Cloud Security and Compliance: A Guide for Your Cloud Infrastructure
Cloud Security Analyst at Cyscale
Monday, December 5, 2022

Cloud security and compliance go hand-in-hand. Following cybersecurity best practices automatically improves your compliance scores, while being compliant with international standards demonstrates that your company is preoccupied with data security and makes efforts to secure its cloud computing environments.
In this article, we will look at both cloud security best practices and compliance standards to construct a comprehensive view on how to secure cloud environments and prevent the occurrence of vulnerabilities while addressing the most common industry compliance frameworks.
Cloud security
1. Contextual security
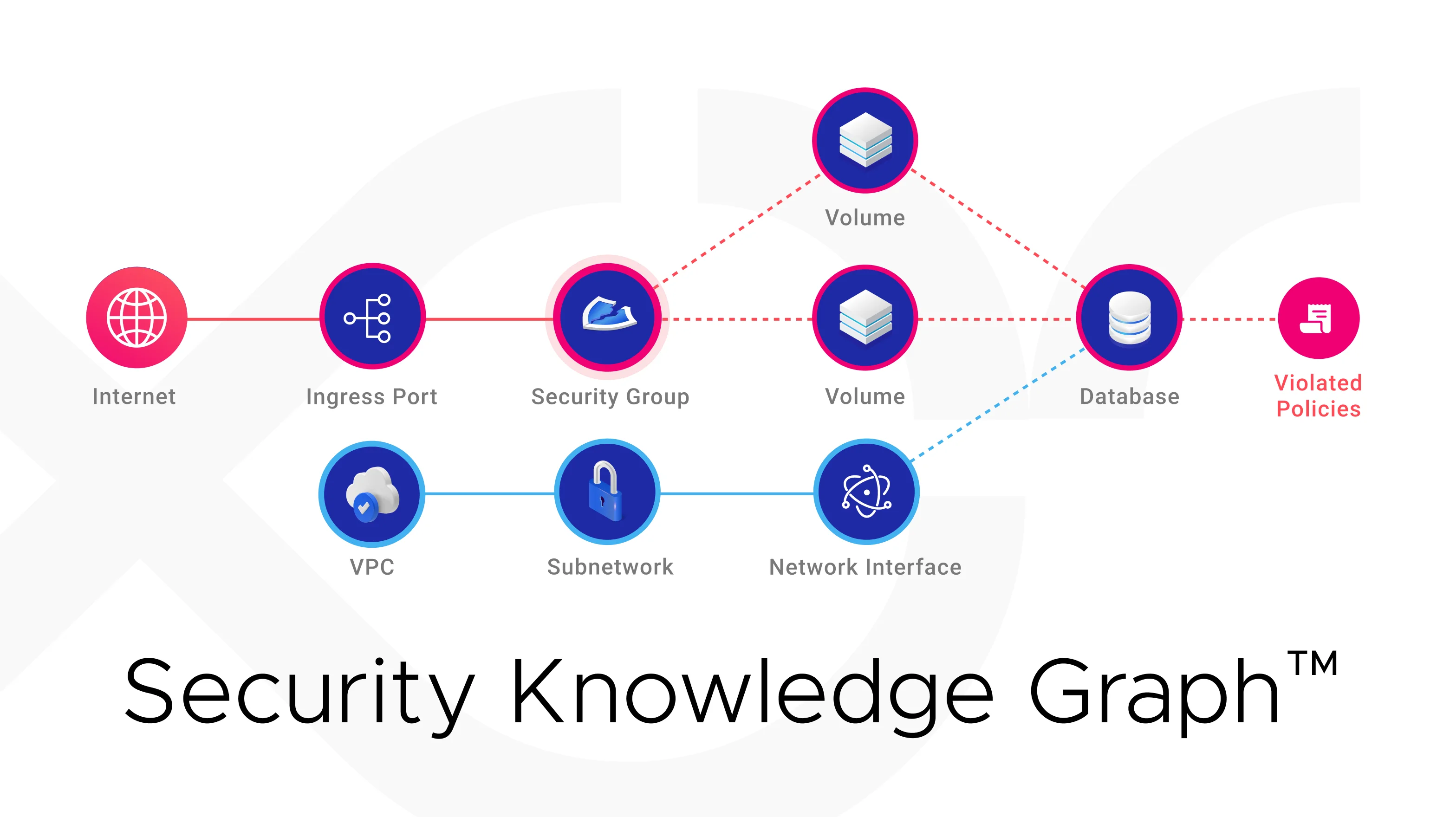
Not often do you see contextual security supporting a security program. However, understanding the consequences of each misconfiguration is an essential step to securing your cloud infrastructure since it can help you prioritize remediation work.
A knowledge graph is the perfect data model to support a contextual security analysis that more accurately indicates risk. Cyscale’s Security Knowledge Graph provides a comprehensive view of your cloud assets and the relations between them.
This all-inclusive graph highlights risk contextually and helps you make better sense of your cloud security posture.
2. IAM
When we think of cloud security, the first thing that comes to our mind is Identity and Access Management (IAM). IAM is described as a set of rules and policies that establish who can access what resources. Authentication and authorization are the security principles that tackle these issues.
Some key configurations you can make to ensure a strong IAM policy are:
- Enable Multi-Factor Authentication (MFA),
- Implement The Principle of Least Privilege for access control,
- Ensure continuous logging and monitoring,
- Rotate credentials and keys regularly, and others.
3. Data encryption
Data encryption is necessary to obtain data confidentiality and protect your assets. Data at rest is the most targeted data, and it can be protected through symmetric encryption. You can encrypt:
- Databases,
- Files,
- Buckets, and others storage assets.
In order to perform correct encryption, ensure that you choose the suitable algorithm (for data at rest, AES is an industry-standard), store your cryptographic keys securely and away from data, rotate the keys you use, and follow other best practices described in this article.
Moreover, encrypt all cloud data traveling to and from your cloud environment using SSL/TLS to prevent any eavesdropping attacks and data breaches..
Compliance
In this article, we will look at some of the most accredited standards:
- ISO 27001, which has been recently updated,
- SOC 2,
- PCI-DSS,
- HIPAA,
- GDPR.
ISO 27001
This standard was developed by ANSI-ASQ National Accreditation Board (ANAB) and defines security best practices for ISMSs (Information Security Management Systems). It contains 93 security controls that specify rules in the following areas:
- People (8 controls),
- Organizational (37 controls),
- Technological (34 controls),
- Physical (14 controls).
After obtaining the accreditation, it has a three-year validity.
The newest version of ISO 27001 was released in October 2022. You can find more details here.
SOC 2
SOC 2 is governed by The American Institute of Certified Public Accountants (AICPA). It also defines security rules for ISMSs, having 64 criteria that need to be fulfilled by a company to obtain this accreditation. They are grouped into five Trust Service Criteria (TSC):
- Security,
- Availability,
- Processing integrity,
- Confidentiality,
- Privacy.
SOC 2 has a one-year validity.
You can find a comprehensive comparison between SOC 2 and ISO 27001 here.
PCI-DSS
Payment Card Industry Data Security Standard (PCI-DSS) is a compliance framework that specifies regulatory compliance requirements regarding credit and debit card transactions performed by a company.
This standard regulates credit card information processing, storage, and transmission.
PCI-DSS contains 12 requirements that ensure a company keeps cardholder data safe. They refer to:
- firewall management,
- encryption of sensitive data,
- the security of applications and technologies,
- the authentication process within a company, and many more.
You can see the entire list, along with explanations, here.
HIPAA
The Health Insurance Portability and Accountability Act of 1996 (HIPAA) is the most well-known standard that regulates the management of individuals’ personal health information (PHI). It is a U.S. healthcare federal law that contains three rules regarding the storage, the management, and the access rights to PHI.
The three rules are:
- The Privacy Rule,
- The Security Rule,
- The Breach Notification Rule.
One aspect of HIPAA is that the consequences of HIPAA violations are not only financial, but also criminal.
GDPR
GDPR (The General Data Protection Regulation) is a security and privacy law drafted and passed by the European Union on May 25, 2018. This law affects anyone that processes EU citizen data, even if they are not from the EU.
Some of the protection principles dictated by GDPR are:
- Lawfulness, fairness and transparency,
- Accountability,
- Data minimization,
- Integrity and confidentiality, and others.
All of these compliance standards have rigorous regulatory requirements, and the consequences of not implementing those rules can lead to financial and criminal repercussions, as well as a damaged reputation.
To read more about these compliance standards, as well as NIST, check out our whitepaper.
Understanding cloud compliance is crucial for organizations that want to ensure both the security and legality of their cloud operations. The constantly changing landscape of regulations demands a comprehensive approach to compliance, aligning with various standards such as ISO 27001, SOC 2, PCI-DSS, HIPAA, and GDPR. To equip yourself with foundational knowledge and practical tips on cloud compliance, read our detailed guide on Cloud Compliance 101: Basics & Best Practices.
Our cloud compliance platform can help you secure your cloud environment and become compliant with respected accreditations through:
- Over 400 controls, across multiple public cloud service providers, such as Microsoft Azure, AWS (Amazon Web Services), and Google Cloud, that help you stay on top of your security program,
- Both pre-configured and editable security policies that can be associated to controls,
- Powerful identity and security dashboards for enhanced visibility over your cloud infrastructure, and others.
Secure your cloud infrastructure effectively with expert insights on cloud security and compliance best practices and international standards. Boost your data safety with our Cloud Security Platform, offering 400+ controls, customizable security policies, and advanced dashboards for ultimate control and visibility.
Cloud Security Analyst at Cyscale
Sabrina Lupsan merges her academic knowledge in Information Security with practical research to analyze and strengthen cloud security. At Cyscale, she leverages her Azure Security Engineer certification and her Master's in Information Security to keep the company's services at the leading edge of cybersecurity developments.
Further reading
Cloud Compliance in
2025: An In-Depth Guide

The whitepaper talks about ISO 27001, SOC 2, PCI-DSS, GDPR, HIPAA.
Download WhitepaperCloud Storage
Misconfigurations
Build and maintain a strong
Security Program from the start.
Share this article
Stay Connected
Receive our latest blog posts and product updates.
TOP ARTICLES
Compliance
Our Compliance toolbox
Check out our compliance platform for cloud-native and cloud-first organizations:

LATEST ARTICLES
What we’re up to

Why the world needs Cyscale in a post-Wiz era





