentless approach delivered impressive initial results, helping the client identify within hours critical vulnerabilities that had escaped detection for months. However, as they moved from discovery to continuous protection, limitations emerged. During an incident response engagement last year, they observed firsthand how Orca’s agentless architecture struggled with ephemeral workloads. The client’s containerized environment was spawning and destroying instances faster than Orca could scan them, leaving dangerous blind spots. Without runtime telemetry, their security team had incomplete context for prioritization.
Lacework: the cautionary tale of AI overreliance
Lacework’s rise and subsequent challenges offer particularly relevant lessons. Lacework impressed with their machine learning approach to anomaly detection. Their Polygraph technology promised to revolutionize threat detection by automatically learning normal behavioral patterns.
The reality proved more complicated. Lacework’s anomaly detection generates thousands of alerts, false positives included (as most cybersecurity tools do anyway). Security teams eventually disable key alerting features in Lacework, undermining the platform’s core value proposition.
By late 2022, customers were reporting growing frustration with alert fatigue, and the company’s once-stratospheric valuation came under pressure. Their story illustrates the danger of overreliance on AI without sufficient context and human oversight. This turned to be a good lesson and helped us do this better at Cyscale, and avoid alert fatigue for our customers.
Smaller contenders on the rise
Companies like Upwind, Uptycs, and even Aikido are aggressively entering the market, each with unique propositions. Unlike Cyscale, each of them focus on a certain aspect of cloud security, rather than the holistic approach we have.
Let's not forget the Hyperscalers (AWS, Azure, GCP, Alibaba, etc.)
AWS, Azure, and GCP all prioritize cloud security through a combination of built-in protections, compliance certifications, and advanced threat detection.
- AWS offers services like GuardDuty, Inspector, and IAM to detect and mitigate risks, along with its shared responsibility model.
- Azure integrates security across its ecosystem with tools like Microsoft Defender for Cloud and Sentinel, leveraging AI for proactive threat management.
- Google Cloud emphasizes a zero-trust approach with BeyondCorp, Chronicle for threat intelligence, and its Security Command Center for centralized visibility.
Each provider continuously invests billions in encryption, identity management, and compliance frameworks to strengthen cloud security.
Why Cyscale is different: built from customer reality
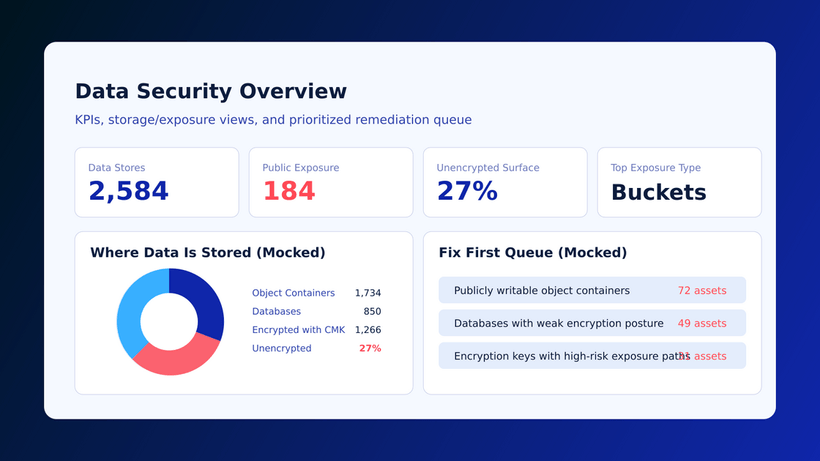
When we founded Cyscale, we didn’t start with PowerPoint slides and funding pitches. Instead, we spent six months conducting in-depth interviews with security practitioners across industries. The consistent theme? Existing tools were generating mountains of alerts without the context needed to prioritize effectively.
This insight became our founding principle: context is everything in cloud security. An unpatched vulnerability in an internet-facing container with access to sensitive data represents an urgent threat; that same vulnerability in an internal development environment might be a low priority. Without this context, security teams waste precious resources on low-impact issues while missing critical risks.
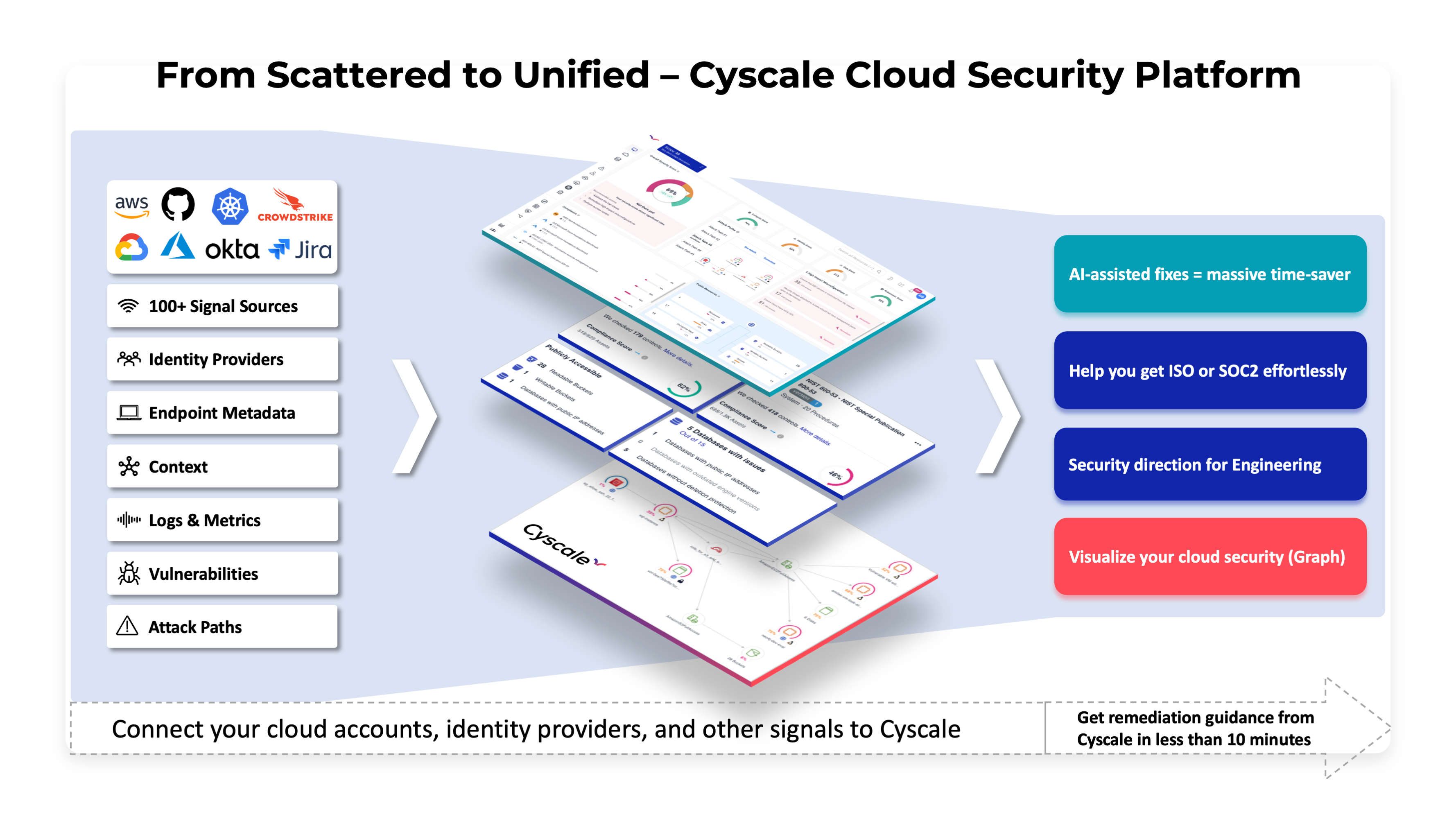
The Security Knowledge Graph: our technical breakthrough
Our key innovation back then, the Security Knowledge Graph, was launched before Wiz and Orca. Unlike conventional approaches that treat cloud resources as isolated entities, our graph technology maps relationships between all elements in your cloud environment:
- Which IAM roles can access which data stores?
- What network paths exist to sensitive workloads?
- Which vulnerabilities exist in actual attack paths?
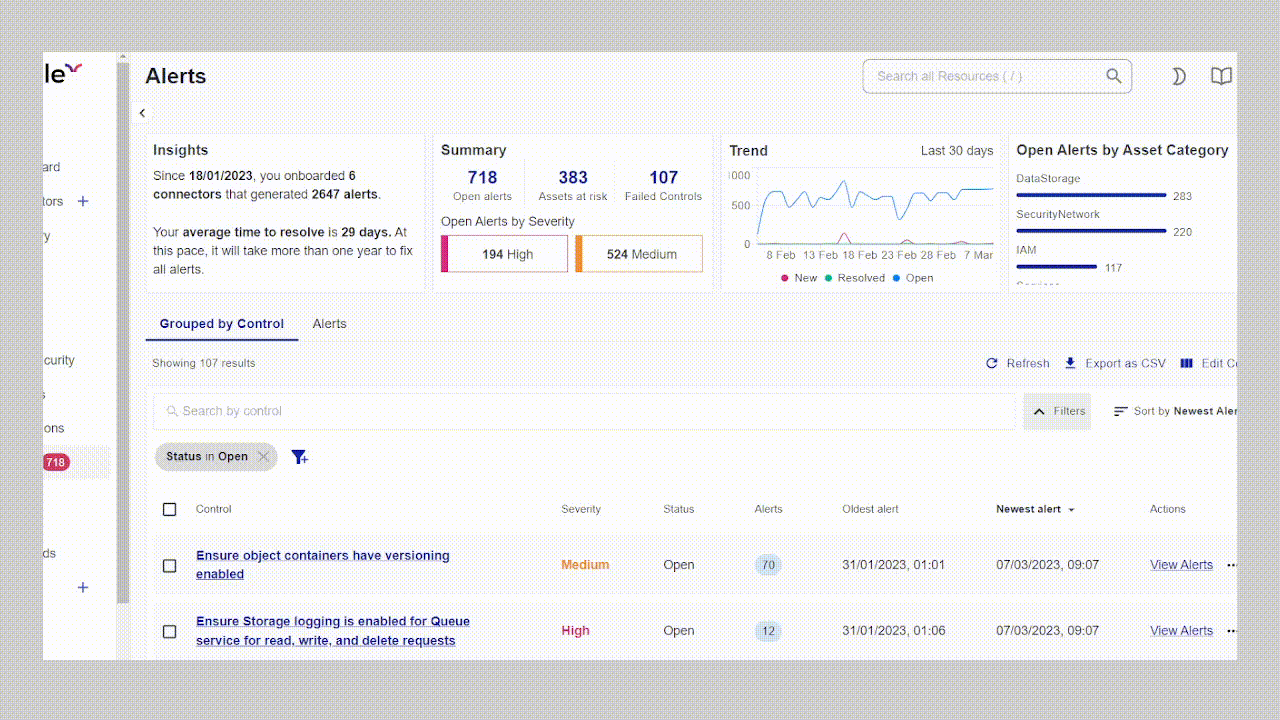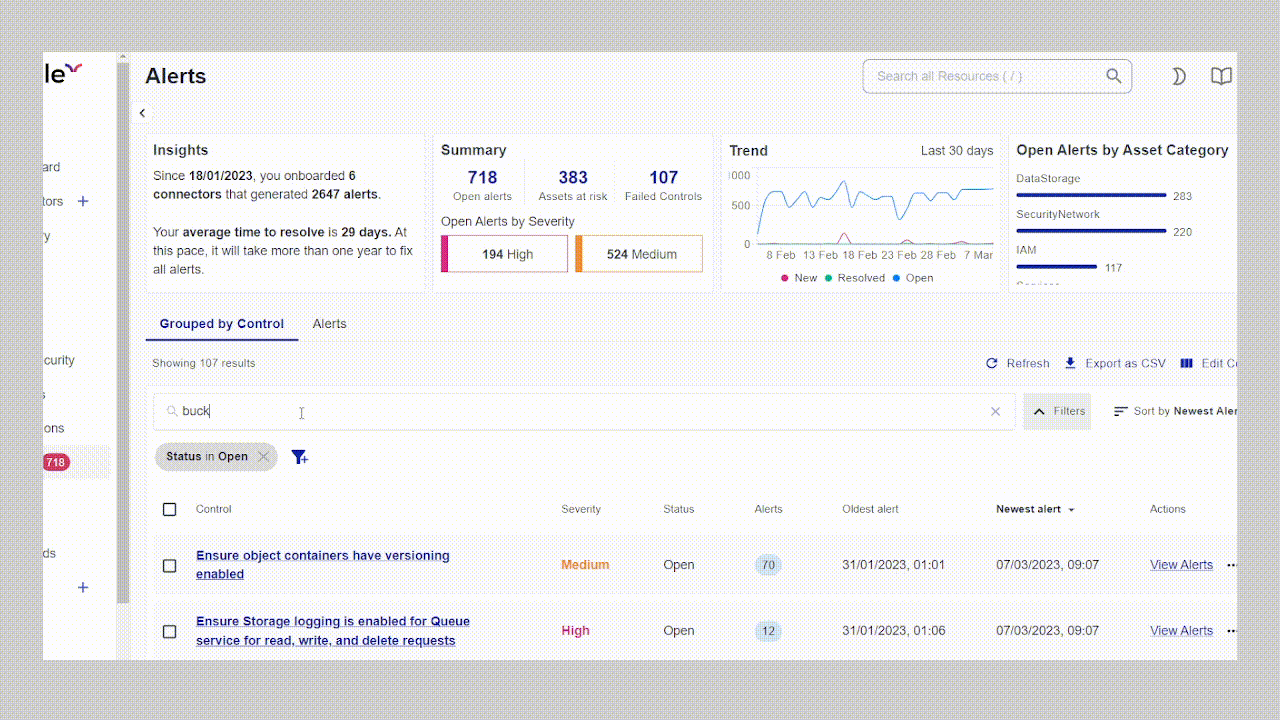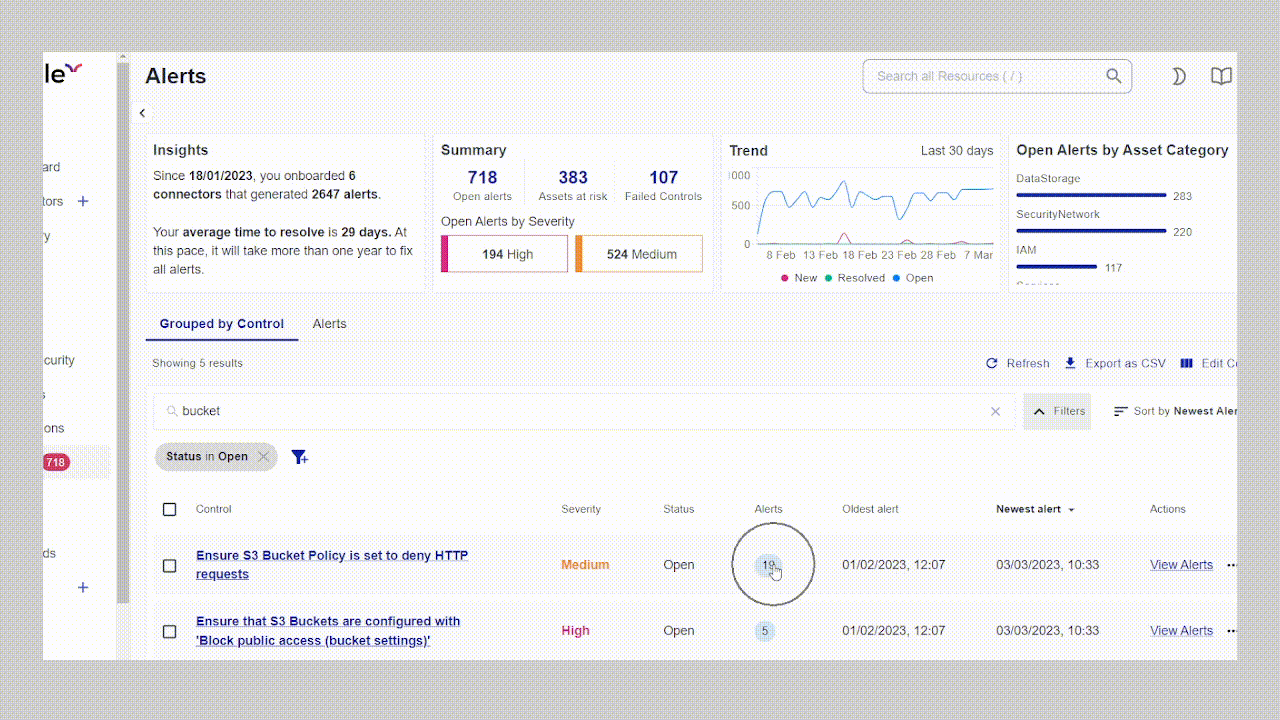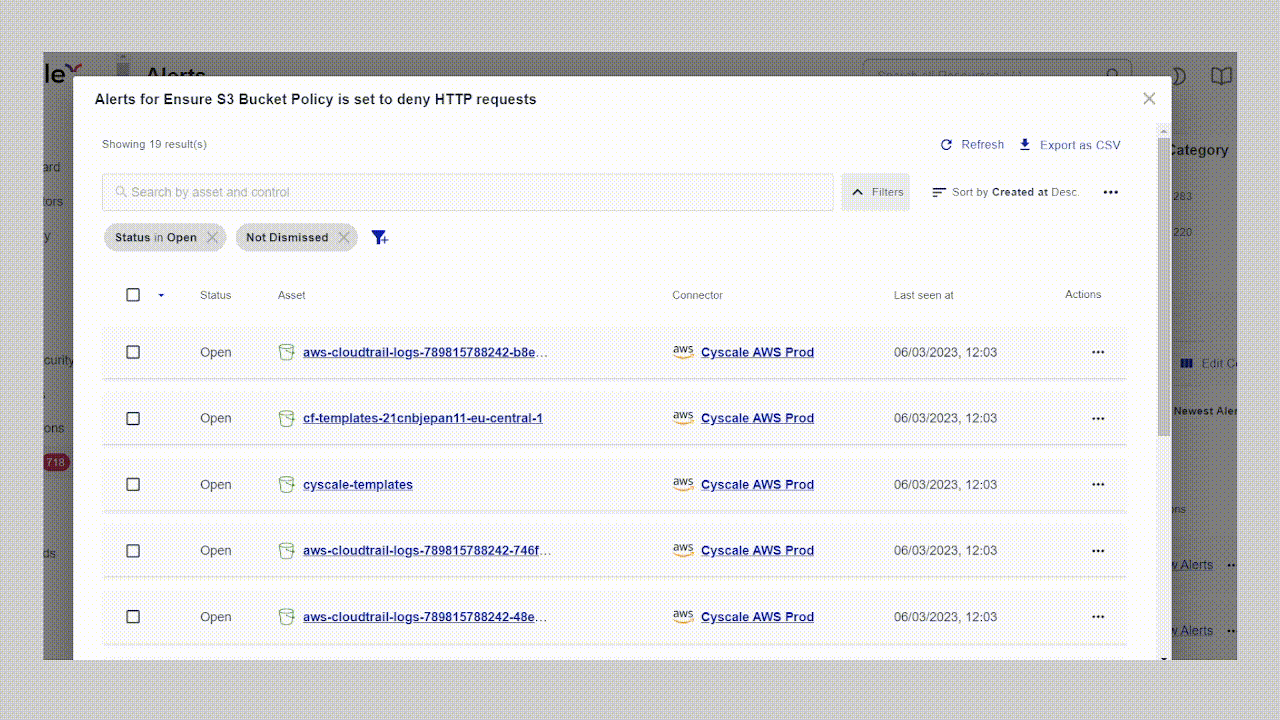
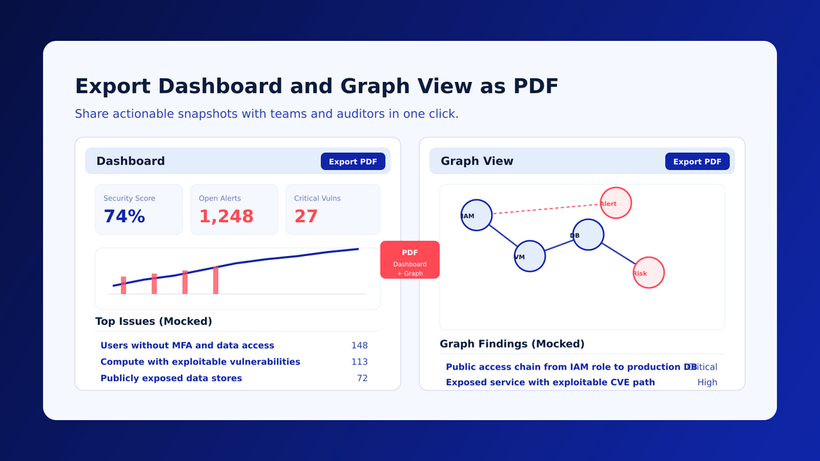
Real-world impact: a customer story
Last year, a mid-sized fintech company approached us after their security team became overwhelmed managing cloud security across AWS and Azure. They were using separate tools for each environment, creating siloed visibility and inconsistent policies.
Within two days of deploying Cyscale, their team discovered a critical exposure: an S3 bucket containing customer financial data was inadvertently accessible through an over-privileged IAM role assigned to a public-facing Lambda function. Their tools had flagged both issues separately, the over-privileged role and the sensitive data, but neither connected the dots to show the actual attack path.
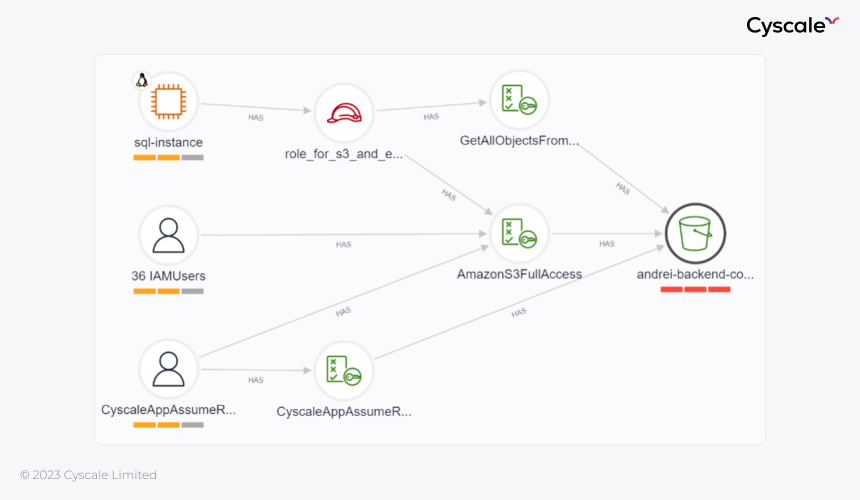
“Before Cyscale, we were drowning in alerts without context,” the cloud team told me. “Now we focus on fixing what matters most: the vulnerabilities attackers could actually exploit to reach our sensitive data”.
Technical Deep-Dive: how Cyscale actually works
For those technically inclined, let me explain how our approach differs architecturally from alternatives like Wiz and Orca:
-
Multi-Dimensional Data Collection
Rather than relying solely on API-based snapshots, we employ a hybrid approach:
- API-based discovery for comprehensive asset inventory - Targeted scanning for vulnerability assessment - where applicable - Configuration analysis for compliance evaluation - Identity and permissions (IAM) mapping for access path analysis - Data classification for sensitivity context, if needed
This multi-dimensional graph approach overcomes the limitations of purely agentless architectures while avoiding the operational overhead of agent-based solutions.
-
The Knowledge Graph Engine
Our graph algorithms don't just store information, they can instantly spot a change. They keep relationships between entities synced in real-time. For example, when evaluating the risk of a vulnerable container, the engine automatically traces:
1. Network access paths to the container 2. IAM permissions granted to the container 3. Data stores accessible from the container 4. Sensitivity classification of accessible data 5. Actual exploit potential based on configuration and CVSS or EPSS scores
This relationship mapping enables true risk-based prioritization. Unlike conventional risk scores based on CVSS alone, our system considers actual attack feasibility and potential impact based on your unique environment.
-
Practical Compliance Automation
Compliance isn’t just about checking boxes, especially if you care about security. It's about verifying security in practice. Our platform automates up to 80% of CIS Benchmark controls across AWS, Azure, and GCP, with contextualized remediation guidance that explains not just what to fix, but how and why.
For a European financial services client, this approach reduced their compliance assessment time from 3 weeks to 2 days, allowing their security team to focus on actual protection rather than documentation.
Looking Forward: the cloud security landscape after Wiz
The Google-Wiz acquisition marks a pivotal moment in cloud security. Having navigated multiple cycles of security market consolidation, I predict several developments:
-
The Return of Multi-Vendor Strategies
Smart security leaders are already revisiting single-vendor approaches. In conversations with CISOs over the past month, I’ve heard growing concerns about vendor lock-in, particularly when the vendor is also a cloud provider. This trend benefits independent security providers like Cyscale who can deliver objective, cross-cloud protection.
-
Context has become the new security currency
The alert fatigue crisis is reaching a breaking point. Organizations can no longer afford to waste security resources investigating false positives and low-priority issues. Solutions that provide genuine context, not just raw findings, will dominate the next wave of cloud security adoption.
-
AI will enhance humans, not replace them
Lacework’s challenges demonstrated the limitations of AI without proper guardrails. The future belongs to solutions that use AI to augment human decision-making rather than attempting to replace it entirely. At Cyscale, our approach has always been “AI-informed, human-verified”, using machine learning to identify patterns while providing security teams the context they need for informed decisions.
Conclusion and why Cyscale is your best path forward
As someone who has spent most of my career in cloud security, from implementing early CSPM solutions for customers like Rolls-Royce, ABB, or Canon, to developing multi-cloud security architectures for regulated industries, I’ve never seen a more critical moment for organizations to reevaluate their cloud security strategies.
The Google-Wiz acquisition creates both uncertainty for existing customers and opportunity for security leaders to implement more resilient, vendor-independent approaches. Cyscale offers exactly what organizations need in this moment: comprehensive protection that works across all major cloud platforms, prioritizes based on actual risk context, and provides clear remediation guidance.
Whether you’re reassessing your current cloud security solution or implementing protection for the first time, I invite you to experience the difference contextual security makes. Visit Cyscale.cloud to see how our Security Knowledge Graph can transform your approach to cloud security.
Further reading
Cloud Storage
Misconfigurations

Build and maintain a strong
Security Program from the start.
Cloud Compliance in
2026: An In-Depth Guide
The whitepaper talks about ISO 27001, SOC 2, PCI-DSS, GDPR, HIPAA.
Download WhitepaperShare this article
CEO & Founder at Cyscale
Ovidiu brings his cybersecurity experience to the table, innovating with AI-powered solutions that address the real-world challenges of cloud security. His approach is focused on providing SaaS companies with the tools they need to navigate the complexities of compliance and grow securely within their regulated environments.
Stay Connected
Receive our latest blog posts and product updates.
TOP ARTICLES
News
Our Compliance toolbox
Check out our compliance platform for cloud-native and cloud-first organizations:

LATEST ARTICLES
What we’re up to

Cyscale on AWS Marketplace Simplifies CNAPP Procurement and Deployment